What is IEEE 802.1Q?
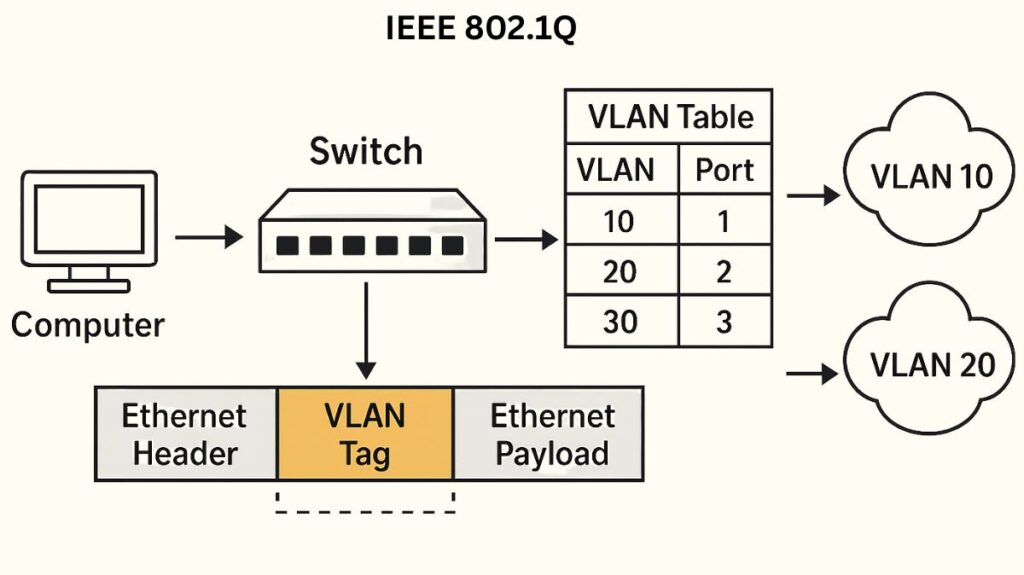
IEEE 802.1Q is the industry standard for VLAN implementation and tagging on Ethernet networks. Ethernet frames are tagged so switches and routers can identify their VLANs. Often called Dot1Q. This standard is needed for VLAN trunking, which combines VLAN traffic on one physical link. Most network devices support it, making it the most popular VLAN tagging method. IEEE manages this standard.
How IEEE 802.1Q Works?
Adding a 4-byte tag to the Ethernet packet header is 802.1Q’s main function. The technique is essential for network segmentation, traffic control, and security.
Tagging Process
- When traffic leaves an end device-connected access port, it is untagged.
- A trunk link between two switches requires the transmitting switch to include a 4-byte 802.1Q tag to the Ethernet packet.
- The tag sits between the source MAC address and the frame’s EtherType/Length fields.
- This insertion increases frame size from 1518 to 1522 bytes.
- Since the original frame changed, the switch recalculates the Frame Check Sequence (FCS) or checksum for the modified frame.
Transmission and Reception
- Tagged Ethernet frames maintain their VLAN identities while moving over trunk lines.
- The receiving switch forwards the frame to the correct destination port/VLAN after reading the VLAN ID from the tag.
- The tag stays in place if the destination port is another trunk.
- The tag is deleted before the frame is sent to an end device on an access port, preventing the end device from knowing about the VLAN.
Structure of the 802.1Q Tag
There are multiple fields that make up the 4-byte 802.1Q tag:
TPID (Tag Protocol Identifier)
The 16-bit field known as TPID (Tag Protocol Identifier) is always set to the hexadecimal value 0x8100. The frame is identified as VLAN-tagged by this value.
Tag Control Information (TCI)
Three subfields make up the 16-bit Tag Control Information (TCI) field:
- Priority Code Point (PCP): A 3-bit field used for Quality of Service (QoS) that shows the priority level of the frame. It is sometimes referred to as Class of Service or CoS. This field ensures that critical information is handled effectively, particularly for Layer 2 frames such as voice traffic.
