What is EAP-TTLS?
A well-liked and safe EAP technique for providing safe and encrypted authentication for wired and wireless network connections is EAP-TTLS (Extensible Authentication Protocol–Tunneled Transport Layer Security).
Certicom and Funk Software (now Juniper Networks) created it. Like PEAP, EAP-TTLS is a hybrid system that seeks to strike a balance between the flexibility of password-based client authentication and the robust server authentication of EAP-TLS. In order to protect the authentication process while still enabling the usage of current username/password-based authentication procedures, it was created as an extension of the previous EAP-TLS protocol.
Tunneling, which is the technique of enclosing sensitive data within a safe, encrypted route, is essential to EAP-TTLS security.
You can also read What is Customer Premises Equipment CPE and Key Functions
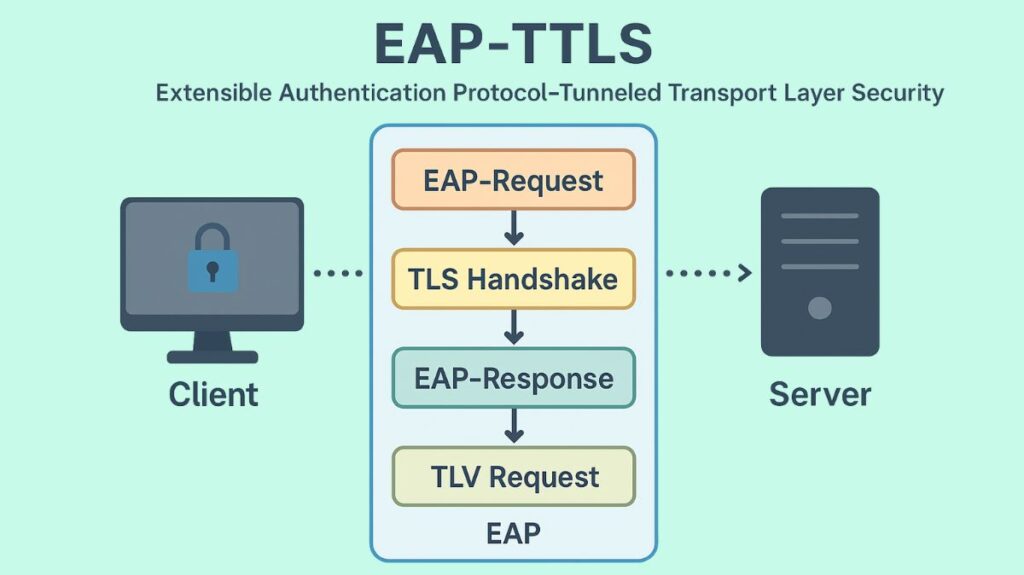
The Two-Phase Authentication Process
To guarantee safe authentication, EAP-TTLS functions in two separate stages:
Phase 1: Establishing the Secure Tunnel (TLS)
This first stage, which is the same as the first stage of EAP-TLS and PEAP, focuses on protecting the communication channel:
- Server Authentication: The connection is started by the client device (supplicant). The client is shown the digital certificate of the authentication server, which is usually a RADIUS server.
- Verification: By comparing the server’s certificate to its trusted root Certificate Authorities (CAs), the client confirms the server’s identity. In order to prevent connections to rogue access points and possible man-in-the-middle (MITM) attacks, this step is essential for robust server authentication.
- Secure Tunnel Creation: An encrypted TLS tunnel is created between the client and the RADIUS server after the server’s certificate has been verified. All ensuing authentication messages are safeguarded by this tunnel’s confidentiality and integrity.
The Server Certificate, which needs to be issued by a reliable Certificate Authority, is the sole certificate needed for this stage.
Phase 2: Client Authentication (Inside the Tunnel)
The client authenticates itself to the server following the establishment of the secure TLS tunnel. The Inner Authentication Phase is another name for this stage:
- Flexible Authentication Method: The client can authenticate itself using almost any alternative EAP technique or legacy protocol inside the secure channel. This covers techniques such as MS-CHAP, MS-CHAPv2, CHAP, and PAP (Password Authentication Protocol).
- Encrypted Transmission: To prevent interception and eavesdropping, client credentials (passwords, tokens, or other credentials) are safely transferred within the encrypted TLS tunnel.
- No Client Certificate Required: One important aspect of this inner authentication is that the client usually does not have to provide a digital certificate. The selected inner method, such as a username and password combination, is used to verify the client’s identity.
EAP-TTLS Characteristics and Use
Flexibility vs. PEAP
PEAP and EAP-TTLS both create a TLS tunnel to safeguard client credentials. But the main distinction is the inner authentication method’s adaptability:
- MS-CHAPv2 is the main method used by PEAP for inner client authentication.
- EAP-TTLS is more flexible to various current authentication infrastructures since it supports a much wider range of inner authentication techniques, including historical protocols like PAP/CHAP and other EAP kinds.
You can also read Advantages Of Wide Area Network WAN Architecture & Features
Advantages
EAP-TTLS provides a number of significant advantages:
- Strong Server Authentication: Offers strong defense against rogue access points.
- Adaptability: Because of its adaptability, it may incorporate nearly any authentication technique now in use, which is advantageous for businesses with a variety of or outdated authentication systems.
- Simplified Management: Since individual client certificates are typically not needed, it makes deployment easier than EAP-TLS.
- Password Protection: The TLS tunnel encrypts all client credentials.
Disadvantages and Weaknesses
Despite its security, EAP-TTLS has potential limitations:
- Complexity: Compared to more straightforward authentication techniques, setting up the protocol, including the TLS tunnel, might be more difficult.
- Reliance on Server Certificate: The correct administration and validity of the server’s digital certificate are crucial to the tunnel’s overall security.
- Lack of Mutual Certificate Authentication: Unless client certificates are optionally set, there is no certificate-based mutual authentication because, in contrast to EAP-TLS, the client usually does not present a certificate.
- Legacy Method Vulnerabilities: The usage of these inner methods can still compromise the overall security against attacks like password cracking or sniffing because it permits weaker legacy authentication methods (like PAP) within the tunnel.
Common Use Cases
In settings that need high security but don’t want to deal with the administrative load of client certificate management, EAP-TTLS is frequently utilized. It is a common option for wired networks (802.1X) and enterprise Wi-Fi (WPA/WPA2-Enterprise), where interaction with several backend authentication systems is required.
You can also read Cisco Software Defined Networking and How SD-WAN Works
