What are Network Components?
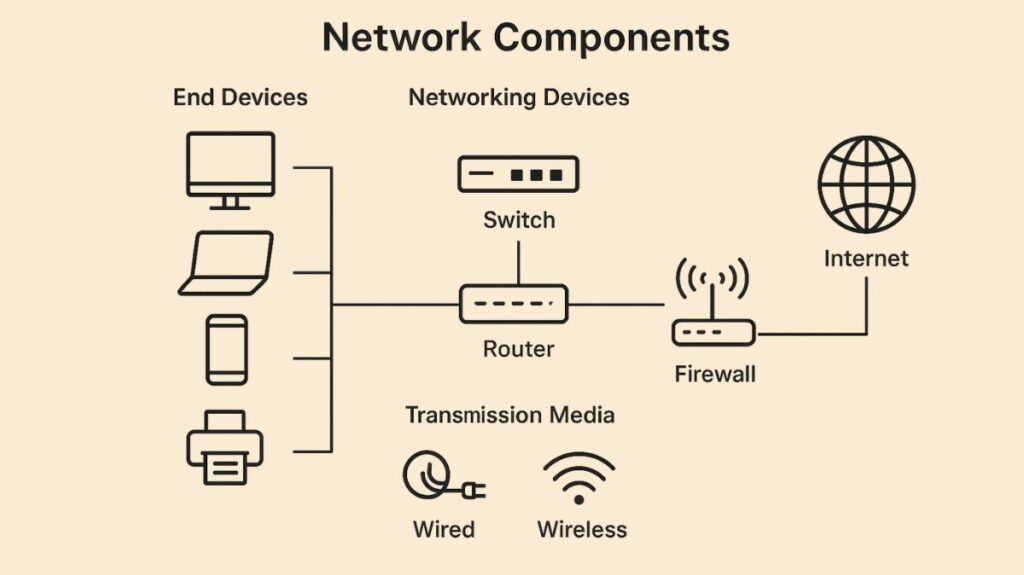
The fundamental units that make up a computer network are called network components, and they enable device connections, communication, and resource sharing. They consist of both software components and hardware components. The particular components needed vary depending on the kind of network being set up, and not all of the components must be used for a network to work.
Functions of Network Devices
- Data transmission and reception between devices is facilitated by network devices.
- Devices can connect to the network effectively and safely thanks to network devices.
- Network devices increase network speed and better control data flow.
- Through threat prevention and access control, it safeguards the network.
- Increase the network’s coverage area and address signal issues.
Also Read About Importance Of Computer Network Security Protect Your Data
Components of network hardware
The actual parts of a computer or electrical system that cooperate to carry out different functions are called hardware components.
Servers and Clients
- Clients are gadgets that ask other computers for data or services, including desktops, laptops, cellphones, and tablets. They utilize and get access to network resources.
- These services are offered by servers, which are strong computers that store information and operate programs that customers can access. They usually have the network operating system installed on them and are responsible for managing network resources. There are many different types of servers, including file servers, database servers, and print servers.
- In a workgroup network, peers are computers that both give and receive services from one another.
Transmission Media
The channels that allow data to move between devices in a network are known as transmission media. Coaxial and fiber optic cables are examples of guided media, while microwaves and infrared radiation are examples of unguided media.
Wired media
- The majority of contemporary Ethernet networks use twisted-pair connections. Physical Ethernet local area networks often use unshielded twisted-pair (UTP) cable.
- Coaxial cables: Frequently utilized for audio and video communications, cable television, and older network kinds.
- Fiber-optic cables: These cables use light pulses to send data, providing extremely fast speeds over great distances. Because of their favorable electrical properties, they are frequently used for backbone cabling.
- Ethernet: According to IEEE standards 802.3, Ethernet is the most popular LAN technology.
- USB Cable: Mainly used to connect PCs and smartphones.
Wireless media
- Bluetooth and Wi-Fi use radio waves.
- Satellite communication uses microwaves.
- TV remote controls and other short-range communication devices use infrared technology.
- Cellular.
Software Components
Operating systems, protocols, and other programs that support a network’s smooth operation are examples of software components.
Network Operating Systems (NOS)
Programs that operate on servers and control network resources, including file sharing, security, user access, and device-to-device communication. Cisco IOS, Linux, macOS Server, and Windows Server are a few examples.
