Explore the fundamentals of Virtual Local Area Network, from various Types of VLANs to their inner workings. Understand how creating virtual networks can improve network performance, security, and management.
VLAN
A basic networking concept called a Virtual Local Area Network (VLAN) makes it possible to logically divide users and network devices according to their physical locations. In order to regulate users’ access levels and limit the quantity of broadcasts, it divides a network. In essence, a VLAN functions similarly to a virtual switch or network link, allowing it to share a physical structure with other VLANs while maintaining logical separation.
How VLAN Works?
Devices on a switch in a typical Local Area Network (LAN) regularly broadcast in order to find network resources, acquire IP addresses, and communicate. Like a highway with too many cars, these broadcasts can cause traffic to clog up, severely slowing down the network as the number of devices rises.
This is addressed by VLANs, which enable the grouping of switch ports into many VLANs, so establishing several smaller Layer 2 broadcast domains. Only other ports in the same VLAN will receive Ethernet packets from a switch that has been set up with VLANs; ports assigned to other VLANs will not receive them.
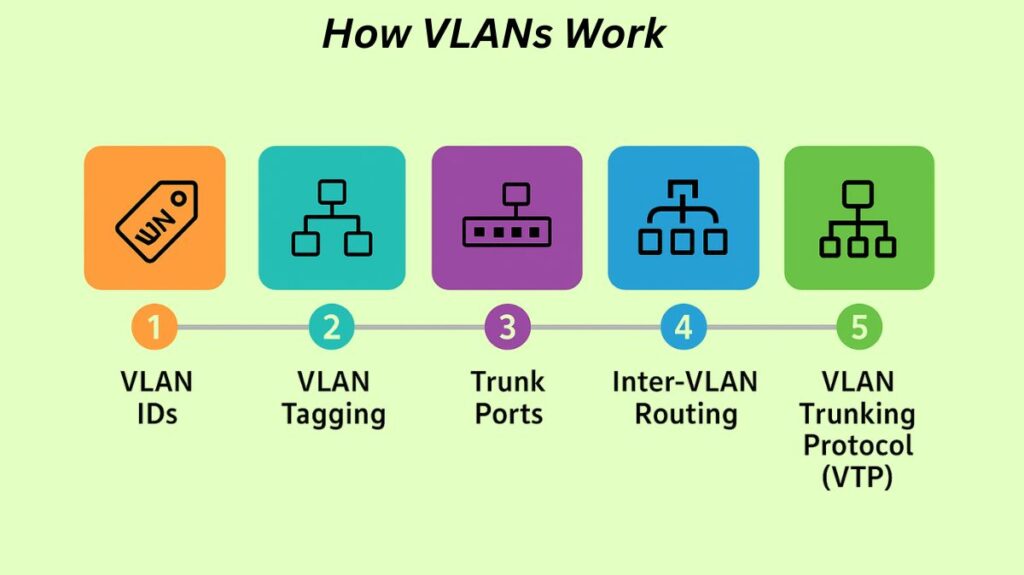
Crucial elements of VLAN operation include:
VLAN IDs: VLAN IDs (VIDs) are unique identifiers assigned to each VLAN. Up to 4,096 VLANs are possible with this ID, a 12-bit field in the header data of each Ethernet frame delivered to that VLAN.
VLAN Tagging: Using IEEE 802.1Q frame tagging, a frame’s VLAN membership is appended when it is transmitted via a trunk link. Upon receiving an untagged Ethernet frame from a host, a switch appends the VLAN tag linked to the device’s identity/traffic type (for dynamic VLANs) or the ingress port’s VLAN ID (for static VLANs). The tag is taken off before the frame gets to the intended device.
Trunk Ports: VLAN Trunking on the lines connecting the switches is necessary for VLANs to extend across several interconnected switches. Multiple VLANs’ traffic is carried by a trunk link, which uses the VLAN tag to determine which VLAN a message belongs to while it is being forwarded between switches. These may be referred to as tagged ports by other suppliers, however Cisco calls them trunk ports.
Inter-VLAN Routing: A Layer 3 device, like a router or a Layer 3 switch, is required for direct communication between devices in different VLANs. Generally, in order to communicate with one another, each VLAN needs its own IP subnet. Router-on-a-stick (ROAS) and Multilayer Switching, which use a Layer 3 switch with Switched Virtual Interfaces (SVIs) and a single router physical interface with several logical subinterfaces, are common techniques.
VLAN Trunking Protocol (VTP): A Cisco-proprietary messaging protocol called VTP is used to exchange VLAN configuration data, such as the VLAN ID and name, between Cisco switches that are part of a defined VTP domain. VTP has the ability to broadcast to other switches in the campus LAN any VLAN that is set up on a single switch. Nonetheless, many businesses decide to turn off VTP.
How VLANs Span Multiple Switches (Trunking and Tagging)
VLAN trunking on the lines connecting the switches is necessary for VLANs to extend across several interconnected switches. Traffic for several VLANs is carried over a trunk link.
