Identity Based Access Control (IBAC)
In the security architecture known as Identity-Based Access Control (IBAC), the primary basis for determining access to resources, systems, networks, and data is the distinct digital identity of the particular user or entity making the request.
Every access choice is based on confirmed identity, according to IBAC. IBAC explicitly links access permissions to the verified individual identification, in contrast to methods that depend on broad roles or intricate policies. The person attempting to access a resource is the main emphasis of the most basic interpretation of IBAC. This contrasts with Attribute-Based Access Control (ABAC), which concentrates on a broad range of context (attributes), or Role-Based Access Control (RBAC), which concentrates on a group (the role).
Core Principles and Features of IBAC
Several essential features define Identity-Based Access Control, which is essentially an identity-centric model:
- User-Centric Focus: Every access decision is associated with a unique user identity, guaranteeing a customised strategy where the user’s identity is of utmost importance.
- Direct Assignment: Rather than being distributed through roles or generalized qualities, permissions are given to specific individuals directly.
- Granularity: By enabling administrators to customise permissions at the individual level to uphold the principle of least privilege, IBAC facilitates fine-grained, customised access controls.
- Required Authentication: IBAC mainly depends on user identity verification through the use of usernames, passwords, biometrics, tokens, and Multi-Factor Authentication (MFA).
How Identity-Based Access Control Works
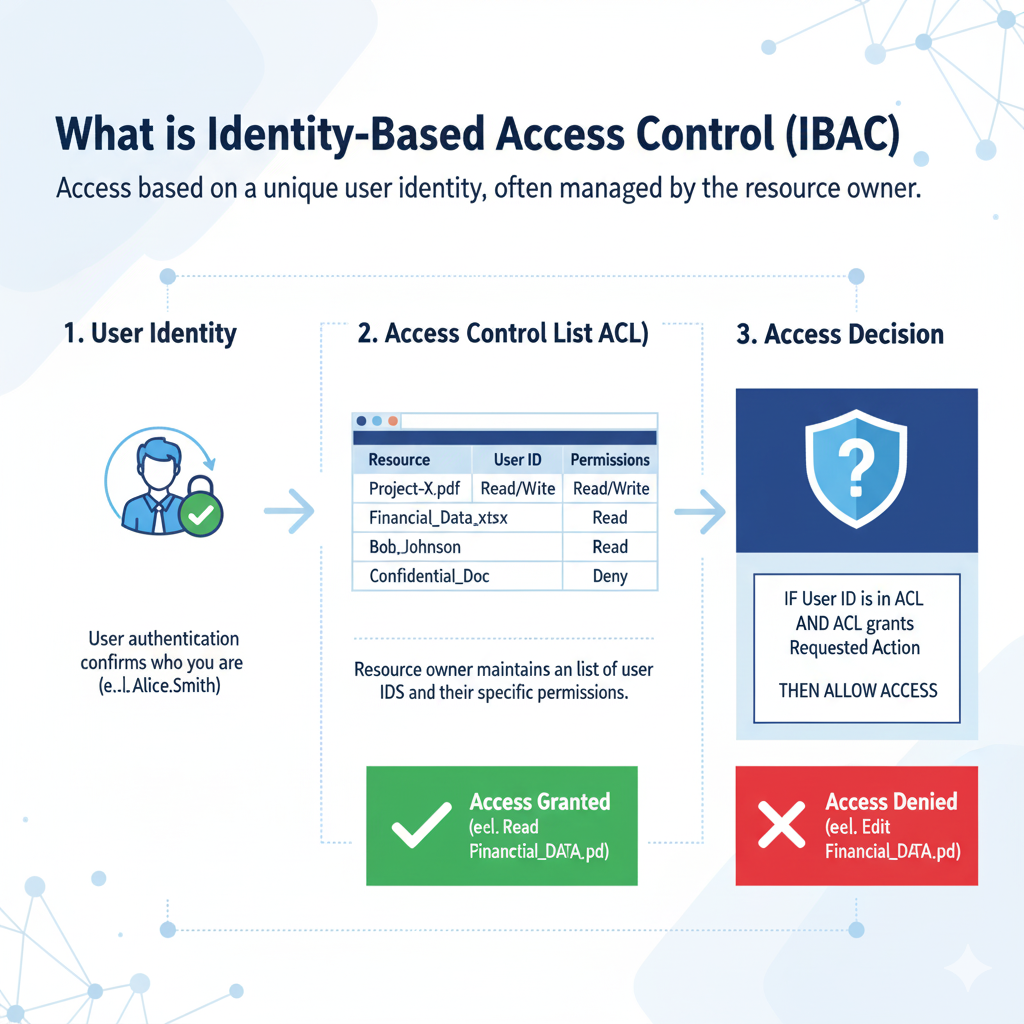
Before allowing a user to perform something, the IBAC mechanism verifies their identity:
- To request access, the user or device must identify themselves with a username, digital certificate, or device-specific identity. By creating the identification context, this stage starts the access request.
- User authentication: The system uses credentials or other authentication methods, including MFA, biometrics, or passwords, to confirm the claimed identity. By doing this, mimicry is avoided.
- Authorization/identification Verification: The system assesses the permissions linked to the user’s identification after confirming their identity in order to decide which resources or actions are available. This frequently entails verifying the resource’s direct permissions or an Access Control List (ACL).
- Decision/Enforcement of Access: The system verifies the user’s identification in relation to established access policies. Access is given if the user is authorised and refused if not. A Policy Enforcement Point (PEP) is responsible for enforcing this decision in real time.
Also Read About Types Of Access Control In Network Security: DAC, MAC & More
Advantages and Disadvantages
IBAC offers significant security enhancements, but it also poses management difficulties.
| Advantages (Benefits) | Disadvantages (Challenges) |
|---|---|
| Enhanced Security: Minimizes unauthorized entry by verifying identity before granting access. | Scalability Issues: Difficult to manage in large organizations; does not scale well inherently. |
| Accountability and Auditing: Provides clear audit trails and non-repudiation, as permissions are tied directly to an individual. | Administrative Overhead: Requires managing permissions individually for every user, increasing administrative burden. |
| Granular Control: Allows for precise, user-specific control, reducing the risk of over-permissioned accounts. | Complexity: Managing personalized permissions for thousands of users necessitates advanced Identity and Access Management (IAM) systems. |
| Simplicity (Small Scale): Simple and straightforward to understand and implement in personal or small business systems. | Dependence on Authentication: The success of IBAC is tied to the robustness of its authentication methods (e.g., weak passwords undermine effectiveness). |
Strong authentication techniques like MFA and biometrics are necessary, and IBAC solutions should interface with reliable IAM systems to automate the identity lifecycle (onboarding, updates, and offboarding) in order to overcome the difficulties of managing sizable user groups and authentication flaws.
Applications of IBAC
IBAC is useful in settings where accuracy and responsibility are essential, like:
- Healthcare: Supports HIPAA compliance by limiting access to electronic health records (EHRs) so that only authorised physicians can view patient data.
- Finance: Used to limit access to data centres, transaction platforms, and bank vaults by requiring personal identification verification.
- Cloud-First Enterprises: With permissions closely linked to each developer’s identity, cloud-first enterprises use this technique to protect developer access to repositories and cloud environments.
- Critical Infrastructure: Used to safeguard digital access to operational technologies and physical entry to industrial facilities and power plants, as well as to authenticate each employee.
Also Read About Rule-Based Access Control RuBAC Advantages And Use Cases
