We covered the following topics in this blog: the Business Email Compromise (BEC) assault, how it works, common types of BEC scams, the effectiveness of BEC attacks & their effects, and how can you prevent a BEC attack .
Business Email Compromise (BEC)
A sophisticated kind of malware and exploit known as business email compromise (BEC) targets companies and organisations, frequently those that have suppliers located overseas or undertake wire transfers. Because BEC attacks are more focused, customized, and carefully thought out than regular, mass phishing emails, they are typically more difficult to identify.
The main objective of a BEC scammer is to defraud the business by fooling an employee into sending funds or private information to an account under the attacker’s control, typically by posing as a reputable vendor or a trusted authority figure.
Also Read About Advantages And Disadvantages Of Malware & Types Of Malware
How BEC Attack Works?
Instead than depending on malicious links or attachments that security software could detect, BEC attacks frequently use a type of pretexting and social engineering to take advantage of people’s confidence.
Usually, the attack consists of the following steps:
Reconnaissance/Research
The attacker identifies important people (such as the CEO, CFO, or finance staff) and learns about internal company processes and communication styles by conducting in-depth research on the target organisation using publicly accessible information (such as social media or the company website).
Impersonation
The attacker either creates a phoney email address that closely resembles a valid one(e.g., ceo@cornpany.com instead of ceo@company.com) or takes control of a legitimate firm email account (Account Compromise).
Deception/The Deceptive Request
An employee, usually in the finance department, receives an email that appears authentic but is actually sent from the compromised or spoof account. The email makes a high-value, urgent request that looks real but is completely fake. By depending on a feeling of urgency, authority, or confidentiality, the request frequently takes advantage of the recipient’s confidence.
Execution and Payoff
The victim complies without checking the information because they think the request is sincere and urgent. They move the money or private information, which instantly ends up in an account that the attacker controls. Money laundering strategies can make it extremely impossible to retrieve the monies if the scam is not discovered quickly.
Types of BEC attacks
BEC offenders frequently employ a number of unique message archetypes:
- CEO Fraud (or Whaling): CEO fraud, also known as whaling, is when a hacker poses as the CEO or another senior executive and sends a pressing email telling a worker to start a wire transfer for an urgent payment or a purportedly private business transaction.
- Vendor Invoice Scam (False Invoice Scheme): The attacker poses as a well-known supplier or vendor and sends a phoney invoice with new, fictitious bank account information for payment, stating that the vendor’s bank has changed.
- Data Theft/Request: To get private employee information, such as W-2 forms, payroll data, or personally identifying information (PII), which may be used in future assaults or identity theft, the scammer poses as an HR or IT leader.
- Attorney Impersonation: At the end of the workday, the fraudster often puts pressure on lower-level employees by posing as a lawyer or legal representative for the firm and asking for a speedy wire transfer for a private legal concern.
- Payroll Diversion: In order to divert employees’ pay cheques, fraudsters deceive HR or staff into altering salary deposit information.
- Account Compromise (AC): This happens when an attacker uses credentials that have been stolen to obtain unauthorised access to a legitimate executive or staff email account. The attacker then uses the legitimate account to send phoney requests to internal contacts.
Also Read About Examples of Social Engineering Attacks And How it Works
Why BEC Attacks Are Effective and Their Impact
Because they imitate regular company processes and frequently get past technical defences because they don’t use malware, BEC attacks are very effective. Artificial intelligence (AI) developments are also making it possible for attackers to create more individualised and convincing emails, making detection more challenging.
Organisations are severely impacted by BEC, which results in large financial losses (the FBI recorded losses of over USD $50 billion since 2013). BEC can lead to business disruptions, regulatory and legal fines, data breaches, and reputational harm in addition to the stolen money.
Finance staff, executives (CEOs, CFOs), HR specialists, IT administrators, and new or entry-level staff members who might not be familiar with communication standards are among the frequently targeted groups.
How can you prevent a bec attack
Advanced technical solutions, staff training, and procedural controls are all necessary for an effective defence against BEC.
Also Read About Email Phishing Attacks, Why Do Hackers Use Phishing Emails?
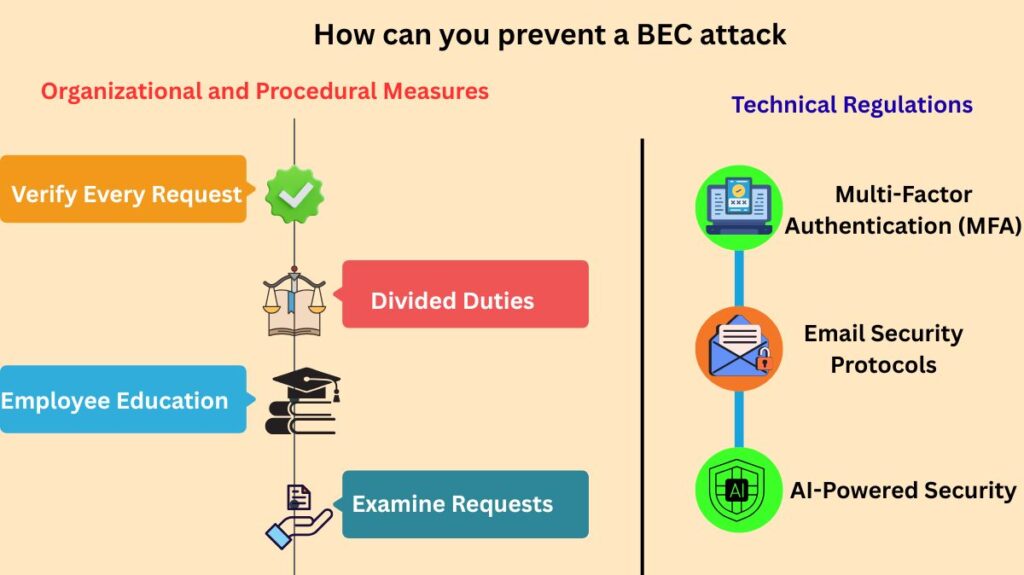
Organizational and Procedural Measures
- Verify Every Request: Make sure that every wire transfer and data request is subject to a stringent two-factor verification procedure. This should use out-of-band verification, which entails never using the contact details in the dubious email and instead confirming the request by phoning the sender at a known, reliable phone number.
- Divided Duties: Put in place a rule that requires two or more workers to give their approval for significant financial transactions.
- Employee Education: To assist employees in identifying BEC warning signs, such as odd phrasing, a sense of urgency, or requests to update banking information, regularly conduct cybersecurity awareness training.
- Examine Requests: Pay close attention to all email requests for money transfers to see if they seem unusual. When the “reply” email address is different from the “from” address displayed, internal security rules have the ability to flag the communication.
Technical Regulations
- Multi-Factor Authentication (MFA): To add an additional degree of protection and make it more difficult for an attacker to obtain access, even if they manage to steal a password, MFA should be mandatory for all business email accounts.
- Email Security Protocols: Make use of sophisticated security tools and filters. In order to stop email spoofing and identify similar-looking email addresses, enable protocols like DMARC, SPF, and DKIM.
- AI-Powered Security: Make use of machine learning and AI-driven solutions to examine email behaviour patterns and identify spoofing or unusual signals in incoming communications.
