What is IP Spoofing?

In computer networking, IP spoofing is a malicious technique where an attacker generates Internet Protocol (IP) packets using a changed or faked source IP address. The main purposes of this fabrication are to obscure the origin of attack traffic, conceal the sender’s true identity, or imitate another computer system.
How IP Spoofing Works?
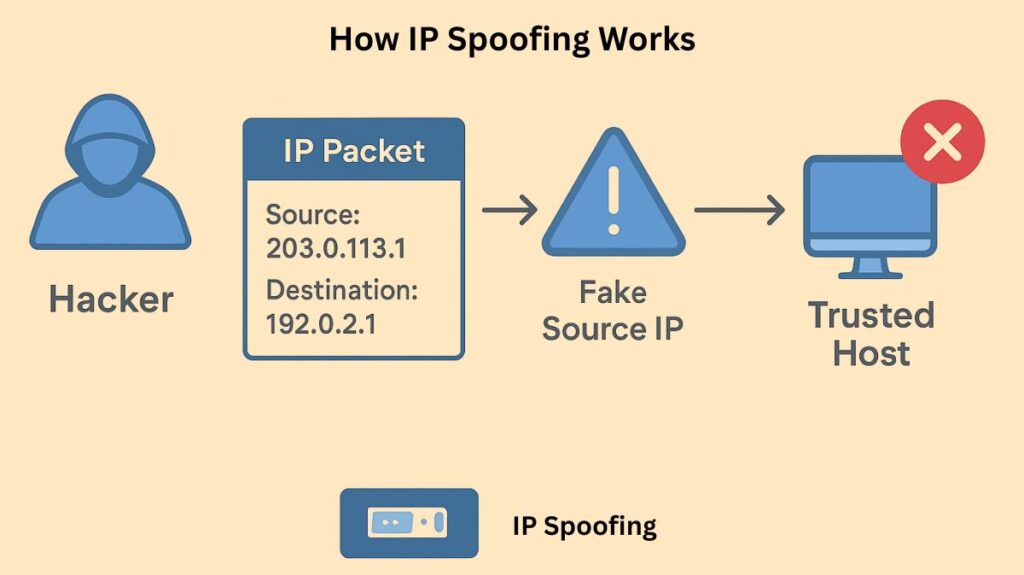
An IP header, which carries important routing details like the source IP address, is present in every data packet transmitted over the Internet. The IP address from which the packet was sent is typically the source address.
The source address field in the outgoing packet header is altered by the attacker in an IP spoofing attack. Unless intermediate systems are set up to verify or filter them, the network will forward these packets with fake sources because the IP protocol is stateless.
The spoof IP address is frequently that of a reliable host or system on the target network if the attacker’s goal is to obtain unauthorized access. After obtaining the trusted IP address through a variety of methods, the hacker must alter the packet headers to give the impression that the packet is coming from the trusted host.
The fact that the recipient computer routes any response packets back to the source IP address indicated in the header, which is the faked address rather than the attacker’s actual address, is a major drawback of IP spoofing. Because of this, IP spoofing works best in assaults that don’t require the attacker to establish a two-way connection or get a response.
You can also read What is Quishing, How Quishing Attacks Work and Examples
Applications and Attack Types
Because it enables attackers to conceal their location and get around security measures, IP spoofing is regarded as a crucial technique in many assaults.
Denial-of-Service (DoS) Attacks
The most common usage of IP spoofing is in denial-of-service (DoS) attacks, which aim to overwhelm the target with excessive traffic.
- Hiding Identity and Evading Mitigation: Distributed Denial-of-Service (DDoS) attacks can employ randomly generated fake IP addresses throughout the IP address space. This complicates mitigation attempts and makes it challenging for law enforcement and security teams to identify the actual source, making it tough for the victim to block the traffic by only filtering out a few source IPs.
- Reflected and Amplification Attacks: Spoofing is crucial for reflected attacks, in which the attacker utilizes the target’s IP address as the falsified source to overwhelm the victim with a high number of responses from unprotected intermediary servers.
- Smurf attacks, DNS amplification, and NTP amplification are a few examples where a small initial request results in a significantly bigger answer that is sent to the spoof victim address.
Unauthorized Access and Masquerading
Spoofing is a technique used by attackers to mimic a reliable system or peer.
- Bypassing Access Controls: An attacker can get around access controls or authentication methods that only use IP addresses by impersonating a trusted host’s IP address. Services like Remote Procedure Call (RPC) services and the R services suite (e.g., rlogin, rsh) that rely on IP address authentication are susceptible.
- Masquerading/Session Hijacking: Although contemporary protocols frequently make this more difficult, an attacker may attempt to take over a user’s session or obtain unauthorized access to a network by impersonating a trusted IP address.
Data interception and reputational harm where the attack seems to come from a genuine source are two other possible malevolent applications.
Legitimate Uses of IP Spoofing
It’s not necessarily harmful to use packets with a fictitious source IP address.
- Performance Testing: To simulate hundreds or thousands of “virtual users” visiting a website at once, commercial testing programs occasionally employ IP spoofing, which enables each simulated user to have a unique “return address.”
- Load Balancing: Some server-side load balancing strategies can make use of IP spoofing. This results in significant savings in outgoing message processing burden and networking hops by enabling the load balancer to effectively spray incoming traffic without having to be involved in the return path from the servers to the client.
- Security Testing: To test how systems react to different assaults, security professionals may employ spoofing.
Defense and Mitigation Strategies
Organizations can put measures in place to secure their networks, even if IP spoofing cannot be completely eradicated because the design of TCP/IP makes it possible to change the source IP.
The most effective operational control against spoofing is packet filtering.
- Ingress Filtering: This technique looks at arriving packets at the edge device or network gateway. A packet is rejected as evidence of spoofing if it arrives from the outside (external network) but purports to have a source IP address from within the internal network (your local domain).
- Egress Filtering: This technique checks outgoing packets to make sure the originating IP address is legitimate and part of the internal network of the business. This stops a spoofing attack against external systems from being launched by a network attacker.
Additional defensive measures include:
- Unicast Reverse Path Forwarding (uRPF): Using strict mode, for example, routers can discard packets whose source address would be unreachable over the interface they arrived on a method called Unicast Reverse Path Forwarding (uRPF).
- Strong Authentication: Rather than depending only on IP address authentication, organizations should employ strong verification and authentication techniques, such as mandating TLS, tokens, or multi-factor authentication (MFA).
- IP-Level Encryption: IP packets can be authenticated and encrypted using protocols like IPsec (Internet Protocol Security), which protects data integrity and makes it more difficult to spoof addresses.
- Monitoring and Detection: To keep an eye out for questionable network behavior, organizations should employ network monitoring software. Defenders frequently search for indicators like odd OS fingerprint or Time-To-Live (TTL) anomalies, traffic that appears to be internal but is actually coming from the outside, or asymmetric flows that don’t follow typical session patterns (e.g., answers without an outbound SYN).
- TCP Hardening: Although sequence numbers in older systems were occasionally predictable, upper layer protocols like TCP use them to make sure packets belong to an established connection. This serves as a defense against connection hijacking via spoofing.
- Coordination: Since spoofing prevention works best when widely implemented by upstream providers, it is beneficial to encourage Internet service providers (ISPs) to embrace BCP 38 (Best Common Practice for filtering).
You can also read ICMP Attacks Types: Ping Flood, Smurf & Tunneling Explained
