This article gives an overview of Media Access Control address, it’s Characteristics, Types of MAC Address, it’s advantages and disadvantages.
What is Media Access Control address?
An address is necessary for data transfer or communication between computers. Computer networks use a variety of addresses, each operating at a distinct layer. Operating at the OSI model’s Data Link layer (Layer 2), Media Access Control (MAC) addresses are essential identifiers in local area networks (LANs). They are essential for direct communication between devices in the same network segment.
Core Characteristics of MAC Addresses
Definition and Terminology: A MAC address is a hexadecimal number that indicates a host’s physical location. Because it is burned into the ROM chip on the Network Interface Card (NIC) during manufacturing, it is frequently referred to as a hardware address, physical address, LAN address, or burned-in address (BIA).
Length and Format: 48 bits, or 6 bytes, make up a MAC address. Usually expressed as 12-digit hexadecimal values, they are sometimes accompanied by hyphens (e.g., 00-00-0c-12-34-56) or periods (e.g., 0000.0C12.3456) for readability.
Structure (OUI): In a MAC address, the Organizationally Unique Identifier (OUI) is the first 24 bits (3 bytes or 6 hex digits). This special code is given to manufacturers by the IEEE. To uniquely identify the particular network interface, the manufacturer assigns the remaining 24 bits.
Uniqueness: A universally unique MAC address is assigned to each Ethernet device to avoid misunderstanding and guarantee correct delivery.
You can also read SMB, SMC And SMA Connectors, RCA AND SHV Connectors
Types of MAC Address
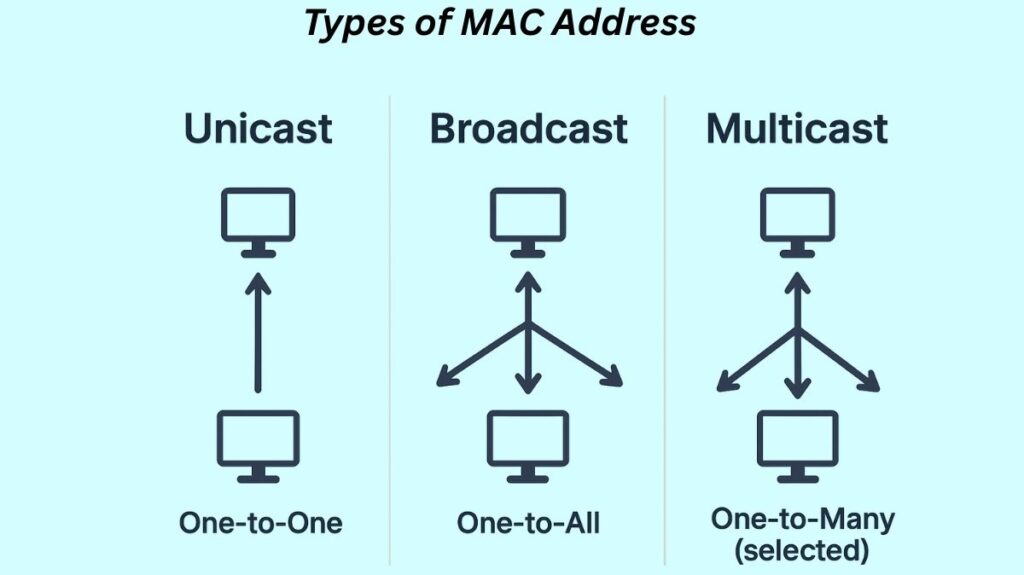
Unicast Address: The interface leading to a particular NIC is the only one to receive a Unicast-addressed frame. Only one receiving NIC is intended to receive a frame if the first octet of an address’s LSB (least significant bit) is set to zero. Unicast is always the source machine’s MAC address.
Broadcast Address: The underlying layer (Data Link Layer) allows broadcasting, much like the Network Layer does. Broadcast addresses (FF-FF-FF-FF-FF) are Ethernet frames that have ones in every bit of the destination address. Frames having the MAC address FF-FF-FF-FF-FF will be received by all of the computers in that LAN segment.
Multicast Address: A group of devices can receive a frame from the source with the multicast address. The first octet of an address’s LSB (least significant bit) is set to one in Layer-2 (Ethernet) Multicast addresses. The address block 01-80-C2-xx-xx-xx (01-80-C2-00-00-00 to 01-80-C2-FF-FF-FF) has been set aside by IEEE for group addresses that are used by standard protocols.
Role of MAC Addresses in LAN Switching
MAC addresses are the primary means by which switches, which are Layer 2 devices, function.
MAC Address Table (CAM Table): RAM is used by switches to create and manage a MAC address table, also known as a switching table, bridging table, or content-addressable memory (CAM) table. MAC addresses are mapped to the particular ports that they were learnt on in this table.
MAC Learning (Address Learning): This is the second primary purpose of the switch (as mentioned in the previous turn). Upon receiving a frame, a switch looks at the incoming frame’s source MAC address. The switch then enters the port on which it was received together with the source MAC address into its MAC address table. If no frames are observed from that MAC address for a predetermined “ageing time” (which, on most switches, is 300 seconds or five minutes by default), entries are deleted. This procedure is dynamic.
Forwarding and Filtering: After populating the MAC address table, the switch decides whether to forward or filter incoming frames based on the destination MAC address.
- Known Unicast: Only the particular port linked to the destination MAC address is sent by the switch if it is present in the table.
