What is a rogue dhcp server?
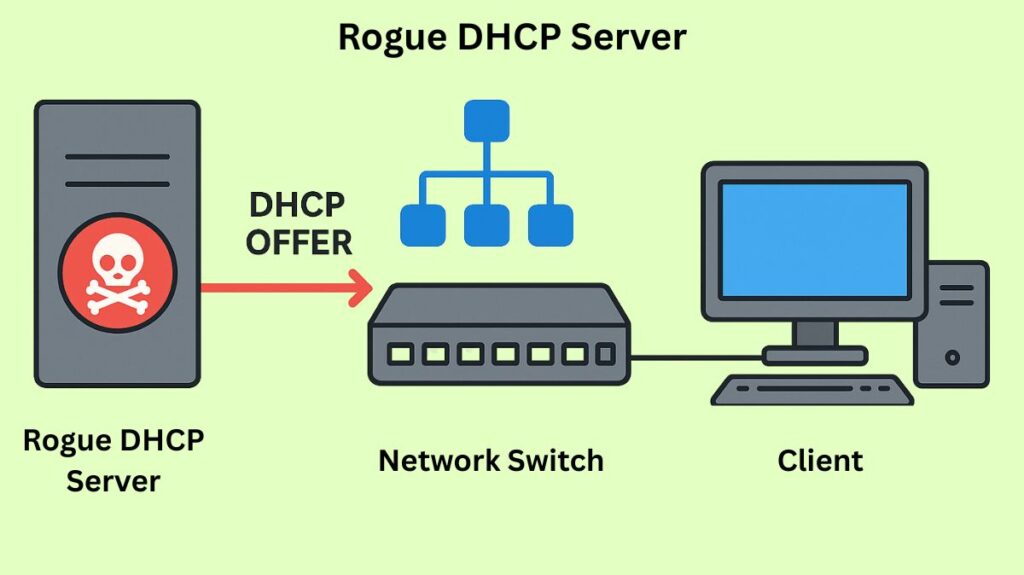
An unapproved DHCP (Dynamic Host Configuration Protocol) server running on a network that is not under the administrative supervision of network personnel is known as a rogue DHCP server. These servers give clients inaccurate IP configuration information, which can seriously jeopardise security and interfere with network functionality.
An uninformed person connecting an equipment, such as a router or modem, may unintentionally set up a rogue DHCP server, or an attacker may do so deliberately. The distribution of random IP addresses to network clients by virtual machine software, like VMware, can also result in unintentional rogue servers.
How Rogue DHCP Attack Works
The attack takes use of a basic flaw in the DHCP standard’s architecture: it doesn’t have a robust server authentication system. An unauthorised device might take part in the DHCP procedure because of the absence of authentication.
The Normal DHCP Process (DORA)
Typically, when a device joins a network, it retrieves configuration information using the DORA process:
- Find: The client sends out a request to find a DHCP server.
- Offer: In response, the approved DHCP server issues a DHCP Offer, allocating a legitimate IP configuration lease.
- Request: The provided IP address is requested by the client.
- Recognize: The lease is granted by the server.
The Attack Mechanism
When a rogue server is available, connecting clients will be provided with IP addresses and configuration parameters (such DNS servers and the default gateway) by both the rogue and legitimate servers.
In order to fool the clients into adopting its malicious configuration, the rogue server is usually set up to react more quickly than the legal server. The client obtains harmful configuration data rather than the correct settings when it accepts the rogue answer.
Malicious Configuration Details
Importantly, traffic is redirected to the attacker using the rogue server’s fictitious network configuration details:
- False Default Gateway: The attacker’s controlled computer is the source of the default gateway IP address provided by the rogue server.
- Malicious DNS Servers: In order to facilitate DNS spoofing or redirection, the rogue server supplies DNS server IP addresses that link to a malicious DNS server.
- Invalid IP Range: A local network failure could result from the rogue server distributing an invalid IP range.
Consequences and Impacts of the Attack
Attacks by rogue DHCP servers provide serious risks to the integrity, security, and stability of networks.
Data interception and Man-in-the-Middle (MITM) attacks
Enabling Man-in-the-Middle (MITM) attacks is the main danger.
- The attacker can intercept, view, capture, analyse, and alter all of the client’s network traffic sent to other networks by making its own IP address the client’s default gateway.
- By violating user privacy and network security standards, this interception enables the attacker to obtain sensitive information, such as login passwords and private data.
Phishing and Malware Distribution
Attacks are made easier by rogue DHCP servers that supply harmful configuration information:
- Phishing/DNS Hijacking: A malicious DNS server can be used to divert customers who are trying to access trustworthy websites (such as banks) to a phoney phishing site. Hackers illegally gain users’ passwords and social security information by using phoney websites.
- Malware: Hackers have the ability to respond selectively with malicious communications, such as viruses that interfere with users’ devices or phoney authentication requests. The hacker can remotely install harmful software, such as viruses or spyware, to take control of the computer once a client connects to the rogue device.
