History Based Access Control (HBAC)
By analysing the current history of a user’s previous actions, including the content they have requested or the order in which they have taken them, History-Based Access Control (HBAC) decides whether to allow or prohibit access to a resource. In contrast to more conventional permission-based models, this paradigm offers a dynamic, stateful view of permissions, allowing rights to be gradually decreased based on user history.
HBAC takes into account a user’s past actions when determining whether they are allowed to do the subsequent action, in contrast to conventional approaches that only take into account current qualities (like ABAC) or roles (like RBAC).
Also Read About NAC Use Cases And How Does Network Access Control Work
Core Concept and Characteristics
The basic tenet of HBAC is that historical behaviour might offer important information about possible danger or reliability, which can then affect whether access should be allowed or prohibited in the present.
Important traits consist of:
- Stateful View: HBAC employs a stateful view of permissions, which means that depending on a user’s past behaviour and the order in which actions are carried out, their access rights may alter or even decline over time.
- Dynamic and Contextual: Because they rely on the particular order of a user’s previous activities and system interactions, access decisions are both dynamic and contextual.
- Increasing Security: HBAC frequently adds an extra degree of adaptive security to existing access control techniques. In a more comprehensive Identity and Access Management (IAM) solution, it might cooperate with ABAC or RBAC.
- Scope: HBAC can be used to safeguard both the caller, or entity requesting access, and the callee, or entity supplying the resource.
How HBAC Works
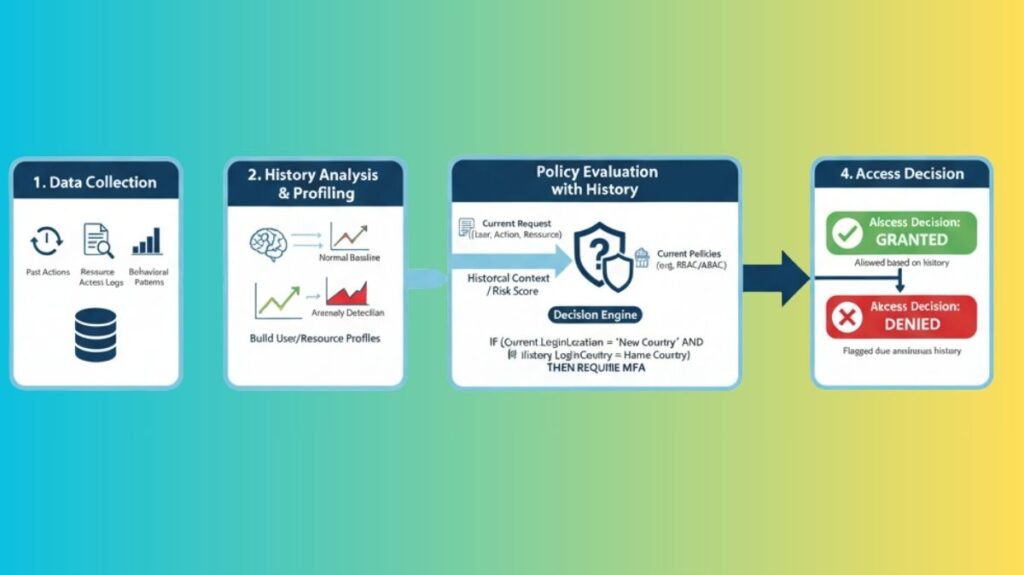
Typically, HBAC systems adhere to a methodical procedure that includes ongoing observation and real-time assessment:
Data Collection/History Collection
Large volumes of data about user activity, system events, and resource use patterns are continuously gathered and logged by the system. This history contains information like:
- Past login attempts, both successful and unsuccessful.
- Historical resource access (which files, when, and from where were accessed).
- Data transfer volume and frequency.
- Modifications to user permissions or roles.
- The precise order in which everything were done.
Also Read About How ABACs Work & Attribute Based Access Control Components
History Analysis/Profiling
A historical profile of users, resources, or particular actions is created by analysing the data that was gathered. This analysis includes:
- Establishing a standard of “normal” conduct.
- Recognising typical access trends.
- Assessing risk based on past events (such as many failed login attempts or private data access outside of office hours).
Policy Evaluation with History
The system analyses an access request against current rules, roles, and attributes based on the user’s historical profile.
Access Decision
Access is either given, denied, or allowed with extra constraints (such read-only access or multi-factor authentication) based on the previous context and the present request.
Examples of HBAC in Action
Complex conditional and risk-based access controls are implemented using HBAC:
- Conditional entry: “If the user has tried to log in unsuccessfully 5 times in the last hour, DENY access, even if the current password is correct” .