- Unknown Unicast/Broadcast/Multicast: Except for the interface on which it was received, the switch floods the frame out of all interfaces in the same VLAN if the destination MAC address is broadcast or multicast, or if it is not in the table (unknown unicast). When the destination reacts to this flooding, the switch is able to determine its MAC address.
Loop Avoidance: Additionally, switches employ Spanning Tree Protocol (STP) to establish a loop-free environment in switched LANs, preventing broadcast storms and MAC address table instability that may result from duplicated connections. STP makes use of Bridge IDs (BIDs), which are made up of the switch’s MAC address and a priority field.
MAC Addresses in Related Protocols and Features
Address Resolution Protocol (ARP): ARP converts a known IP address on a local network to an unknown MAC address. When a host needs to resolve an IP address to a MAC address, it first looks in its ARP cache and then sends an ARP broadcast request if it can’t find it.
IPv6 EUI-64 Format: In IPv6, the 64-bit interface ID is formed using MAC addresses using the EUI-64 format, especially for stateless address autoconfiguration (SLAAC). This entails dividing the 48-bit MAC address into two 3-byte parts, inverting the first byte’s seventh bit, and placing FFFE in the middle.
Port Security: This functionality identifies devices and limits access to switch ports using the source MAC addresses of Ethernet messages. It has the ability to define violation actions such as restrict or shutdown, as well as limit the maximum amount of MAC addresses that can be learnt on a port. Sticky MAC addresses are MAC addresses that are learnt dynamically and then saved as static entries in the running configuration of the switch. This makes the MAC address permanent even after reboots.
DHCP Snooping and Dynamic ARP Inspection (DAI): For validation, these security measures rely on MAC addresses. In order to determine whether the client hardware address (chaddr) in the DHCP message and the source MAC address in the Ethernet header match, DHCP Snooping is used. DAI prevents spoofing by comparing the MAC and IP addresses of the origin of ARP messages to a DHCP Snooping binding table.
HSRP (Hot Standby Router Protocol): The last eight bits of a well-known virtual MAC address are used by HSRP to signify the HSRP group number.
Wireless Networks: Additionally, wireless devices communicate over the air using Layer 2 using distinct MAC addresses. The wireless MAC address of an Access Point (AP) is usually used to generate its Basic Service Set Identifier (BSSID).
MAC Addresses in Routing
Distinguishing between MAC and IP addresses is crucial. IP addresses are logical identifiers at Layer 3, whereas MAC addresses are physical identities that function at Layer 2. A router’s interface is never traversed by MAC addresses, which are local to a LAN segment. Although the MAC addresses of packets vary with each hop as they travel between routers, the packet’s source and destination IP addresses usually stay the same. When a host needs to send data to a distant network, it uses the router’s MAC address to send the frame to its default gateway.
You can also read How To Set Up A LAN Network Devices Connection Guidelines
Verification Commands
MAC address tables can be viewed and managed by network engineers using the following commands:
show mac address-tableorshow mac address-table dynamicdisplays dynamically learned MAC addresses.show mac address-table interface <type number>shows MAC addresses on a specific interface.show mac address-table aging-timedisplays the global aging time for MAC entries.clear mac-address-table dynamiccan reset the table for learned MAC addresses.
Advantages of MAC Address
Uniqueness: Because each MAC address is distinct, network devices are simple to identify and control.
Simplicity: Without the need for extra network equipment, MAC addresses are simple to set up and maintain.
Compatibility: MAC addresses are compatible with a wide range of systems due to their widespread use and support by numerous networking technologies and protocols.
Security: MAC addresses can be used to limit network access by limiting connections to devices that have been granted permission to use them.
Fault-tolerance: If a device’s MAC address matches that of the old one, it is simple to replace it in the event of a hardware or software malfunction without impacting the network.
Multicasting: Multicasting is a technique that uses MAC addresses to send a single packet to several devices simultaneously.
Efficiency: Devices can rapidly and readily identify and communicate with one another thanks to MAC addresses, which facilitate effective network connectivity.
Lower network overhead: By eliminating the need for extra routing or addressing, MAC addresses enable devices to interact directly with one another, lowering network overhead.
Ease of troubleshooting: By locating the issue’s origin and monitoring network activity, MAC addresses can be used to troubleshoot network problems.
Flexibility: Network topologies and configurations that can be supported by MAC addresses include client-server, peer-to-peer, and hybrid models.
Disadvantages of MAC Address
Limited address space: Since MAC addresses are 48-bit values, the number of viable MAC addresses is limited. Address conflicts may result if several devices share a MAC address.
Spoofing: Because MAC addresses are so easily spoofable, unauthorized devices can connect to the network.
Inefficiency: The lack of hierarchy in MAC addresses might make managing big networks challenging.
Static addressing: MAC addresses are usually allocated during manufacturing and are difficult to modify. This could be a drawback when equipment need to be changed or adjusted.
Limited scope: Devices outside of a local network segment cannot be identified using MAC addresses; they are only used to identify devices inside that segment.
Hardware-dependent: A device’s MAC address is linked to its network interface card (NIC), therefore if the NIC malfunctions or is replaced, the MAC address also changes.
Lack of encryption: Due to their plaintext transmission, MAC addresses are susceptible to eavesdropping and interception.
No inherent security: Although MAC filtering can be used to limit network access, MAC addresses by themselves don’t offer any built-in security measures.
MAC address collisions: MAC addresses occasionally clash, which can disrupt networks and make it challenging to locate and control networked devices.
You can also read Triax Cable Connector, SMP Connector, Twinax Cable Connector