Protocols
A collection of guidelines and standards that control the format, transmission, and reception of data and guarantee that various devices may communicate with one another. They specify the guidelines for communication between different networking equipment. Important protocols consist of:
- The core set of protocols for the internet is TCP/IP (Transmission Control Protocol/Internet Protocol). IP is responsible for addressing and routing, but TCP is in charge of data delivery (connection-oriented, dependable).
- Web browsing is done via HTTP/HTTPS (Hypertext Transfer Protocol/Secure Hypertext Transfer Protocol), with HTTPS encrypting communications for security.
- DNS (Domain Name System): Converts IP addresses from domain names.
- File transfers over networks are accomplished via FTP (File Transfer Protocol).
- Dynamic Host Configuration Protocol, or DHCP, automatically assigns IP addresses to networked devices.
- When just the IP address is known, the Address Resolution Protocol (ARP) determines the host’s hardware address (MAC).
- Internet Control Message Protocol (ICMP): Provides control and error messages, such as whether a host is reachable and whether services are available.
- SNMP, or Simple Network Management Protocol, is used to manage configurations, statistics, security, and performance in addition to monitoring and controlling network devices.
- In switched systems, STP (Spanning Tree Protocol) stops network loops.
Network Services
Offer specialized features including file servers, web servers, email servers, DNS, and DHCP.
Network Management Software
Network administrators can monitor and regulate network performance with the aid of network management software. Nagios, PRTG Network Monitor, and Wireshark are a few examples.
From a small home network to the worldwide internet, these elements all act together to form a functional network. These particular devices and components must be integrated for a freshly established network to operate properly.
Types of computer network devices
Network devices are crucial to the operation of a computer network because they act as a mediator in the data transmission process between two devices. Some typical network equipment seen in contemporary networks are listed below:
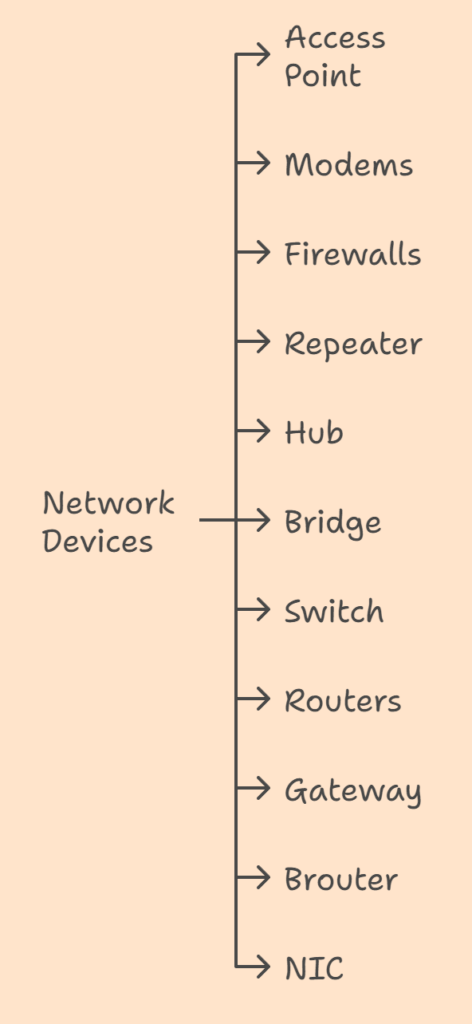
Access Point
In networking, an access point is a device that enables wireless devices, such as laptops and smartphones, to join a wired network. By establishing a Wi-Fi network, it enables wireless devices to connect to the internet or other networked devices. Access points are used to provide Wi-Fi in places without it or to increase a network’s range. They are frequently used to offer wireless internet access in residences, workplaces, and public areas.
Also Read About What A Network Is And What Are Benefits Of Networking
Modems
A network device called a modem, sometimes referred to as a modulator or demodulator, is used to transform digital signals into analog signals of various frequencies and send them to a modem at the receiving point. Telephone lines, cable systems, and other communication channels can all be used to send these transformed signals. An analog signal can also be converted back to a digital signal using a modem. Customers of Internet service providers (ISPs) typically utilize modems to access the internet.
Modem Types
Modems come in four primary varieties:
- DSL Modem: Slower than other models, yet it connects to the internet using standard phone lines.
- Faster internet than DSL is offered by cable modems, which transmit data via TV lines.
- Wireless Modem: Uses neighboring Wi-Fi signals to connect devices to the internet.
- Using mobile data from a cellular network rather than Wi-Fi or fixed connections, a cellular modem connects to the internet.
