Dynamic Trunking Protocol DTP Spoofing
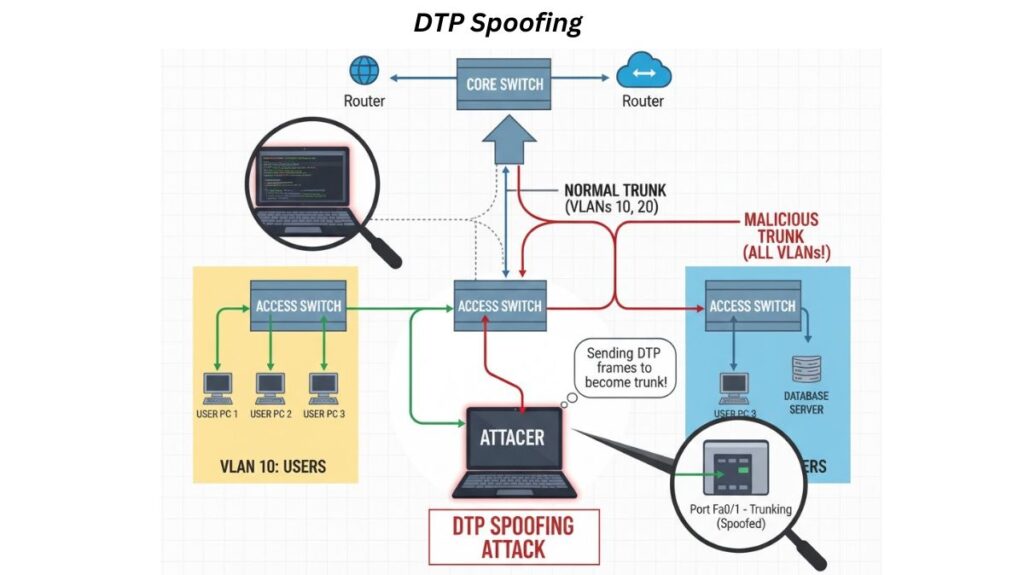
Often called switch spoofing, dynamic trunking protocol (DTP) spoofing is an attack technique used to carry out a VLAN hopping assault. In order to fool the network switch into creating a trunk link with the attacker’s device, this technique takes advantage of a network switch port’s default or incorrectly configured state. The attacker can send and receive traffic on any Virtual Local Area Network (VLAN) that is permitted on a trunk once a trunk link has been established.
The attacker tricks the associated switch port into switching from a regular access port to trunking mode by impersonating DTP messages. Bypassing VLAN segmentation, the attacker can access traffic from numerous VLANs after the port is converted to a trunk.
You can also read RSTP Attacks: What Is RSTP? Attack Mechanism And Types
Dynamic Trunking Protocol (DTP) Overview
This attack takes use of the Cisco-proprietary Layer 2 protocol, DTP.
Function: DTP serves the function of automatically negotiating the link between two network devices in order to ascertain whether the link should be a trunk link, which carries traffic for many Virtual Local Area Networks (VLANs), or an access link, which carries traffic for a single VLAN. Additionally, it negotiates the type of trunk encapsulation, such 802.1Q.
Vulnerability: Because DTP is an unauthenticated protocol, various spoofing attacks can affect it.
Mechanism of DTP Spoofing
The switch port must be set up in a dynamic mode for the DTP spoofing attack to work. The attacker exploits a switch’s default automatic trunking setup (DTP enabled on the switch).
The vulnerable dynamic modes are:
- Dynamic Auto: The port is passive; it advertises that it is capable of trunking but only enters the trunking state if the remote port initiates it (is set to
trunkordesirable).
- Dynamic Desirable: The port is open, actively tries to create a trunk, and uses DTP to let you know that the interface is trying to do so.
The attack process generally follows these steps:
- Attacker Connection: An attacker attaches a computer device (such as a laptop running Yersinia or another specialized program) to a switch port that is set up in dynamic DTP mode.
- DTP Spoofing: By actively transmitting DTP negotiation signals, the attacker’s equipment mimics or spoofs a genuine network switch. The creation of a trunk link is suggested by these malicious communications.
- Trunk Negotiation: The attacker’s device may enter trunk mode if the switch port is in a dynamic configuration and receives these bogus DTP packets without the necessary authentication.
You can also read Spanning Tree Protocol Attack and Mechanism of STP Attacks
Impact and Result: VLAN Hopping
The attacker circumvents network segmentation by achieving VLAN hopping once the switch port enters trunking mode.
Since most trunks permit all VLANs by default, the device of the attacker can now:
Send/Inject Traffic: To gain access to or launch an attack against hosts on any of the trunked VLANs, send traffic that has been tagged with the target VLAN ID (such as 802.1Q frames).
Receive Traffic: This can lead to data interception and possible privilege escalation since it listens to and records traffic from all trunked VLANs.
Gateway for More Attacks: The trunk link facilitates additional operations such as Man-in-the-Middle (MitM) attacks and ARP spoofing.
Mitigation Strategies
The most critical step to prevent DTP spoofing is to disable the automatic negotiation feature. Network best practice dictates disabling DTP on production networks by statically configuring ports.
| Mitigation Strategy | Cisco Command Example (Interface Mode) | Purpose |
|---|---|---|
| Set Static Access Ports | switchport mode access | This should be the default for all ports connected to end-user devices (PCs, printers, etc.). It explicitly forces the port into a permanent access state and implicitly disables DTP negotiation. |
| Disable DTP on Trunk Ports | switchport mode trunk followed by switchport nonegotiate | This explicitly forces the port into a permanent trunking state and prevents it from sending or listening for DTP messages. |
| Shutdown Unused Ports | shutdown | Administratively disable all unused switch ports and assign them to an unused VLAN to physically secure the network. |
| Change Native VLAN | switchport trunk native vlan [unused_VLAN_ID] | Change the default native VLAN (often VLAN 1) to an arbitrary, unused VLAN ID to mitigate the risk of Double-Tagging VLAN hopping attacks. |
The best defence is to statically set all ports and explicitly deactivate DTP when trunking is not required. In summary, DTP Spoofing is a major VLAN-related vulnerability where an attacker uses fictitious trunk negotiation signals to push a port into trunk mode, exposing numerous VLANs.
You can also read Types Of Access Control In Network Security: DAC, MAC & More
