SYN Flood Attack
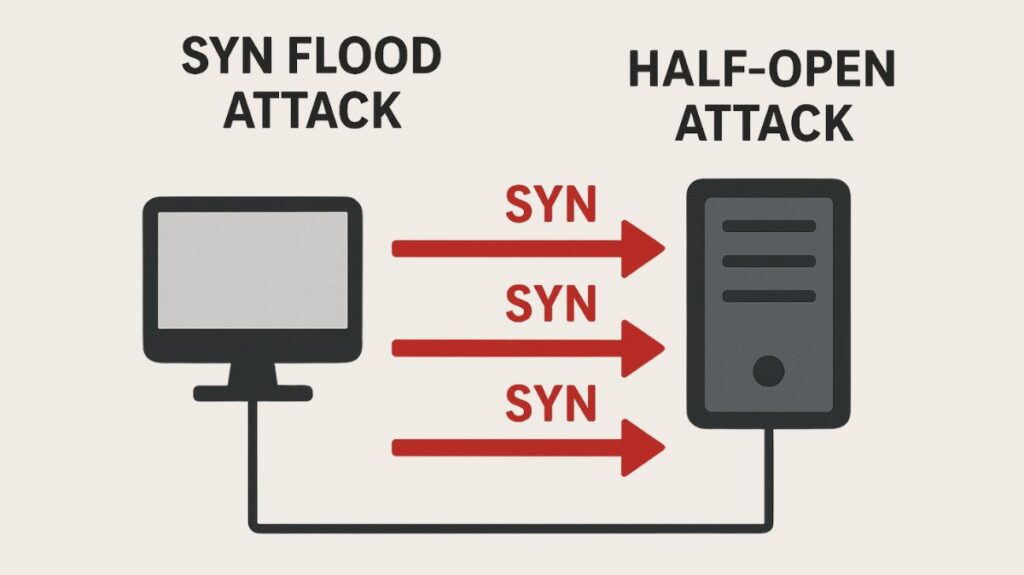
One well-known type of Denial-of-Service (DoS) attack that compromises the integrity of the Transmission Control Protocol (TCP) connection formation process is a SYN flood attack. It’s frequently classified as a Transport Layer attacks.
Rapidly establishing connections to a server without successfully completing them is the main goal of a SYN flood attack. By using up the server’s memory and connection table (or backlog), this operation renders the system inaccessible and unable to process connection requests from authorized users. The term “half-open attack” is occasionally used to describe the SYN flood attack because of this kind of vulnerability exploitation.
You can also read How To Prevent Watering Hole Attack, Examples And Risks
Mechanism of the SYN Flood Attack
The typical TCP three-way handshake, which is used to establish a TCP connection, has a weakness that the attack takes advantage of.
The Normal TCP Three-Way Handshake
SYN (Synchronize): Sending a SYN packet to the server to seek a connection is how a client starts the process.
SYN-ACK (Synchronize-Acknowledge): After receiving the request, the server sends the client a SYN-ACK packet to confirm receipt. At the same time, the server distributes resources while keeping a waiting connection in its memory (known as the SYN backlog).
ACK (Acknowledge): After the client sends one last ACK packet, the connection is made.
How the Attack Exploits the Handshake
A large number of SYN packets are sent to the target server by the malicious client in a SYN flood attack.
Server Response: While waiting for the final ACK, the server maintains a fresh half-open connection by responding to each incoming SYN packet with a SYN-ACK message and leaving a port open.
Missing ACK: Never does the attacker submit the last ACK packet. For a predetermined period of time, the server waits for the acknowledgement, thinking that the delay may be due to network congestion.
Resource Exhaustion: Through the deluge of these first requests, the attacker makes the server store a large number of half-open, incomplete connections. These connections bind server resources, which may eventually fill the connection backlog or surpass the available resources.
Denial of Service: A denial of service occurs when the server can no longer handle any more connection requests, malicious or not, due to the connection backlog being full.
