RSTP attacks
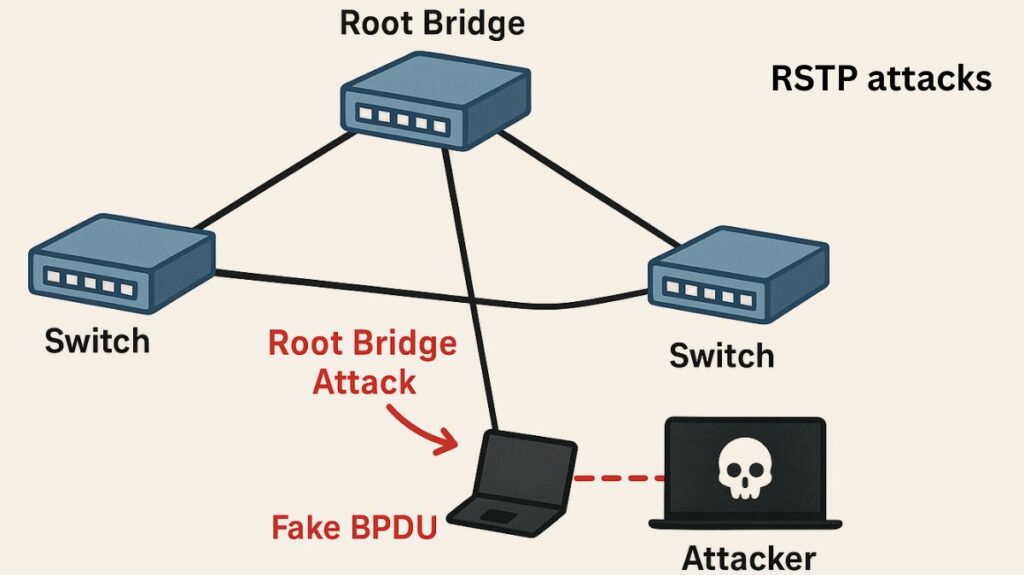
Malicious acts known as RSTP (Rapid Spanning Tree Protocol) attacks aim to undermine a network’s availability, confidentiality, or integrity by focussing on the protocol’s operation. Attackers take advantage of RSTP’s flaws to alter traffic flow, interrupt operations, or obtain unauthorised access because it governs the logical topology of a Layer 2 Ethernet network.
What is RSTP?
Rapid Spanning Tree Protocol (RSTP) is a network protocol that prevents loops in a Layer 2 Ethernet network by ensuring there is only one active path between two network devices. It is an improved version of the original Spanning Tree Protocol (STP), offering faster convergence when network changes occur.
Fundamental Vulnerability and Attack Mechanism
In order to describe the network topology, the fundamental working principle of RSTP depends on switches accepting Bridge Protocol Data Units (BPDUs) from neighbours. Because the Root Bridge is always chosen based on the lowest Bridge ID, the topology is susceptible. The Bridge ID is made up of the switch’s MAC address and a priority value (by default, 32768).
By trying to introduce a rogue device into the network, RSTP attacks usually aim to take advantage of this weakness.
RSTP Attack Types
These attacks usually aim to execute a Man-in-the-Middle (MitM) or Denial of Service (DoS) attack.
Root Bridge Hijacking (Root Manipulation Attack)
This is regarded as the most important and frequent RSTP/STP attack.
- Mechanism: Based on the Bridge ID that is the lowest, STP/RSTP chooses the “Root Bridge” the central switch for the network topology. The Bridge ID is made up of the switch’s MAC address and a priority value (by default, 32768). An attacker sends out bogus Bridge Protocol Data Units (BPDUs) with a much lower Bridge Priority (e.g., 0 or 4096) after connecting a malicious device (such as a laptop running an attack tool like Yersinia) to an access port.
- If the rogue device is successful in manipulating the topology, it becomes the new Root Switch. After then, the RSTP topology converges.
- Consequence (MitM/Eavesdropping): The attacker can make a large portion of the LAN traffic pass through their device by taking control of the root switch. This allows the attacker to either use a LAN analyser to copy a huge number of data frames (sniffing/eavesdropping) or intercept and alter sensitive communications (MitM).
- Result (DoS/Instability): The newly created topology might not be as good as it could be. There may be a protracted outage while a new, authentic root bridge is chosen if the attacker’s device crashes due to excessive traffic.
Also Read About What Is MAC Flooding Attack And Prevention Techniques
Flooding Attacks and BPDU Injection
In these attacks, phoney BPDUs are introduced into the network.
- BPDU Injection Attack: In order to fool switches into changing the spanning tree and possibly causing instability or rerouting traffic through a rogue device, attackers insert phoney BPDUs.
- DoS Attack for Topology Change Notification (TCN): The attacker bombards the network with a lot of spoof BPDUs, especially those that are Topology Change Notification (TCN). As a result, valid switches are forced to continuously reconverge or recalculate the topology of the Spanning Tree. Switches may briefly halt traffic forwarding or flush their MAC address tables while they are busy recalculating, which could cause a serious interruption or Denial of Service (DoS).
