Extended Access Control List (ACL)
With much more flexibility than a Standard Access Control List (ACL), the Extended Access Control List (ACL) is a very versatile and detailed method for filtering network traffic according to a variety of criteria contained in the packet headers.
Certain packets passing via a router or going to and from a router (such as traffic to/from VTY lines) can be filtered or allowed using extended ACLs. They are thought to be essential for controlling traffic flow and putting security measures into action.
Functionality and Filtering Criteria
Compared to conventional ACLs, extended ACLs are far more robust since they examine various fields inside the Layer 3 (Network) and Layer 4 (Transport) headers.
Important Parameters for Matching:
- Source IP Address: Uses the originating IP address to filter.
- Destination IP Address: Filters according to the IP address of the intended receiver.
- Protocol Type: Filters according to particular protocols at the network layer, like:
- IP (all packets of IPv4).
- Transmission Control Protocol (TCP).
- User Datagram Protocol, or UDP.
- Internet Control Messaging Protocol, or ICMP.
- Additional protocols, such as PIM, ESP, AHP, GRE, OSPF, and EIGRP.
- Port Numbers: Filters according to certain TCP or UDP source and destination ports at the transport layer. Filtering by application or service is made possible by this feature (e.g., blocking FTP or Telnet but permitting HTTP).
- TCP Flags/Operators: Additional options are available when TCP is provided, such as using the established keyword to only permit communication to pass if it is a part of an existing connection (e.g., has the ACK bit set). Operators such as eq (equal to), neq (not equal to), lt (less than), and gt (greater than) can be used in port number comparisons.
Matching Logic: In order for a rule to be applied to a single Access Control Entry (ACE) inside an extended ACL, all matching parameters must match the packet.
Types and Identification
Names or numbers can be used to identify extended ACLs.
| Type | Range/Format | Key Feature |
|---|---|---|
| Numbered (IPv4) | Primary Range: 100 to 199 | Uses numbers for identification. Traditionally requires deleting and reconfiguring the entire list to edit a single entry. |
| Expanded Numbered (IPv4) | Expanded Range: 2000 to 2699 | Provides additional numbers for extended lists. |
| Named (IPv4 and IPv6) | Uses a descriptive alphanumeric name | Allows for deleting, inserting, or editing individual statements (Access Control Entries or ACEs) using sequence numbers. Must be used when configuring IPv6 ACLs. |
Also Read About CISCO LLDP Link Layer Discovery Protocol Advantages, Types
Placement Suggestions
To optimise performance and accomplish the desired filtering objective, Cisco highly advises positioning Extended ACLs in a particular area.
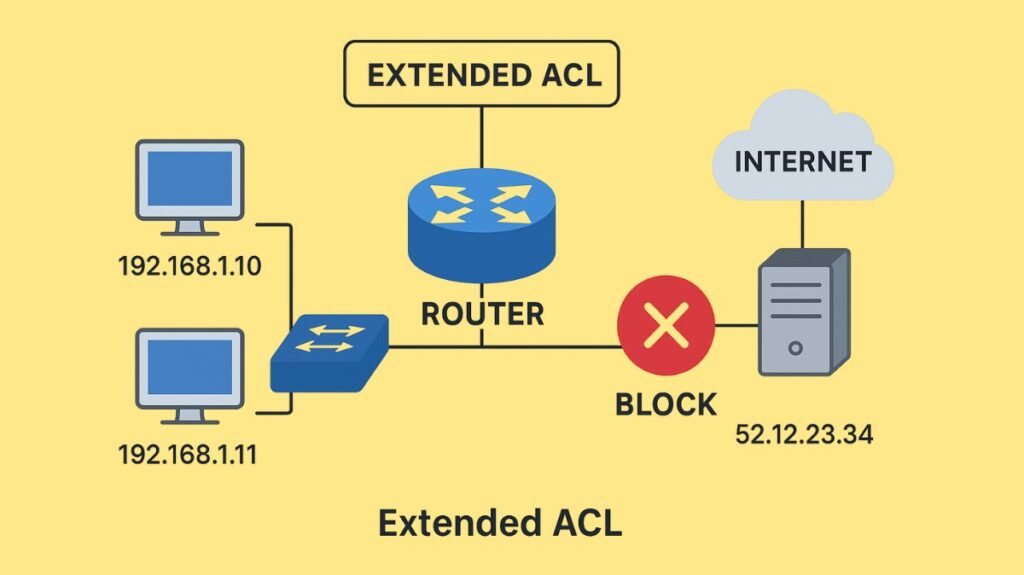
- Rule: If you want to filter or deny traffic, you should position extended ACLs as close to the source as you can.