VLAN Tagging: A frame must include information about its VLAN membership when it is transmitted over a trunk link. Frame tagging in IEEE 802.1Q is used to do this.
- Following the Source Address field in the original frame, the 802.1Q standard adds a 4-byte (32-bit) header. A 12-bit VLAN ID (VID), which supports up to 4096 VLANs, is contained in this header.
- A 1-bit feature called the Canonical Format Identifier (CFI) makes it possible for Token Ring frames to travel over Ethernet networks.
- For Class of Service (CoS) in QoS, the 802.1P User Priority field (3 bits) is utilized.
Inter-Switch Link (ISL): This is a proprietary legacy trunking technology from Cisco that encapsulates the entire Ethernet frame with a new header and CRC, specifically tagging VLAN information. Although 802.1Q is the suggested protocol, ISL is included for completeness, particularly for older Cisco switch types like as the 2960.
Access Ports: An access port connects to host devices and belongs to a single VLAN. The frame is cleared of any VLAN tagging prior to leaving an access port and reaching the final device.
Dynamic Trunking Protocol (DTP): Trunk port encapsulation type (802.1Q) and status (trunk or access) are negotiated using a Cisco-proprietary protocol. Disabling VTP is a common decision among businesses.
Benefits of VLAN
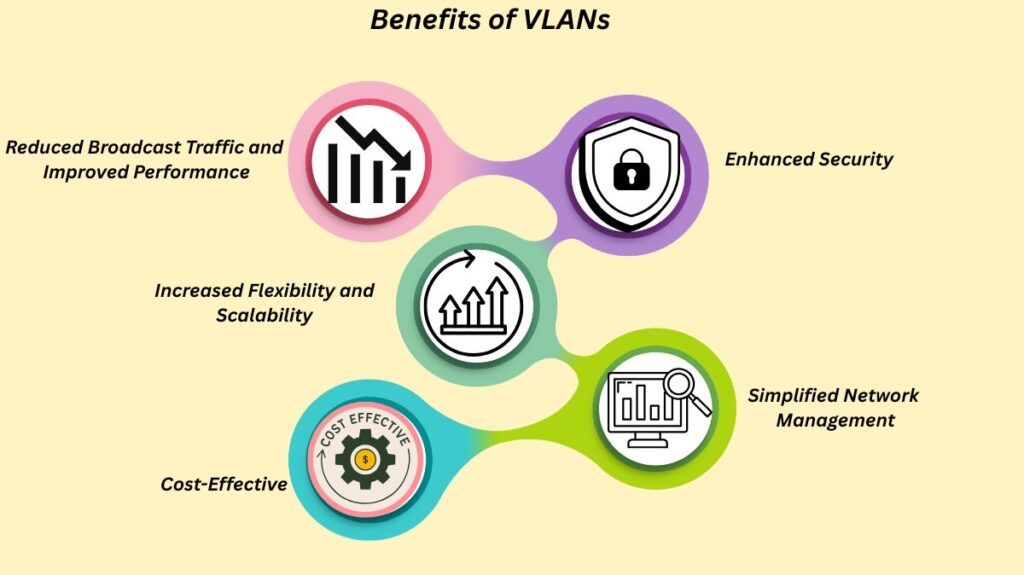
VLANs provide several benefits for network administration and design:
Reduced Broadcast Traffic and Improved Performance: VLANs can improve network speed and conserve device resources by limiting the number of devices that receive and process broadcast frames by dividing the network into smaller broadcast domains. Additionally, this aids with broadcast storm management.
Enhanced Security: By conceptually dividing users and departments, VLANs enable distinct security policies for each VLAN and limit the number of hosts that receive flooding frames. For instance, this keeps traffic from the sales and accounting teams separate, preventing unwanted access between departments.
Increased Flexibility and Scalability: By allowing users to be grouped by department or workgroup rather than by geographical location, VLANs remove physical borders from a LAN and increase the adaptability of network designs to organizational changes.
Simplified Network Management: Network administration chores like configuration, troubleshooting, and maintenance are made easier by logically grouping devices.
Cost-Effective: Administrative expenses related to additions, modifications, and migrations can be decreased with VLANs. By logically segmenting a network using current switches, they can also save money by avoiding the need for costly routers or other physical hardware.