Network Disruption and Denial of Service (DoS)
Network instability brought on by rogue servers may result in lost connectivity:
- IP Address Conflicts: If several DHCP servers assign addresses within the same range, there is a greater chance of IP address conflicts, which is one of the most obvious effects. To cause this conflict, the hacker can broadcast a duplicate IP address.
- Network instability is the result of inaccurate or duplicate IP addresses being distributed, or of configuration settings that are different from the actual ones. This leads to problems with network connectivity, speed, and reaching other hosts.
- Denial of Service (DoS): Any legitimate device cannot connect to the network if a malicious or badly designed rogue server uses up all of the IP addresses available. Large swaths of the network could be disconnected from the rest of the domain and the internet as a result.
Detection and Mitigation Strategies
Certain security techniques can be used to effectively counteract rogue DHCP servers:
Common Mitigation Techniques
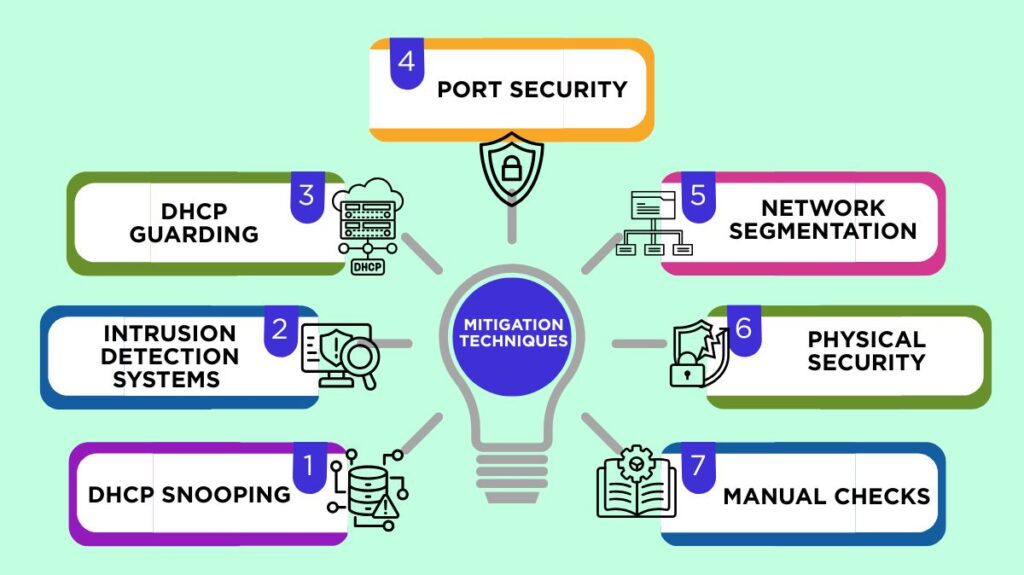
DHCP Snooping: One of the most popular and efficient defence techniques is DHCP spoofing. A common security feature on multilayer switches is DHCP spoofing, which keeps an eye on DHCP traffic and verifies DHCP packets. Any DHCP traffic found on an untrusted port is dropped or ignored by the switch, which is set up to trust only certain ports as valid DHCP server ports.
Intrusion Detection Systems (IDS): By using the proper signatures, IDS can prevent rogue DHCP servers.
DHCP Guarding: In order to prevent unauthorised servers from sending DHCP offers, network switches must be configured with trusted DHCP servers and DHCP guarding enabled.
Port Security: By using switches’ port security capabilities, unwanted devices are kept from connecting. This entails restricting the amount of MAC addresses permitted per port and setting policies to only permit authorised devices. Disabling unused switch ports is also a good idea.
Network Segmentation: Rogue DHCP servers can be isolated and their influence and spread limited by implementing VLAN segmentation.
Physical Security: Limit network port access to stop illegal devices from connecting to the local area network.
Manual Checks: To make sure the gateway and DNS server IP addresses on client computers correspond to the trusted router/server addresses, administrators can manually check them.
Rogue DHCP server detection
By searching for indicators like IP conflicts, erratic network connectivity, or an abnormally large volume of DHCP traffic (UDP ports 67 and 68), administrators can identify rogue servers. Detection tools include:
- Wireshark and other packet sniffers.
- For Windows XP, Vista, 7, Server 2003, and Server 2008, use Microsoft Network Monitor 3.4.
dhcp_probe(UNIX), SoftPerfect Network Scanner (Win32 Freeware),dhcploc.exe(Win32), DHCP Sentry (Win32),Rogue detect(Perl), and Open DHCP Locate (UNIX, Win32, C).- Manual analysis with Python’s Scapy module.
- FortiNAC Rogue DHCP Detection: This feature uses a specific interface on the FortiNAC appliance to keep an eye on authorised DHCP server activity. In order to find active entities serving IP addresses in particular VLANs, it executes a scheduled job. Events are triggered if there is no match between the discovered DHCP servers and a list of authorized servers, suggesting a suspected unauthorised server.