- The router can discard undesired packets early by placing the ACL close to the source. This saves bandwidth and resources that would otherwise be used to carry the packet across the network before it is denied later on.
- Exclusions: While the rule is usually “closest to the source,” there are instances when an Extended ACL needs to be positioned closer to the destination if doing so is required to properly execute a particular policy requirement, like blocking traffic from accessing only particular networks or services while permitting access to others.
Configuration Syntax Overview (IPv4 Numbered)
The access-list global configuration command is used by extended numbered ACLs to specify the necessary protocol, source, and destination details.
Generic syntax needs:
access-list access-list-number {deny | permit} protocol source source-wildcard destination destination-wildcard [options]
The following are essential syntax requirements:
- Either the 2000–2699 or the 100–199 extended ranges must contain the list number.
- It is necessary to declare the protocol term (such as ip, tcp, or udp) directly.
- The host keyword must be used before the address when matching a single, specific host IP address; the IP address cannot be listed by itself.
Also Read About Types Of Access Control List ACL In Networking & RBAC Vs ACL
Configuration Commands (Cisco IOS Example): Two steps are typically involved in the configuration process:
- Define the ACL: Create the access list using the
access-listcommand (orip access-list extendedfor named lists) and define the permit/deny statements:(config)# access-list NUMBER permit|deny IP_PROTOCOL SOURCE_ADDRESS WILDCARD_MASK [PROTOCOL_INFORMATION] DESTINATION_ADDRESS WILDCARD_MASK PROTOCOL_INFORMATIONFor example, permitting specific TCP traffic to a web server port 80:R1(config)#access-list 100 permit tcp 10.0.0.2 0.0.0.0 192.168.0.1 0.0.0.0 eq 80
- Apply the ACL to an interface: Attach the ACL to the desired interface and direction:
(config-if)# ip access-group ACL_NUMBER in | outFor example, applying ACL 100 inbound to interface F0/0:R1(config)#int f0/0 R1(config-if)#ip access-group 100 in
Implicit Deny Rule: An important idea is that there is an implicit “deny all” declaration at the very end of every access list. This implies that traffic will be rejected if it does not specifically match any permit statement in the list. Consequently, at least one permission entry is required for an access list to be considered valid.
Extended ACLs for IPv6
ACLs for IPv6 are always set up as named ACLs.
- Extended IPv6 ACLs can match on a variety of IPv6 packet header fields, among other things. This comprises IPv6 extension headers, TCP, UDP, ICMPv6 packets, and source and destination IPv6 addresses.
- Limitations: Using application layer data, like a URL or filename for FTP transfers, Extended ACLs (both IPv4 and IPv6) are unable to inspect or filter.
- IPv6 ACLs feature three implied statements at the bottom: two necessary permit icmp statements for Neighbor Discovery (ND) and a final deny ipv6 any any. This is in contrast to IPv4 ACLs, which only have one implicit deny ip any any statement.
Operation Logic
Extended lists function according to three basic rules, much like other ACLs:
- Sequential Order: Beginning with the first line and working down, packets are compared to the list assertions.
- First Match Logic: The router performs the specified action (permit or deny) once a packet matches a statement, ends list processing, and advances to the next packet.
- Implicit Deny: An unseen deny at the conclusion of each ACL follows any sentence. This implicit rule discards a packet if it does not match any explicit permit or refuse instructions. Therefore, in order to permit traffic to pass, an ACL needs to have at least one explicit permit statement.
