What is Challenge Handshake Authentication Protocol?
A popular network authentication method for confirming a user’s or host’s identity is the Challenge Handshake Authentication Protocol (CHAP). It is frequently used in conjunction with Point-to-Point Protocol (PPP) connections, like those used for Wide Area Networks (WANs), Virtual Private Networks (VPNs), and dial-up internet access. CHAP is utilized in PPPoE to authenticate DSL users and is also carried by other protocols such as RADIUS and Diameter.
The fundamental idea behind CHAP is that it requires the connecting client, or peer, to demonstrate its identity by offering a particular answer to a special challenge. This challenge-response system is specifically made to guard against replay assaults and stop unwanted access.
Because the password or shared secret is never sent across the network in plaintext, CHAP is typically seen as being more secure than the more antiquated Password Authentication Protocol (PAP).
You can also read Applications of HMAC Hashed Message Authentication Code
How CHAP Works?
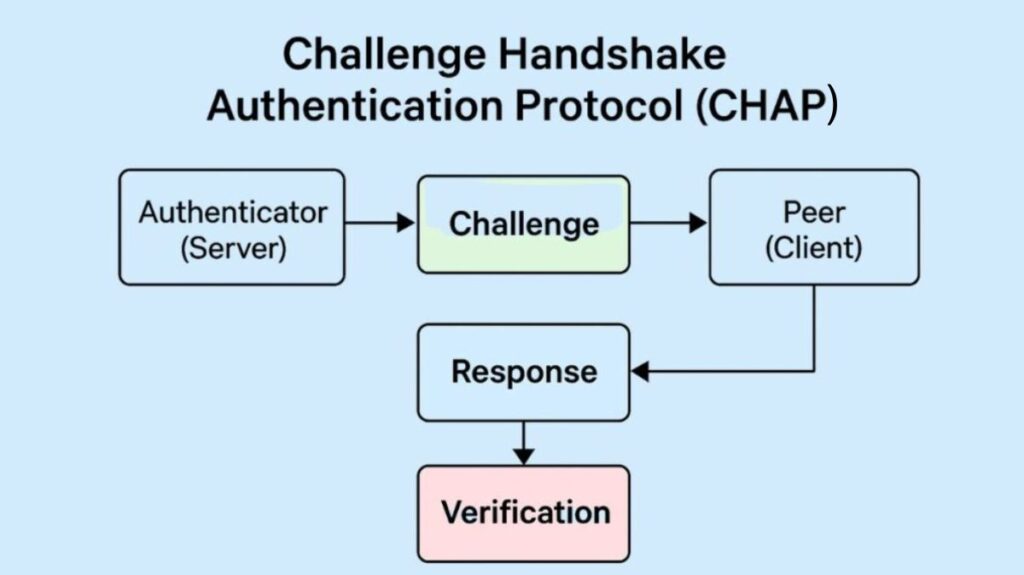
The Three-Step Handshake
CHAP operates using a three-step process, often referred to as a three-way handshake, between the authenticator (typically a router or access server) and the peer (client).
| Step | Initiator | Action | Purpose |
| 1. Challenge | Authenticator (Server) | Sends a Challenge message containing a random value (the challenge string) and a unique ID to the peer. | Ensures the response is unique and not a captured replay. |
| 2. Response | Peer (Client) | Calculates a Response value using a one-way hash function (like MD5) on the concatenation of the ID, the shared secret (password), and the challenge string. Sends this hash back to the authenticator. | Proves knowledge of the shared secret without sending it in plaintext. |
| 3. Verification | Authenticator (Server) | Performs the exact same hash calculation using its own copy of the shared secret, the received ID, and the original challenge. | Compares its calculated hash with the peer’s received response. If they match, the authenticator sends a Success message; otherwise, it sends a Failure and terminates the connection. |
This authentication process happens at the initial startup of the link.
Key Features and Security Profile
Security Advantages
- Protection Against Replay Attacks: Protection Against Replay Attacks: An attacker cannot capture and replay a successful response later because the challenge string (random value) is different and unpredictable for each authentication attempt.
- No Cleartext Password Transmission: The main benefit is that only the computed hash answer is sent over the network, never the shared secret.
- Periodic Verification: To constantly confirm the client’s identity and uphold security, the authenticator may periodically give the client a new challenge during an active session, necessitating a fresh response.
- Widespread Compatibility: CHAP is a flexible option because it is widely supported by a range of networking devices and operating systems, such as Apple OS X and Microsoft Windows.
Limitations
While providing a strong level of security, CHAP has notable limitations:
- Vulnerability to Man-in-the-Middle (MITM) Attacks: CHAP is not built to withstand man-in-the-middle (MITM) attacks, in which a hacker intercepts challenge and response packets and assumes the identity of the client in order to obtain network access.
- Cleartext Secret Storage: The shared secret (password) must be stored in clear-text or a reversible format on both the client and the server in order to carry out the required hash computation. This creates a security risk for password storage “at rest” by prohibiting the usage of irreversibly hashed password databases for the server.
- Vulnerability to Offline Attacks: By comparing guesses to the hash answer that was captured, an attacker can employ an offline dictionary attack or brute-force techniques to crack the shared secret if they are able to intercept the CHAP challenge and response packets.
- No Mutual Authentication: Standard CHAP lacks mutual authentication, which makes the network susceptible to spoofing attacks since the network does not authenticate itself to the user in the same manner that the user authenticates to the network. (Note: One form that permits mutual authentication is MS-CHAP).
- Hash Function Strength: The MD5 hash function, on which the protocol depends, is currently regarded as weak.
You can also read Cisco SNMPv3 Configuration, SNMPv3 security and components
