In this article, we learn about Extensible Authentication Protocol, Key Characteristics of EAP, EAP Architecture and Components, How does Extensible Authentication Protocol Work, Common EAP Methods, Applications and Use Cases.
What is Extensible Authentication Protocol?
As an authentication framework rather than a particular authentication mechanism, the Extensible Authentication Protocol (EAP) is a key element of contemporary network access security. Although EAP specifies the overall syntax for authentication messages, the actual verification of credentials is carried out by particular EAP types or methods.
RFC 3748, which superseded RFC 2284, was the first to define EAP.
You can also read What is MSCHAPv2, How it Works & MSCHAPv2 Key Features
Key Characteristics of EAP
EAP’s flexibility and extension are its main advantages. Within its framework, this approach enables the smooth integration of several authentication protocols and techniques. Numerous credential types are supported by it, including:
- Passwords.
- Digital certificates or smart cards.
- Token-based authentication and biometrics.
EAP typically runs directly over data link layers, such as Point-to-Point Protocol (PPP) or IEEE 802, without requiring IP connectivity.
EAP Architecture and Components
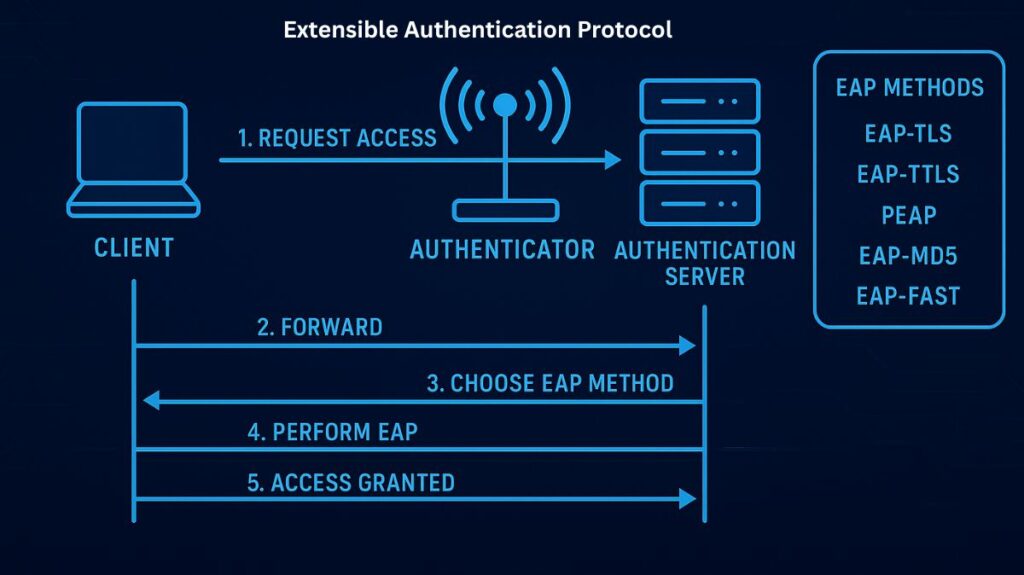
To perform authentication, the EAP architecture uses three primary interdependent components:
- EAP Peer (Supplicant): A laptop or smartphone is an example of an EAP Peer (Supplier), which is the user device or software requesting network access. It is in charge of handling authentication issues.
- EAP Authenticator: This device, such as a switch, wireless access point, or VPN concentrator, serves as the network gatekeeper. Although it does not actively take part in the authentication decision-making process, it does forward EAP communications between the peer and the authentication server.
- EAP Server (Authentication Server): The EAP Server (Authentication Server) is in charge of confirming the peer’s credentials and deciding whether or not access should be allowed. A RADIUS (Remote Authentication Dial-In User Service) server is frequently used to implement it.
How does Extensible Authentication Protocol Work?
EAP uses a “lock step” protocol, which consists of a sequence of requests and answers. The authenticator (server side) starts the communication by asking the peer (client side) to authenticate.
The typical exchange involves several steps:
- EAP Request/Response (Identity): The applicant receives an initial EAP-Request/Identity from the authenticator and replies with an EAP-Response/Identity (often the username).
- Method Negotiation: Using policies and capabilities, the authentication server chooses the best EAP method.
- Authentication Exchange: The cryptographic keys or credentials required for the chosen method are exchanged between the client and server. As long as necessary, this cycle is repeated.
- Result: The authenticator then approves or rejects network access based on the server’s communication of the result (EAP Success, Code 3, or EAP Failure, Code 4).
You can also read What is Password Authentication Protocol PAP & How it Works
Common EAP Methods
EAP’s extensibility has led to approximately 40 different methods being defined. Many modern, secure methods use tunneling to protect credentials exchanged over an insecure network.
| EAP Method | Description | Key Security Feature |
|---|---|---|
| EAP-TLS (Transport Layer Security) | Uses digital certificates on both the client and the server for mutual authentication. | Considered the most secure method; achieves strong authentication using Public Key Infrastructure (PKI). |
| PEAP (Protected EAP) | Encapsulates an inner EAP authentication method (like EAP-MSCHAP v2) within a TLS tunnel. | Requires only a server-side certificate to establish the secure tunnel, protecting the client’s subsequent password-based authentication. Developed by Cisco, Microsoft, and RSA Security. |
| EAP-TTLS (Tunneled TLS) | Similar to PEAP, it establishes a TLS tunnel using only server-side certificate authentication. | Allows legacy authentication protocols (EAP or non-EAP like PAP or CHAP) to be securely used inside the tunnel, simplifying client setup. |
| EAP-FAST (Flexible Authentication via Secure Tunneling) | Uses a Protected Access Credential (PAC), a generated shared secret, to establish a secure tunnel. | Does not require certificates, simplifying deployment overhead compared to EAP-TLS. Developed by Cisco as a replacement for LEAP. |
| EAP-SIM / EAP-AKA / EAP-AKA’ | Methods used for mobile networks (GSM, UMTS) leveraging the security features of the SIM card for authentication. | Provide seamless, secure authentication utilizing existing mobile infrastructure. |
Applications and Use Cases
EAP is frequently used in network settings when secure authentication is necessary:
- Wireless Networks (Wi-Fi): EAP is a crucial component of WPA, WPA2, and WPA3 Enterprise security schemes, offering clients utilizing the 802.1X standard safe, scalable authentication.
- Wired Networks: To authenticate people or devices connected to Ethernet ports, EAP is used in conjunction with the 802.1X Port-Based Network Access Control standard.
- Virtual Private Networks (VPNs): EAP techniques are used in Virtual Private Networks (VPNs) to safely authenticate users prior to their remote access to network resources.
The robustness of the selected approach is crucial to EAP’s efficacy; older approaches such as EAP-MD5 and LEAP are regarded as unsecure and susceptible to dictionary attacks and MitM assaults, respectively.
Analogy: Comparable to a universal power strip that can accommodate a wide variety of international electrical plugs is the Extensible Authentication Protocol (EAP). Although it does not care how the electricity is produced, the power strip (EAP framework) standardizes the connecting point and the power-drawing procedure. A smart card or a password are two examples of the unique authentication technologies used by the different plug types (EAP methods, such as EAP-TLS or PEAP), each of which provides the credentials required to successfully draw power and get access.
You can also read What is Channel Service Unit/Data Service Unit, How it Works
