MSCHAPv2
Microsoft created the password-based authentication protocol known as MSCHAPv2 (Microsoft Challenge Handshake Authentication Protocol version 2), which is mostly used to secure remote access connections in Virtual Private Networks (VPNs) and with the Point-to-Point Protocol (PPP). MS-CHAPv1 is an enhanced and more secure version of the original MSCHAP protocol.
Often encountered in workplace networks and older VPN configurations (particularly PPTP), MSCHAPv2 is an older protocol that is extensively supported in Windows-based networking settings.
How MSCHAPv2 Works?
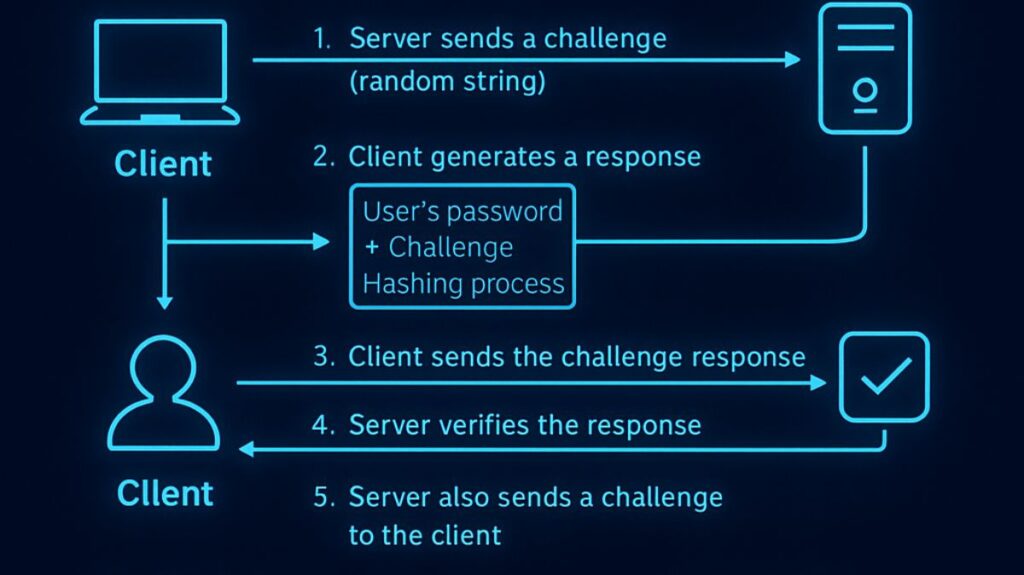
A challenge-response method is used by MSCHAPv2 to confirm the identification of the user or device:
- Challenge: To start the procedure, the server (authenticator) sends the client a 16-octet random string called the Challenge.
- Response Generation: Using a hashing method, the client creates a Response by merging the received Challenge, the user’s password, and their name. The MD4 and DES algorithms serve as the foundation for this procedure.
- Response Transmission: The client replies to the server with this encrypted and hashed response. Importantly, only a password-derived hash of the challenge is sent over the network; the password itself is never sent in plain form.
- Verification: The server, which is aware of the user’s password hash, confirms the client’s response by carrying out the same computation.
- Mutual Authentication: Mutual authentication was introduced by MSCHAPv2, in which the client receives a challenge from the server, and when a success packet is received, the peer (client) must confirm the authenticator (server). In the event that both checks are successful, the connection is verified.
Following successful authentication, the session keys required to encrypt the data link using the Microsoft Point-to-Point Encryption (MPPE) protocol are obtained using MSCHAPv2.
You can also read What Is Packet Switching In Networking And Advantages
Key Features and Capabilities
MSCHAPv2 includes several security and functional enhancements over its predecessor, MS-CHAPv1:
- Mutual Authentication: Man-in-the-middle (MITM) attacks are prevented by mutual authentication, in which the client and the server confirm each other’s identities.
- Password Protection: The use of cryptographic hashing to protect passwords makes them more secure than systems such as PAP (Password Authentication Protocol).
- Encryption Support: To protect credentials during transmission, it allows the authentication data exchange to be encrypted.
- Password Aging/Change Feature: If the RADIUS server indicates that the password has expired, MSCHAPv2’s Password Aging/Change Feature enables the client to update the account password.
Security Concerns and Modern Alternatives
Despite being more secure than MS-CHAPv1 or PAP, MSCHAPv2 has known security limitations that lead security experts to recommend against using it in isolation today.
- Vulnerabilities: The user’s password is a shared secret used by the protocol. The hashing structure, which is based on the NTLM password hash, is vulnerable to brute-force and offline dictionary attacks in the event that the handshake data is captured by an attacker.
- Lack of Robust Mutual Authentication (Standalone): Although MSCHAPv2 has a mutual authentication feature, Microsoft warns that this setup may not be secure when it is used without encapsulation (e.g., MS-CHAPv2/PPTP). When a client fails to adequately authenticate the server outside of a secure tunnel, the connection may be exposed to Man-in-the-Middle (MITM) attacks.
- Deprecation: Microsoft has frequently disabled MSCHAPv2 by default on contemporary OS systems when Credential Guard is activated as a result of these vulnerabilities.
You can also read What Is The Demarcation Point Definition In Networking?
Encapsulation (EAP-MSCHAPv2)
Almost all secure tunnels nowadays use MSCHAPv2 as the inner authentication technique, usually offered via PEAP (Protected Extensible Authentication Protocol), to counteract these cryptographic flaws.
- The MSCHAPv2 exchange is encapsulated within the EAP architecture by EAP-MSCHAPv2, enabling secure transit.
- First, a TLS/SSL tunnel is created when utilizing PEAP-MSCHAPv2 (which includes server-side certificate validation). In order to prevent the authentication exchange from being intercepted and cracked, the MSCHAPv2 challenge-response messages are thereafter transmitted encrypted within this TLS tunnel.
Current Best Practice: EAP-TLS
In enterprise settings, EAP-TLS (Extensible Authentication Protocol-Transport Layer Security) is the recommended authentication method for the highest level of security. Because EAP-TLS is certificate-based (passwordless), it provides more robust mutual authentication and completely removes the security vulnerabilities connected to password-based authentication.
Analogy: MSCHAPv2 on its own can be compared to mailing a locked box (the hashed challenge response). A skilled burglar who intercepts enough boxes may be able to pick the lock (brute-force the hash) despite the password not being written on the outside, since the locking mechanism (the cryptographic technique) is outdated. Comparable to placing the secured box inside an armoured delivery vehicle (the TLS tunnel) is PEAP-MSCHAPv2. Interception and subsequent breaking are nearly impossible due to the stronger external security layer protecting the entire exchange, even if the internal authentication system has flaws.
You can also read What is Local Loop in Networking and Supported Services
