We discussed the Ping of Death Attack, how it works, its historical context and modern relevance, mitigation techniques, and how to prevent ping of death attack.
Ping of Death Attack
One popular kind of Denial of Service (DoS) attack is the Ping of Death (PoD), which seeks to disrupt or totally stop a victim’s device, server, or service. Based on the Internet Control Message Protocol (ICMP), the ping command is a widely used utility for determining network reachability. This is where the name originates.
The fundamental idea is frequently likened to a mail bomb, when the target is attacked or destroyed if the recipient opens the package, setting off a mechanism.
How Ping of Death Attack Works?
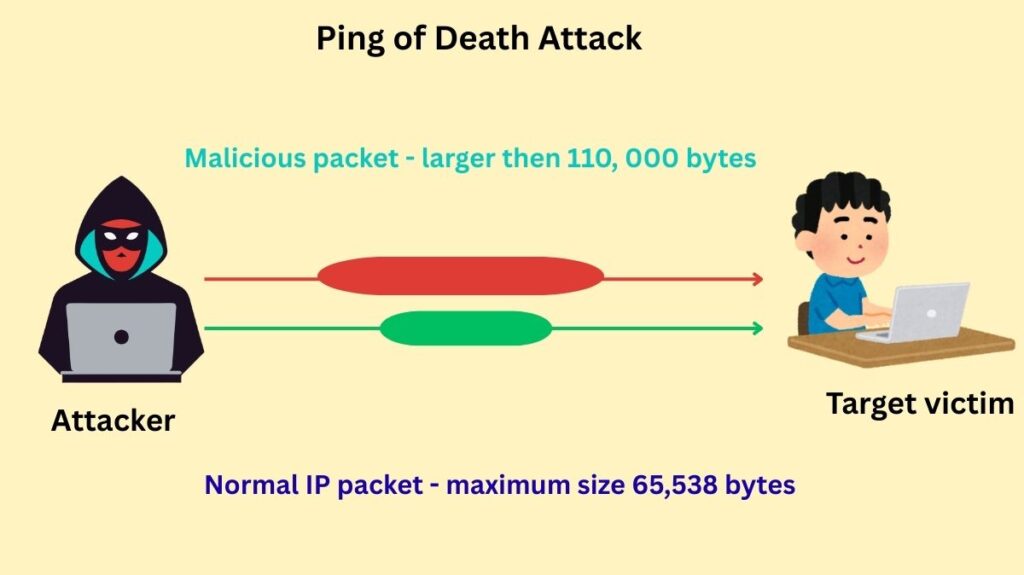
PoD attacks take use of flaws in older or unpatched systems’ handling of network packets bigger than the permitted maximum size. The following actions are part of the attack sequence:
Oversized Packet Creation: The maximum packet length, including the IP header, is 65,535 bytes according to Internet Protocol version 4 (IPv4). The attacker purposefully surpasses this maximum permitted size in their ICMP (ping) packet.
Fragmentation: The attacker’s system divides the large packet into several smaller pieces in order to send it over the network. Because each fragment is less than the size restriction, this fragmentation enables the packet to flow via the network architecture.
Reassembly Failure and Buffer Overflow: The target device tries to put the pieces back together into the original packet after receiving them. The memory buffer allotted for packet reassembly overflows because the reassembled packet is larger than the 65,535-byte limit.
System Crash: The victim’s system crashes, freezes, or reboots as a result of the memory buffer overflow problem.
Usually, the attacker only needs the target device’s IP address and no other operating system information. Although ICMP is frequently used in the attack, any Internet Protocol datagram can be exploited, such as broadcasts via Transmission Control Protocol (TCP), User Datagram Protocol (UDP), or Internet Packet Exchange (IPX). Regardless of the protocol payload, the fundamental problem lies in the reassembly process of IP fragments.
Historical Context and Modern Relevance
The mid-1990s saw the rise in popularity of the Ping of Death attack. Devices and networks were less advanced and more vulnerable to this vulnerability in the early days of the internet. It worked well against a variety of legacy operating systems, including Linux, Mac OS, Unix, Windows 95, and Windows NT.