Impacts of RSTP Attacks
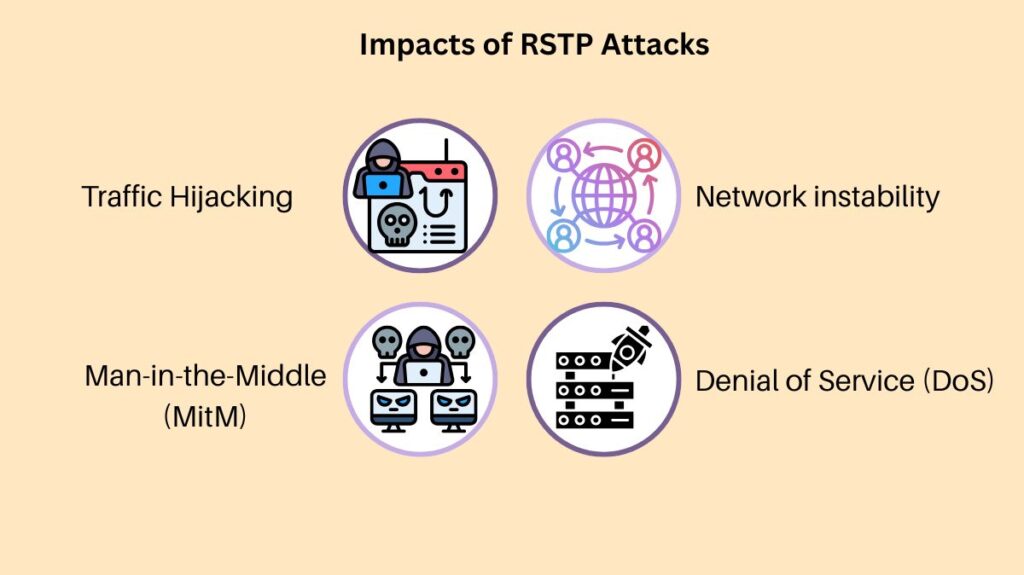
RSTP attacks may have detrimental effects on the network:
- Traffic Hijacking: By using hijacked devices, attackers can reroute network traffic.
- Man-in-the-Middle (MitM): Making it possible to intercept and alter private messages.
- Network instability: Performance is deteriorated by frequent reconvergence or the formation of suboptimal topologies.
- Denial of Service (DoS): When network services are unavailable because of flooding, frequent recalculations, or switch failures.
Mitigation Techniques
Optional features on Cisco switches are intended to lessen the risk of attacks and instability in the Spanning Tree Protocol. These characteristics concentrate on regulating the areas where BPDUs are permitted and guaranteeing the preservation of the root bridge placement:
The Root Guard
An essential security aspect for maintaining the integrity of the spanning-tree topology is Root Guard.
- Role: Root Guard stops a rogue switch from trying to take over as the spanning tree’s root. By keeping an eye out for superior BPDUs—those promoting a better route to the root it does this.
- Action: The feature puts a port into a broken (BRK) state for that VLAN when a superior BPDU arrives on a Root Guard-enabled port, which is often assumed to be a designated port or an access port. In display commands, this broken condition is referred to as a root inconsistent state.
- Traffic Handling: The port behaves similarly to the discarding or blocking states in this inconsistent state, discarding all traffic.
- Recovery: Without operator assistance, STP returns the port to its previous STP state if the incoming superior BPDUs stop for a while.
BPDU Guard
On access layer ports (PortFast-enabled ports), where a switch should never be connected, BPDU Guard is normally activated.
- Function: In the event that it suddenly receives a BPDU, it is intended to disable the port. By attaching a rogue switch to an access port, it avoids the loops that might result.
- Action: The switch immediately places the interface in an error-disabled (err-disabled) state after receiving a Bridge Protocol Data Unit (BPDU) on a port that has BPDU Guard enabled.
- Recovery: An administrator must manually provide the shut/no shut command on the interface in order to restore usability following a shutdown violation (the default violation mode).
Edge Port Behavior (PortFast)
The idea of an edge port, which is equivalent to the Cisco PortFast function, is pertinent to securely managing layer 2 ports even though it isn’t exactly a security feature because these ports link directly to end devices and shouldn’t ever receive BPDUs.
- Function: By bypassing the lengthy listening and learning phases of the original 802.1D STP, edge ports instantly switch to the forwarding state, accelerating convergence.
- Security Context: An edge port loses its edge port status and proceeds through the RSTP procedure normally after receiving a BPDU. The unexpected presence of another switch on an access link is handled by this transition (or the instantaneous action of BPDU Guard, if enabled in conjunction with PortFast).
Also Read About What Is VLAN Hopping Attack? How Does VLAN Hopping Work