Firewalls
A firewall is a type of network security tool that keeps an eye on and regulates data traffic between your computer, network, and the internet. It serves as a barrier, permitting trusted data to go through while preventing unwanted access. By filtering traffic according to security standards, firewalls assist in defending your network against hackers, malware, and other online threats. Firewalls can be software applications, hardware devices, or even cloud-based services that are provided as SaaS, public clouds, or private virtual clouds.
Repeater
A repeater functions on the physical level. Its primary purpose is to regenerate (i.e., amplify) the signal over the same network before it gets too weak or corrupted to broadcast over the same network for an extended period of time. They duplicate the signal bit by bit and regenerate it at its star topology connectors that link after the initial strength when it starts to weaken. It is a device with two ports.
Hub
A hub is a repeater with multiple ports. A hub, like the connector in a star topology that links many stations, joins several wires originating from various branches. Since hubs are unable to filter data, all connected devices get data packets. Stated differently, all hosts connected by Hub maintain a single collision domain. Additionally, they lack the intelligence to choose the optimal path for data packets, which results in waste and inefficiency.
Also Read About Types of Hubs, Features, Advantages And Disadvantages Of Hub
Hub Types
- Active Hub: These are hubs that can clean, strengthen, and relay the signal in addition to the network and have their own power supply. It functions as a wiring center and a repeater. By using these, the maximum distance between nodes can be increased.
- Passive Hub: Hubs that get electricity from the active hub and wiring from nodes are known as passive hubs. These hubs cannot be utilized to increase the distance between nodes and just transmit signals onto the network without cleaning and boosting them.
- Intelligent Hub: It has remote administration features and functions similarly to an active hub. They also give network devices variable data rates. Additionally, it allows an administrator to setup every port in the hub and keep an eye on the traffic flowing through it.
Bridge
The data link layer is where a bridge functions. A bridge is a repeater that also has the ability to filter material by reading the source and destination MAC addresses. Connecting two LANs that utilize the same protocol is another usage for it. Each port is connected to a distinct network segment, and it usually connects several segments. For the purpose of connecting and managing various network segments, a bridge can include more than two ports. Because they serve comparable purposes, contemporary multi-port bridges are frequently referred to as Layer 2 switches.
Bridge Types
- Transparent Bridges: Transparent bridges are those in which the stations are totally ignorant of their presence; that is, they do not require station reconfiguration when a bridge is added or removed from the network. Bridge forwarding and bridge learning are the two techniques that these bridges use.
- Source Routing Bridges: In these bridges, the source station handles routing tasks, and the frame indicates the path to take. By delivering a unique frame known as the discovery frame, which propagates throughout the network via every path that could lead to the destination, the host can find the frame.
Switch
A switch is a multiport bridge with a buffer built in to improve performance and efficiency (more ports mean less traffic). A data link layer device is a switch. Because the switch can check for problems before forwarding data, it is particularly efficient because it only forwards good packets to the appropriate port and does not transmit packets with errors. Stated otherwise, the broadcast domain stays the same while the transition splits the hosts’ collision domain.
Switch Types
- Unmanaged Switches: These switches lack sophisticated configuration options and feature a straightforward plug-and-play design. They can be used as an extension to a bigger network or for small networks.
- Managed switches: These switches provide sophisticated configuration features including link aggregation, QoS, and VLANs. They enable centralized management and are appropriate for bigger, more intricate networks.
- Smart switches: These switches are usually simpler to set up and maintain, although they share characteristics with managed switches. They function well with networks that are modest to medium in size.
- Network segment devices exchange data via Layer 2 switches. They work at OSI’s Data Link layer.
- Layer 3 switches link OSI’s Network layer parts. In bigger networks, they are more advanced than Layer 2 switches.
- PoE switches are able to provide power to network devices using the same cable that transports data since they feature Power over Ethernet capabilities.
- Gigabit switches: Gigabit Ethernet rates, which are quicker than conventional Ethernet speeds, are supported by these switches.
- Rack-Mounted Switches: These switches are appropriate for usage in data centers and other big networks since they are made to fit in a server rack.
- Desktop switches: Usually smaller than rack-mounted switches, these switches are made to be used on a desktop or in a small office setting.
- The modular nature of these switches simplifies expansion and modification. They operate well in data centers and big networks.
Router
Like a switch, a router routes data packets by IP address. A router is primarily a Network Layer device. Your router’s dynamic routing table routes data packets between LANs and Wide Area Networks(WANs). Router-connected hosts have independent broadcast domains.