You can also read What Is Quid Pro Quo Attack Meaning And Common Forms Of It
SYN Flood Attack Variations
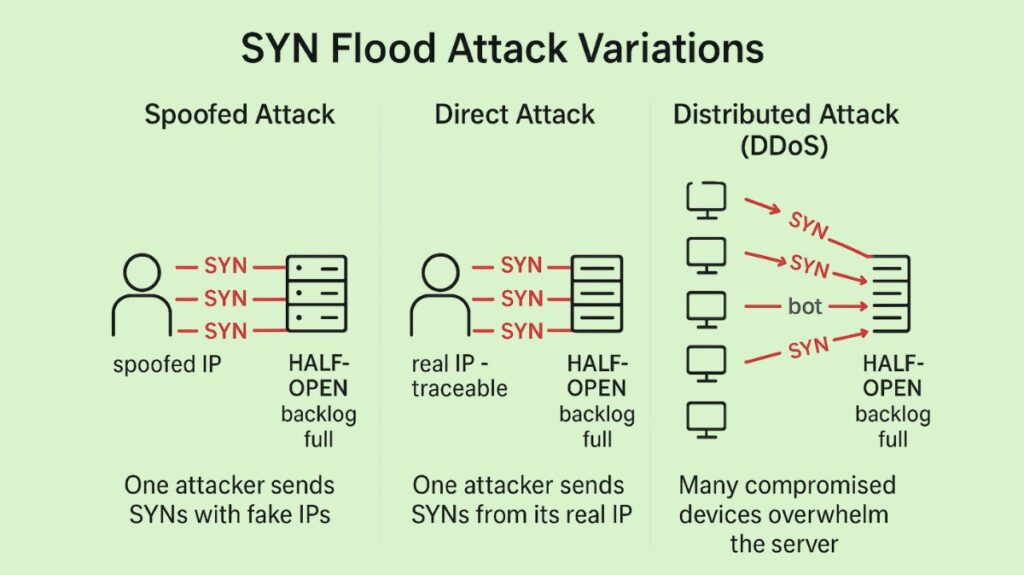
Techniques to conceal the attacker’s identity and increase disruption are frequently employed in SYN flood attack:
Spoofed Attack: Additionally, a malicious user can spoof the IP address on every SYN packet they transmit to thwart mitigation efforts and make it harder to identify them. Despite the possibility of spoofing, the packets may be able to be tracked back to their original source. Although conducting this kind of detective work is challenging, it is not impossible, particularly if Internet service providers (ISPs) are cooperative.
Direct Attack: A direct attack occurs when the IP address is not spoofing and the SYN flood attack occurs. The attacker in this attack does not conceal their IP address in any way. The attacker is extremely susceptible to detection and mitigation since they are utilizing a single source device with a legitimate IP address to develop the attack. By preventing the targeted machine from replying to the server’s SYN-ACK packets, the hacker creates the half-open state on the system.
Usually, firewall rules that block outgoing packets other than SYN packets or that filter out incoming SYN-ACK packets before they reach the malicious user’s computer accomplish this. This approach is rarely, if ever, employed in practice because mitigation is very simple: simply block the IP address of each rogue system. The attacker won’t give a damn about hiding the IP address of the compromised device if they are employing a botnet, like the Mirai botnet.
Distributed Attack (DDoS): If a botnet is used to create an attack, it is unlikely that the attack can be traced back to its origin. An attacker may have every deployed device impersonate the IP addresses from which it delivers packets in order to further obfuscate the system. Masking the IP of the compromised device is usually not a concern for the attacker if they are employing a botnet, like the Mirai botnet.
You can also read Man In The Middle MitM Phishing Attacks And How It Works?
Mitigation Techniques
There are a number of countermeasures available because the SYN flood attack vulnerability has long been recognized, including those mentioned in RFC 4987:
SYN Cookies: This defence is popular and works well. Rather of assigning resources to every SYN request, the server delivers a unique SYN-ACK packet with a cryptographically-hashed “cookie” inside. Resources are only released by the server in response to a valid ACK from the client that contains the same cookie. Half-open connections won’t use up the server’s memory with this stateless technique.
Increasing Backlog Queue: A specific number of half-open connections is permitted by each operating system on a targeted device. The operating system may increase the maximum number of half-open connections it permits in response to large SYN packet volumes. To effectively raise the maximum backlog, the system needs to set aside more memory to handle all of the new requests. Though system performance will suffer, it might still be preferable to denial-of-service attacks if the system lacks the RAM necessary to manage the larger backlog queue size.
Reducing SYN-RECEIVED Timer: It is possible for administrators to change the TCP SYN-Wait time to a low number, such 10 seconds. By forcing the router to terminate an unfinished connection more quickly, the attacker is prevented from accumulating a significant backlog of partially formed sessions on the target host.
Recycling the Oldest Half-Open TCP: After the backlog has been cleared, another mitigation technique is to overwrite the oldest half-open connection. According to this tactic, the backlog of malicious SYN packets must be cleared before the legal connections can be fully created. This specific defence is ineffective when the volume of attacks is increased or when the backlog is too small.
Filtering and Rate Limiting: Tracking, filtering, and removing suspicious traffic (such a large number of SYN packets) using firewalls, Intrusion Detection Systems (IDS), or Access Control Lists (ACLs).
TCP Intercept/SYN Proxy: Before sending verified connections to the application server, network devices like routers and load balancers have the ability to end the TCP connection and actively inspect partially created sessions.
Stateful Firewall Tracking: The number of TCP connection requests that are received per second can be monitored by a stateful firewall. To help the server survive the attack, the firewall can start filtering packets if it notices a pattern common to DoS attacks: a huge number of requests coming from a small number of clients. In general, SYN flood attacks are detectable by modern firewalls.
You can also read What Is A Baiting Attack And How Does Baiting Attacks Work