Types of VLANs
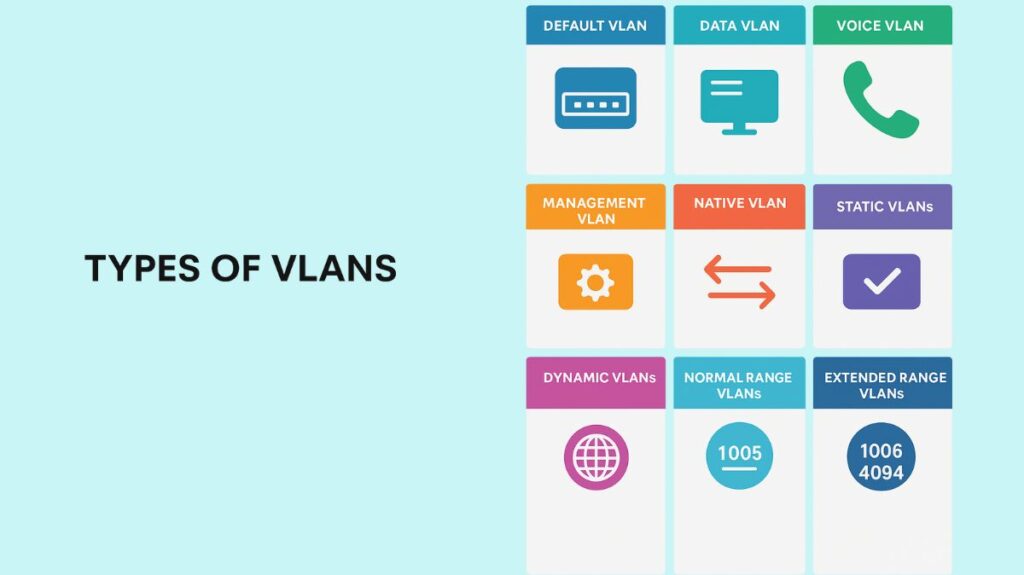
VLANs are divided into groups according to their purpose or method of traffic support:
Default VLAN: VLAN 1 is usually the first VLAN to which all switch ports are automatically assigned. You can’t remove it or change its name.
Data VLAN: Designated to separate user-generated data traffic from other forms of traffic, such as management or speech.
Voice VLAN: Defined with 802.1Q tagged traffic, usually for IP phones. It enables a PC and an IP phone to share a switch port while being in different VLANs. Previously, the voice VLAN was called the auxiliary VLAN.
Management VLAN: Used to manage network devices by offering a secure route for network administration traffic (such as SNMP, SSH, and Telnet). Although it’s a security best practice to set up a separate VLAN for this, VLAN 1 is frequently the management VLAN by default.
Native VLAN: Provides untagged traffic with a common identity on both ends of a trunk link. The default VLAN is 1. A native VLAN that is different from all other VLANs is a recommended security practice.
Static VLANs (Port-based): A port’s manual configuration for a particular VLAN is maintained until an administrator modifies it. The most popular and safest approach in production networks is this one.
Dynamic VLANs (Use-based): Ports use a VLAN Management Policy Server (VMPS) or network protocol to automatically decide their VLAN assignments, frequently based on MAC addresses. It is advised to use 802.1x instead of dynamic VLANs, which are regarded as obsolete.
Normal Range VLANs: All switches can use VLAN IDs between 1 and 1005. VLANs 1002–1005 are not deleteable and are designated for technologies such as FDDI and Token Ring.
Extended Range VLANs: There are switches that can use VLAN IDs between 1006 and 4094. For them to be stored in the database, VTP transparent mode is usually required.
VLAN Assignment Methods
Three general techniques can be used to assign VLAN membership:
Port-based VLAN assignment: A VLAN is statically assigned to a physical switch port, which serves as the basis for membership.
MAC address-based VLAN assignment: Membership is dynamically assigned based on the MAC address of the connected device. This gives mobile users more freedom and minimises manual configuration.
Protocol-based VLAN assignment: The network protocol such as IP or VOIP is used to determine membership assignment. This enhances security and facilitates the best possible traffic management.
Various techniques may be employed by network managers for distinct network segments according to particular requirements.
VLAN Applications
To improve performance and security, VLANs are extensively utilised in a variety of applications, especially in cloud computing environments:
Voice over IP (VoIP): Voice and data traffic can be separated using VLANs, which enhances call quality and eases congestion.
Departmental Segmentation: Organizing and securing a network is enhanced by creating VLANs for distinct departments, such as finance and human resources.
Guest Networks: Access to sensitive network locations is restricted for guest users by creating a separate VLAN for them.
IoT Devices: It improves security and eases congestion when Internet of Things (IoT) devices are isolated from the main network.
Security Concerns
Although VLANs restrict network access, making them intrinsically more secure than standard LANs, there are still security issues to be mindful of:
VLAN Hopping: Attackers can use strategies like switch spoofing and double tagging to transfer packets to unauthorised VLANs by taking advantage of switch configuration errors.
Inter-VLAN Routing: When routing across VLANs is not adequately secured, private information may be exposed. Traffic control requires the usage of Access Control Lists (ACLs).
Broadcast Storms: Broadcast storms can still be caused by assaults or configuration errors, which can impair network performance or result in denial of service (DoS).
Encrypted communication protocols, secure trunk configurations, ACL implementation, regular network traffic monitoring, appropriate VLAN configuration, and VLAN pruning are essential for reducing these hazards.
To put it simply, VLANs offer a strong method of establishing several logical networks inside a single physical network, which greatly enhances manageability, security, and performance.
You can also read What Is Mean By Troubleshooting Interface And Cable Issues?