- DEI (Drop Eligible Indicator): Previously known as a Canonical Format Indicator, the DEI (Drop Eligible Indicator) is a 1-bit field that specifies whether a frame can be dropped in the event of network congestion.
- VLAN ID (VID): A 12-bit field that provides a unique identification of the VLAN that the frame is associated with. Up to 4094 distinct VLANs can be identified by this field (values 1–4094, since 0 and 4095 are reserved).
Also Read About What Does The VLAN Trunk Protocol VTP Do? VTP Versions
VLAN native in 802.1Q
IEEE 802.1Q is compatible with the Native VLAN concept:
Untagged Traffic: Native VLAN frames are transmitted over a trunk link without 802.1Q tags. 802.1Q tags are used by all other VLANs. Traffic for VLANs 10, 20, or 30 will be tagged with their corresponding VLAN IDs, however traffic for VLAN 99, which is the native VLAN, will be sent without a tag.
Reception: A switch believes a frame that is untagged on a trunk port is part of the native VLAN that is set up on that port.
Default and Consistency: VLAN 1 is frequently the native VLAN by default. For a trunk link to function properly, both endpoints must agree on the native VLAN.
Security Risk: When the Native VLAN is configured incorrectly, networks are vulnerable to VLAN hopping attacks, in which malevolent actors may use untagged traffic to obtain unauthorised access. One best practice is to audit and secure native VLAN settings.
Also Read About What is Trunk Port, How it Works, Benefits, and Use Cases
Why is 802.1Q Important for Modern Networks?
802.1Q is crucial for contemporary networks for a number of reasons:
Traffic management: It keeps broadcast and multicast traffic from using up too much bandwidth by breaking up big networks into smaller, easier-to-manage chunks.
Security: 802.1Q improves security between network segments by establishing distinct logical networks.
Flexibility and Scalability: It facilitates easier network management and scaling by enabling many VLANs to share the same physical network equipment. This is especially helpful in cloud environments, data centers, and enterprise networks.
Quality of Service (QoS): By prioritising various network traffic types, the Priority Code Point (PCP) field in the tag guarantees that critical data is handled effectively.
Inter-Switch Link (ISL) Vs 802.1Q
In the past, Cisco also supported Inter-Switch Link (ISL), a proprietary VLAN tagging technology. But 802.1Q is now the most widely used and favoured standard.
Important distinctions include:
- Standard vs. Proprietary: Cisco switches are the exclusive owners of ISL, but the majority of network equipment implement 802.1Q, an industry standard protocol. 802.1Q must be used when connecting switches from different vendors.
- Tagging Mechanism: A 4-byte tag is inserted into the original frame via 802.1Q. However, ISL adds a new header and trailer, encapsulating the entire frame with a 4-byte FCS and a 26-byte header, for a total cost of 30 bytes.
- Overhead: 802.1Q has little effect on network performance and adds very little overhead. ISL is less popular due to its higher overhead; Cisco even suggests using 802.1Q.
- Support for VLAN: 802.Up to 4094 VLANs (12-bit VLAN ID) are supported by 1Q. ISL can accommodate up to 1005 VLANs.
- Native VLAN: The idea of an untagged native VLAN is supported by 802.1Q. However, all frames including those that would be in a native VLAN are tagged by ISL.
Configuration and Use Cases
Commands likeswitchport mode trunk and switchport trunk encapsulation dot1q are commonly used when configuring a switch port for 802.1Q trunking. Older Cisco switches, for example, might not need the encapsulation command as 802. The only supported type can be 1Q. Using subinterfaces and the encapsulation dot1q vlan_id, routers can also be set up to route between VLANs on an 802.1Q trunk link. Managing interdepartmental traffic in enterprise networks, enabling communication across hybrid networks in cloud settings, and permitting multi-tenant isolation in data centers are examples of common use cases.