Gateway
As the name implies, a gateway is a passageway that connects two networks that may operate using various networking architectures. As messenger agents, they collect information from one system, decipher it, and then send it to another. Gateways can function at any network layer and are also known as protocol converters. Compared to switches or routers, gateways are typically more complicated.
Brouter
Bridging routers combine bridge and router functionalities. It works at the network or data connection layer. It can function as a bridge to filter traffic from local area networks and as a router to transport packets across networks.
NIC
A network adapter called a network interface card, or NIC, is used to link a computer to a network. In order to create a LAN, it is installed on the computer.It features a connector to attach the cable to it, as well as a unique ID printed on the chip. The cable serves as a conduit between the modem or router and the PC. Since NICs operate on both the physical and data link layers of the network model, they are classified as layer 2 devices.
Load Balancers
Distribute network traffic among several servers to promote scalability, improve application performance, and avoid overload.
Network Storage Devices
Data access, backups, recovery, and scalability are all improved by centralized data storage solutions like NAS (Network-Attached Storage) and SAN (Storage Area Networks).
Nodes
A network connection point is any computing device that transmits and receives network packets over the network. Computers, network printers, security cameras, and switches, bridges, routers, and cell towers are examples of end nodes. Intermediary nodes include these devices. Every node needs to be identified by a MAC or IP address.
Importance and Best Practices
Components of computer networks are essential for:
- Efficient Communication: They guarantee uninterrupted workflows by facilitating quick and secure communication.
- Flexibility and Scalability: Networks can expand and adjust to rising needs with the correct components, which lowers downtime.
- Enhanced Security: Network security is increased by the cooperation of elements such as routers and firewalls.
- Reliability: Modern load balancers, switches, and routers optimize data flow, reduce latency, and guarantee high availability.
The following are some best practices for network components:
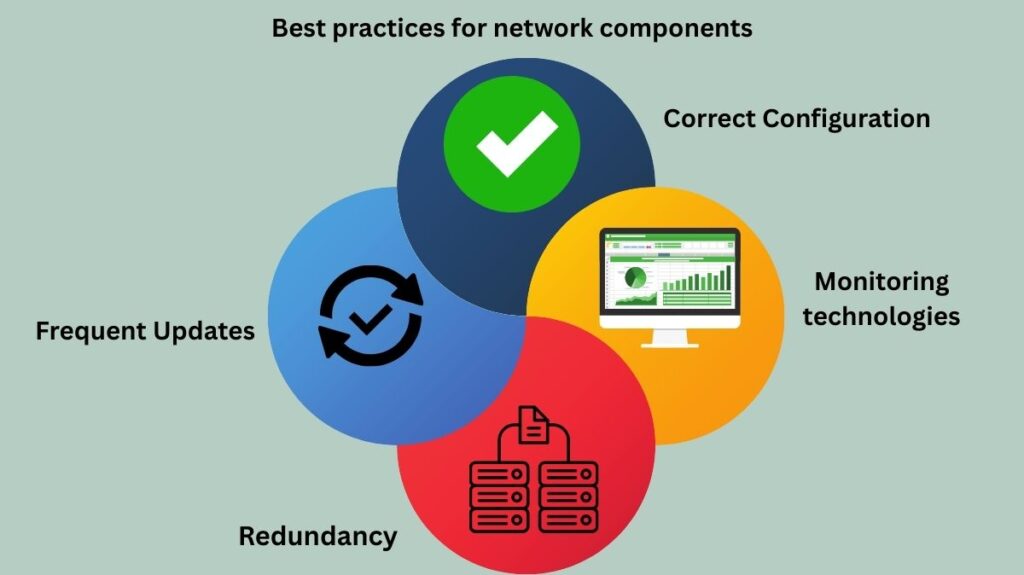
- Frequent Updates: To minimize security risks, keep software and firmware updated.
- Redundancy: Installing contingency plans for critical parts to guarantee continuous functioning in the event of a failure.
- Monitoring technologies: Making use of technologies to quickly identify and fix network problems.
- Correct Configuration: To maximize security and performance, routers, switches, and firewalls should be configured correctly.
Many traditional networking components are virtualized and provided as managed services in cloud settings, enabling businesses to create strong network infrastructures without having to worry about maintaining physical hardware. With improved scalability, flexibility, and global reach, cloud providers encapsulate the underlying complexity while adhering to the same core networking concepts.
Also Read About What Is A Metropolitan Area Network Architecture & Benefits
