We discussed what spoofing attacks are, how they work, and why they are important in this blog. Spoofing attack types, their advantages and disadvantages, and applications are also explained.
What is Spoofing attack?

Spoofing attacks, as used in cybersecurity, occur when a malevolent actor poses as a reliable source in order to trick people, steal information, or obtain unauthorised access. In order to appear authentic, the attacker conceals their identity or communication, taking advantage of consumers’ faith in well-known sources such as websites, phone numbers, IP addresses, and email addresses.
How it Works?
The fundamental weakness in network systems’ implicit faith in addressing data and services is exploited by spoofing attacks. By replacing real address data with fictitious ones, attackers accomplish their objectives.
The following are some specific spoofing attack mechanisms:
Source IP Address Spoofing
An attacker transmits packets with a spoof source IP address that differs from their real address. The spoof address, not the attacker’s actual address, is where the victim forwards any return traffic after receiving these packets. This can make it hard to track down the attacker by rerouting traffic to either a nonexistent IP or an unwary legitimate host.
MAC Address Spoofing
When an attacker sends frames to a Layer 2 switch, they are using a fake source MAC address. The switch may update its forwarding table (CAM table) with inaccurate information as a result, possibly giving the impression that the same host is connected to several ports. As a result, the attacker may receive frames that were intended for the legal host. A Denial-of-Service (DoS) attack against the legitimate host may result from the switch being confused and continuously rewriting its MAC address table entries.
ARP Spoofing/Poisoning
One type of MAC address spoofing is ARP spoofing/poisoning. Unwanted Address Resolution Protocol (ARP) replies, or gratuitous ARP messages, are sent to a switch by attackers with a faked MAC address. As a result, other LAN hosts’ ARP caches include inaccurate MAC-to-IP address mappings. A Man-in-the-Middle (MitM) attack can be made possible by tampering with the ARP database such that an attacker’s computer appears as the destination and systems blindly transmit traffic to the attacker’s MAC address.
DHCP Spoofing
When an attacker connects to the network, a rogue DHCP server gives authentic clients fictitious IP setup settings (such a default gateway). This can allow eavesdropping and a MitM attack by rerouting client traffic through the attacker’s device.
VLAN Spoofing (DTP Spoofing)
This technique involves sending a switch spoof Dynamic Trunking Protocol (DTP) packets, which causes the switch to go into trunking mode. In order to get around VLAN isolation, the attacker can send traffic that is tagged with the target VLAN once the switch is in trunking mode. The switch will then deliver these packets to their destination.
Reflection Attacks
This type of attack involves sending packets to a third, unintentional “reflector” host using the intended target’s (victim) fake source address. The target then receives unexpected traffic as the reflector directs its regular reply traffic towards the spoof source, which is the real target.
Amplification Attacks
One particular kind of reflection attack is this one. Using a protocol or service on the reflector (such DNS or NTP) that produces a significantly higher number of reply traffic, the attacker sends a small quantity of traffic to a reflector with a spoof source address (the victim’s address). The target is then disrupted and a large amount of network bandwidth is used by this amplified traffic being reflected back to it.
Why it is Important?
It is crucial to comprehend spoofing attacks for a number of reasons:
- Undermines Trust: Spoofing attacks specifically target the implicit trust that legitimate network settings often engender in devices and services. Numerous security lapses may result from this basic betrayal.
- Facilitates Other attacks: Spoofing frequently serves as a prelude to more intricate and destructive assaults, such as Man-in-the-Middle (MitM), Distributed Denial-of-Service (DDoS), and Denial-of-Service (DoS) attacks.
- Information Theft and Disruption: If spoofing is successful, it may result in denial of service to authorized users, unauthorised access, theft of private information, or session hijacking.
- Effect on Critical Infrastructure: Because cybercriminals have the means and know-how to carry out these attacks, they may have an effect on vital infrastructure.