- Risk-Based Access: The system may demand multi-factor authentication (MFA) or deny access completely if a user tries to access sensitive data from a new, untrusted IP address and their history indicates they only access sensitive data from corporate IPs.
- Workflow Security (Banking): A rule stating that a user “cannot transfer funds unless they previously logged in with multi-factor authentication” may be part of the banking workflow security policy.
- Insider Threat Monitoring: If a user unexpectedly downloads several private files in a short period of time, which is very different from their usual behaviour, the system may prevent additional downloads.
- Banking Systems: Unless a user has already logged in using multi-factor authentication, they are unable to transfer funds.
- Workflow Systems: If a reviewer generated a document, they cannot approve it.
- Security Monitoring: The system prevents additional downloads if a user downloads several private files quickly.
Use Cases of HBAC
HBAC is especially helpful in settings where security must be flexible and responsive to changing user behaviour or threats.
- Fraud detection is the process of using past financial behaviour to identify odd transaction trends.
- Employees who suddenly begin accessing extremely sensitive information they didn’t previously need should be flagged for insider threat detection, particularly following a poor performance assessment.
- Adaptive security is the process of modifying access permissions in response to past events and the perceived risk level of a user’s current session.
- If a user’s access pattern differs substantially from their previous norm, such as logging in from an odd geographic location after a prolonged period of inactivity, compromised account detection may be used to deny access or require re-authentication.
- Providing audit trails and proof of access decisions based on past data is known as compliance.
Advantages of HBAC
- Beyond static standards, enhanced security offers a more proactive and flexible layer of protection.
- Contextual awareness: By taking into account not only the present but also the entire past, it enables more informed access decisions.
- Risk mitigation: By seeing unusual activity, it assists in identifying and stopping possible fraud, security breaches, and resource abuse.
- Decreased False Positives/Negatives: By comprehending typical user behaviour variances, access judgements can be improved.
Disadvantages of HBAC
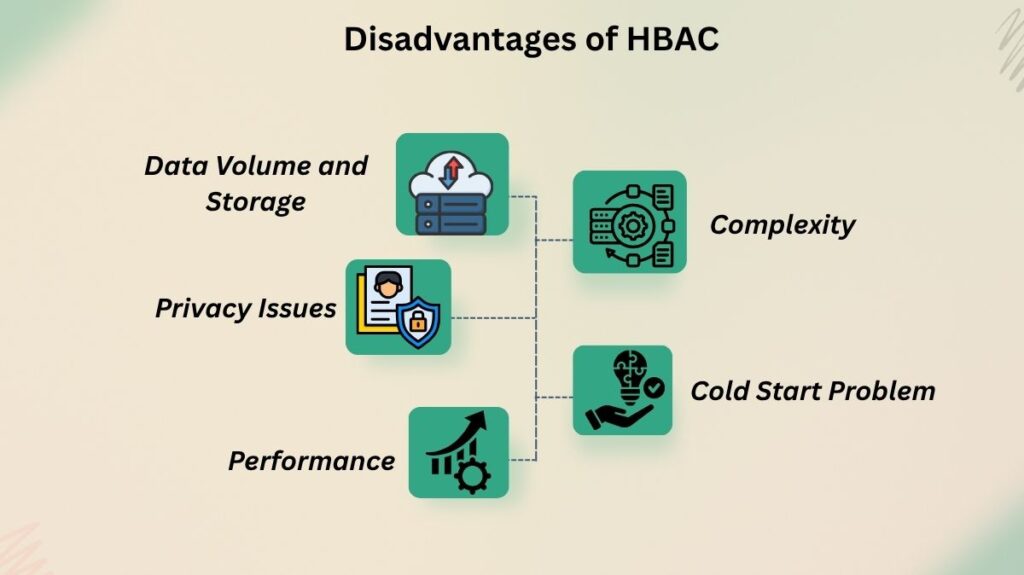
Notwithstanding its benefits, there are a number of challenges in putting HBAC into practice:
- Data Volume and Storage: In order to continuously gather and examine the enormous volumes of historical data, HBAC needs a significant amount of processing power and storage.
- Complexity: Creating efficient historical profiles and policies can be difficult to handle and frequently calls for complex algorithms.
- Privacy Issues: There are serious privacy issues brought up by the requirement to gather a large amount of user history.
- “Cold Start” Problem: Until a profile can be created, first HBAC judgements are less informed for new users or resources since they lack past data.
- Performance: When making access decisions, real-time analysis of past data may result in latency.
Also Read About Advantages And Disadvantages Of RBAC & Types Of RBAC