Most computers and gadgets have been patched to contain protections against this particular vulnerability since the late 1990s (after 1998).
PoD is still dangerous, nevertheless, in several circumstances:
- Unprotected Legacy Equipment: This exploit may still target unpatched systems or unprotected legacy equipment.
- Protocol Flaws (IPv6): The attack has occasionally resurfaced due to new vulnerabilities. For example, PoD attacks against Internet Protocol version 6 (IPv6) networks made a formal comeback in August 2013.
- Kernel Vulnerabilities: In October 2020, a vulnerability (CVE-2020-16898) was found in the Windows component
TCPIP.sys, a kernel driver that, if abused, might cause a hard crash and complete shutdown. - IoT and Embedded Devices: A lot of contemporary IoT and embedded systems could not have safeguards against fragmentation handling, which leaves them open to PoD tactics.
Mitigation techniques
Protecting against PoD attacks requires both network-level security and system management:
Software Updates
Since vendors are releasing patches to address vulnerabilities linked to large ICMP packets, the most important defence is to regularly update all operating systems and network devices.
Filtering and Validating Packets
- Set up routers or firewalls to examine and weed out large or corrupted transmissions.
- In the assembly process, activate a checker to halt anomalous packets in the event that big data chunks are found.
- Make sure the “Fragment Offset” and “Total length” columns don’t add up to more than 65,535 bytes by implementing checks during the reassembly process.
- As an alternative, set aside more than 65,535 bytes of memory for reassembly.
Traffic Surveillance and Examination
- Use Deep Packet Inspection (DPI) or Intrusion Detection Systems (IDS) to automatically detect and respond to suspicious activities in network traffic, such as odd fragmentation or an unexpected spike in large ICMP packets.
DDoS Protection Services
Before malicious traffic, including packets that are malformed and typical of PoD attacks, reaches the targeted server, it can be detected and mitigated by using a DDoS protection service.
Blocking ICMP
To defend the network against the PoD threat, firewalls can be set up to completely block incoming ICMP ping messages. This isn’t the best option, though, because it also prevents valid pings that are necessary for debugging.
Also Read About How To Prevent Watering Hole Attack, Examples And Risks
How to prevent ping of death attack
The best defences against Ping of Death and other fragmentation threats include host-level and network perimeter security stacking.
Network Perimeter Security (Firewalls & Routers)
Packet Size Validation: Set up your router or firewall to check each incoming IP fragment’s length and offset fields. Any fragments that would cause the overall packet size to exceed 65,535 bytes upon reassembly should be dropped by the device.
Block Oversized ICMP: Set up the firewall to automatically discard any ICMP packets that are malformed or larger than the protocol’s typical maximum size limit.
Rate limitation: To guard against the associated Ping Flood attack, set rate limitation for ICMP traffic on your router or firewall to stop a large number of pings from a single source.
ICMP Disablement (Warning): As a last option, you can use the firewall to block any incoming ICMP echo requests, or pings. This is generally not advised, though, as it hinders the use of crucial network diagnostic tools that administrators need for troubleshooting, such as ping and traceroute.
System and Software Hardening (Host Level)
The most crucial line of defence is regular patching and updates. Verify that the most recent security updates are installed on all operating systems, network drivers (particularly those for the TCP/IP stack), and network equipment (firewalls, switches, and routers).
The fundamental buffer overflow flaws that the attack takes use of are fixed via patches.
Modern Operating Systems: To avoid buffer overflows during IP reassembly, use supported and updated operating systems, which have built-in defences and appropriate packet handling algorithms.
Advanced Detection and Mitigation
Install intrusion detection/prevention systems (IDS/IPS) that have Deep Packet Inspection (DPI) capabilities. DPI can identify and stop malicious or unusually fragmented packets linked to the Ping of Death before they reach the target system since it can analyse the packet content in addition to the headers.
Use cloud-based DDoS mitigation services for DDoS protection. Before they affect your infrastructure, these services filter and “scrub” harmful traffic, such as Ping Flood and PoD attacks, at the network edge.