Spoofing attack types
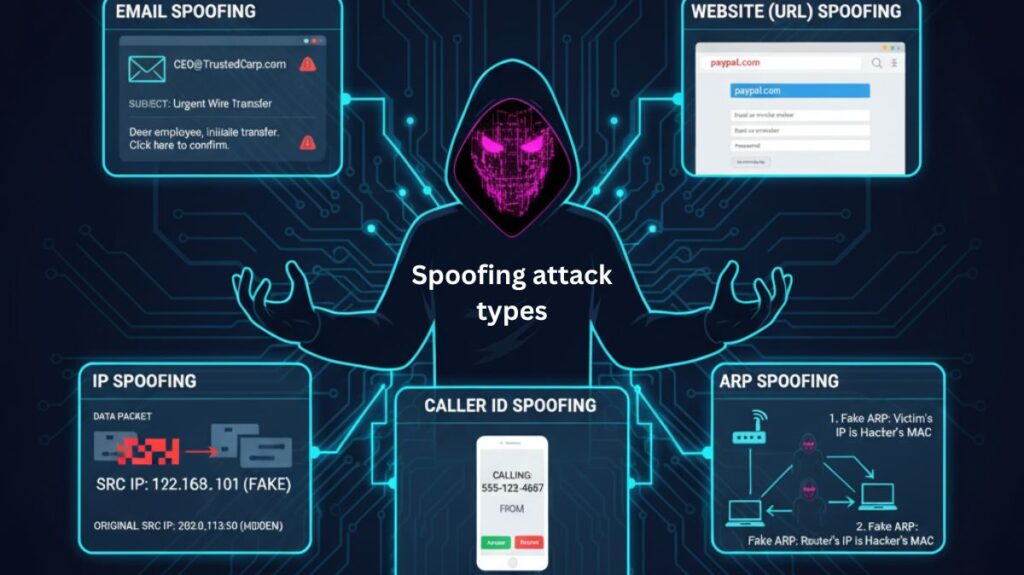
The various kinds of spoofing attacks include:
Email Spoofing
This is among the most popular and successful spoofing techniques. An attacker falsifies an email’s “From” address to give the impression that it was sent by a reputable organisation, a coworker, or a bank.
How it works: To display a phoney sender address, attackers alter the email’s header data (the envelope). This attack is relatively simple to carry out since the Simple Mail Transfer Protocol (SMTP), which is the foundational protocol for email transmission, has historically lacked a strong method for sender authentication. As part of a phishing campaign, the objective is usually to fool the receiver into downloading malware, clicking on a dangerous link, or disclosing credentials.
Website (URL) Spoofing
This attacks, sometimes referred to as domain spoofing, entails building a phoney website that resembles a genuine one almost exactly. To fool people who aren’t paying close attention, the attacker frequently uses a slightly modified URL.
How it operates: Attackers register a domain name that is a close variation of a website that they trust, such as (e.g., micr0soft.com instead of microsoft.com or paypa1.com instead of paypal.com). After that, they create a website that is identical to the authentic one in terms of branding, logos, and user interface. Usually, a malicious link or phishing email directs users to this fraudulent website. When they arrive, they are asked for sensitive information, such as login credentials, which the attacker then obtains.
Also Read About Advantages And Disadvantages Of TCP IP Model & Its Functions
IP Spoofing
This is a network-level attack that is more technical in nature. To conceal their genuine identity or to pretend to be another machine on the network, an attacker forges the originating IP address in network data packets.
How it operates: The attacker creates or modifies data packets using specialised software, inserting a fake IP address in the packet header in place of their own. This could be used maliciously for a number of reasons:
- To conceal their identity, the attacker can use spoof IP addresses to execute a distributed denial-of-service (DDoS) or denial-of-service (DoS) assault, which makes it hard for the victim to stop the malicious traffic or identify where it came from.
- To get around network security: An attacker can fake an IP address to get beyond firewalls and obtain unauthorised access if a network (such a corporate network) trusts traffic from that IP address.
Caller ID Spoofing
Telephone networks are the focus of this attack. To conceal their true phone number, an attacker purposefully fabricates the data sent to the recipient’s caller ID display.
How it operates: Attackers alter the caller ID that shows on the victim’s phone by using Voice over IP (VoIP) services or specialised software. They frequently pick a number that is local to the victim (“neighbour spoofing”) or that is associated with a business or government organisation they wish to mimic. Convincing the victim to answer the phone and then utilising social engineering (sometimes referred to as “vishing”) to convince them to provide personal information or money is the aim.
ARP Spoofing
This is a particular kind of local area network (LAN) man-in-the-middle (MitM) attack. IP addresses are converted into a device’s physical MAC address via the Address Resolution Protocol (ARP). By connecting their own MAC address to the IP address of a genuine device, an attacker delivers phoney ARP messages to a network.
The way it operates is that the attacker’s device successfully communicates to the network that it is the router and to the router that it is the victim’s computer. This enables the attacker to intercept, examine, and even alter the data in real time by tricking all communication between the two parties into going through their device.
Advantages
Spoofing attacks have various advantages from the perspective of the attacker:
- Disguised Identity: Sending packets with fictitious values is the main objective in order to make it challenging to identify the attacker.
- Bypass Security: Spoofing is intended to evade network security features like Access Control Lists (ACLs) and filters.
- Traffic Redirection: Attackers can reroute traffic through their own devices, allowing for data manipulation or eavesdropping, by supplying bogus DHCP information or contaminating ARP tables.
- Denial of Service: A key component of DoS and DDoS attacks, spoofing forces target systems to handle phantom traffic or magnify attack traffic from several sources.
- Impersonation: To obtain unauthorised access to network resources, an attacker may pose as a reliable computer or service.