Advantages and disadvantages
Advantages of extended ACL
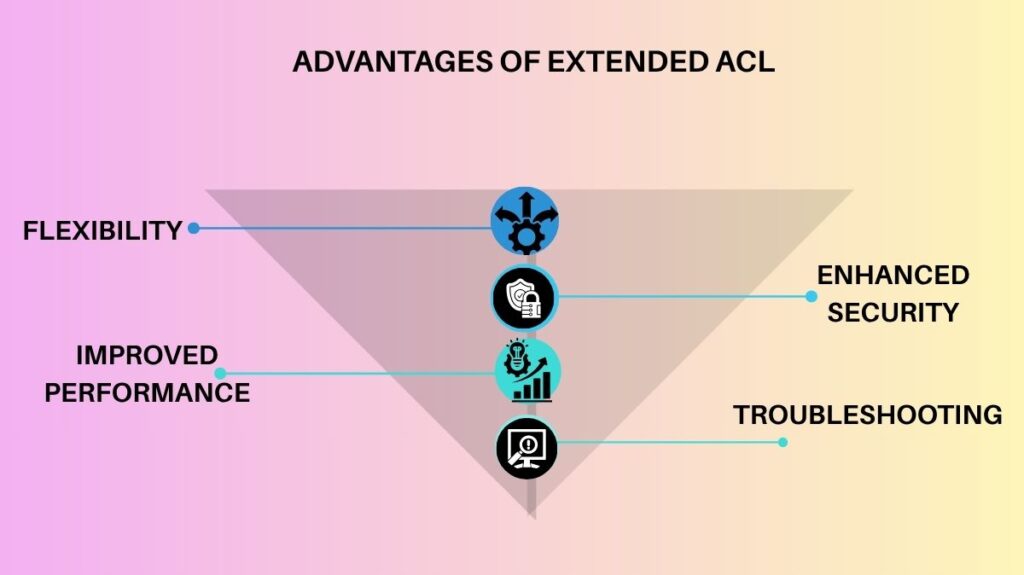
- Granular Control and Flexibility: Adopts complicated security rules by enabling administrators to define precisely which traffic is permitted or prohibited depending on a variety of parameters (source/destination IP, protocol, and ports).
- Enhanced Security: By filtering particular protocols and ports, enhanced security better prevents undesired or malicious traffic, protecting the network from malevolent attackers.
- Improved Performance: Increases network efficiency by reducing superfluous traffic by deleting undesired packets closer to the source.
- Troubleshooting: By determining which ports and protocols a server is accepting connections on, network administrators may swiftly fix problems.
Disadvantages of extended ACL
- Complexity: Compared to ordinary ACLs, extended ACLs are typically more challenging to set up and manage.
- Resource-intensive: Compared to ordinary access lists, they take longer for the processor to evaluate.
- Knowledge Needed: A thorough understanding of network architecture and the several networking protocols (TCP, UDP) is necessary for configuration. They also need to be updated and examined on a frequent basis.
Also Read About Cisco IOS NetFlow Configuration Guide, Uses, And Types
Standard vs Extended ACLs
| Feature | Standard ACL | Extended ACL |
| Filtering Criteria | Source IP address only. | Source IP address, Destination IP address, Protocol type (e.g., TCP, UDP, ICMP), Source and Destination Ports (for TCP/UDP). |
| Control Granularity | Low. Permits or denies the entire protocol suite (all services) to or from a network/host. | High. Permits or denies specific protocols or services (e.g., allow HTTP but deny FTP). |
| Numbered Range (Cisco IOS) | 1–99 and 1300–1999. | 100–199 and 2000–2699. |
| Recommended Placement | Close to the Destination. Placed near the destination network because its filtering is broad (source IP only). Placing it too close to the source could block all traffic (even legitimate) to all destinations. | Close to the Source. Placed near the source of the traffic being filtered to prevent unwanted traffic from crossing the entire network infrastructure, saving bandwidth and router resources. |
| Complexity | Simple configuration. | More complex configuration due to the additional parameters. |