Disadvantages
Spoofing attacks pose serious hazards to network defenders:
- Security Compromise: By undermining basic network trust, spoofing exposes systems to further threats including MitM, data theft, and illegal access.
- Service Disruption: When switches are continuously rewriting their CAM tables due to MAC spoofing, legitimate hosts may experience DoS circumstances or performance degradation. By leasing all available IP addresses with fake MAC addresses, DHCP spoofing can produce a denial-of-service issue for clients that are trying to connect.
- Difficulty in Detection and Tracing: It might be difficult to determine and track down the origin of an attack when phoney addresses are used.
- Resource Exhaustion: Attacks involving reflection and amplification have the potential to use up a lot of network bandwidth.
- Complexity of Mitigation: Because spoofing techniques can be diverse and flexible, protecting against them frequently necessitates a number of layered security procedures.
Also Read About Advantages And Disadvantages Of SNMP, How SNMP Work
Applications of spoofing attacks
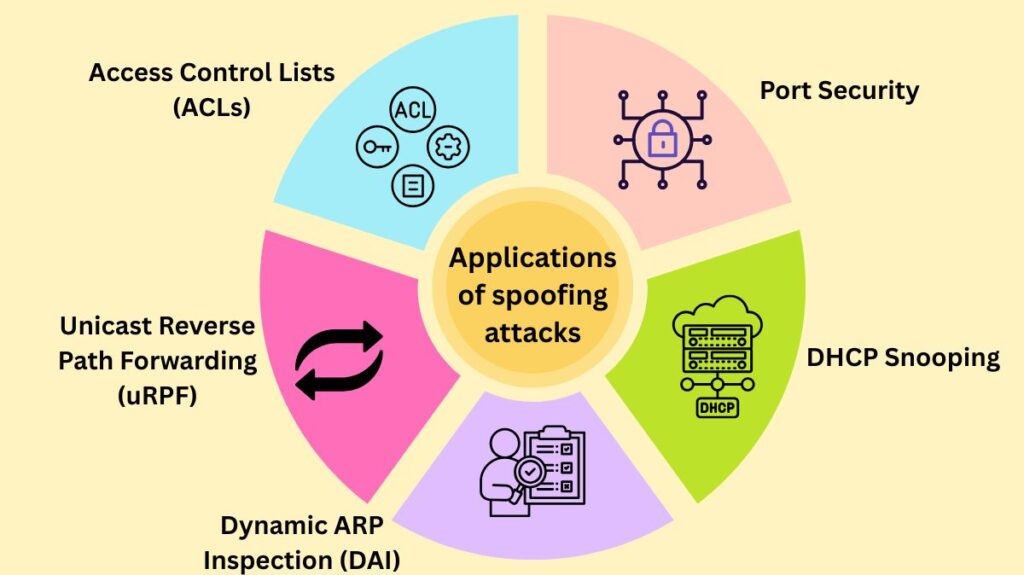
To counteract spoofing attacks, network security uses a variety of strategies:
Access Control Lists (ACLs)
ACLs have the ability to filter traffic according to IP addresses, both source and destination. By blocking packets claiming to be from internal network addresses but coming in from outside or by filtering particular harmful traffic types, they are an efficient method of reducing inbound and outbound IP address spoofing. Router resources can be saved by positioning ACLs as close to the attacker’s source as feasible.
Unicast Reverse Path Forwarding (uRPF)
To stop attacks employing spoof IP packets, router interfaces are equipped with Unicast Reverse Path Forwarding (uRPF). It determines whether an incoming packet’s originating IP address would normally leave the same interface, rejecting packets if the routing table indicates that the path is impractical. Limiting IP spoofing can be achieved in this fashion.
Dynamic ARP Inspection (DAI)
The purpose of the switch feature Dynamic ARP Inspection (DAI) is to stop ARP poisoning and spoofing. By comparing ARP packets against valid MAC-to-IP address bindings which are frequently discovered through DHCP snooping it filters out messages that don’t match. Rate restriction is another feature that DAI offers to stop DoS attacks on the switch CPU.
DHCP Snooping
By serving as a firewall between trusted and untrusted DHCP servers and verifying DHCP packets, this Layer 2 security feature reduces the impact of DHCP spoofing attacks. It can reject DHCP server messages received on untrusted ports and creates a binding table of valid DHCP leases. Incoming DHCP communications can also be rate-limited to stop DoS attempts that try to overload the switch’s CPU.
Port Security
When enabled on switches, this feature can prevent MAC address spoofing by limiting port access so that only MAC addresses that are permitted to communicate (either statically configured or dynamically learnt) can do so. The port may become err-disabled if an unauthorised MAC address tries to connect.
Also Read About How Does A Router Table Work, Types of Routing Table Entries
