Reconnaissance Attack

The first stage of a cyberattack is known as a reconnaissance attack, during which the attacker surreptitiously learns about the target in order to identify vulnerabilities and prepare a full-scale attack. Before attempting a break-in, a burglar “casing” a house to identify entrance points, security systems, and valuables is the cyber counterpart of that.
You can also read What Is A Network Security Threat? History, And How It Works
How it Works
Methodically gathering information on a target organization’s network, systems, and employees is how reconnaissance operates. A more focused and successful attack, like a malware distribution or phishing campaign, is then created using the information acquired.
The general process includes these steps:
Information Gathering: Information gathering is the process of compiling public data from sources such as public records, corporate websites, and social media.
Network Mapping: Network mapping is the process of determining the target’s network topology and IP address ranges.
Vulnerability Scanning: Finding open ports, active services, and known software flaws on the target’s systems is known as vulnerability scanning.
Data Aggregation: Data aggregation is the process of combining all the information gathered to create a thorough target profile that highlights the most promising assault avenues.
History
For millennia, military strategy has included the idea of reconnaissance. As the internet developed, so did cybersecurity. In the 1980s and 1990s, early hackers mapped networks using simple tools like ping and traceroute. Reconnaissance techniques evolved to incorporate increasingly complex techniques as networks and social media grew more prevalent; in the mid-1990s, IP spoofing and phishing became prevalent. In the Cyber Kill Chain, a model for the phases of a cyberattack, it is now a recognized and crucial step.
Importance
Reconnaissance is a crucial and dangerous phase of an attack because it helps the attacker:
Increase Success Rate: Attackers can modify their exploits for a better chance of success by being aware of the target’s vulnerabilities in advance.
Avoid Detection: To stay concealed, they can use strategies that are less likely to set off alarms, such as utilising information that is readily available to the public.
Maximize Impact: Attacks that steal valuable data or compromise vital systems using the information acquired may result in more serious harm.
Types of Reconnaissance Attacks
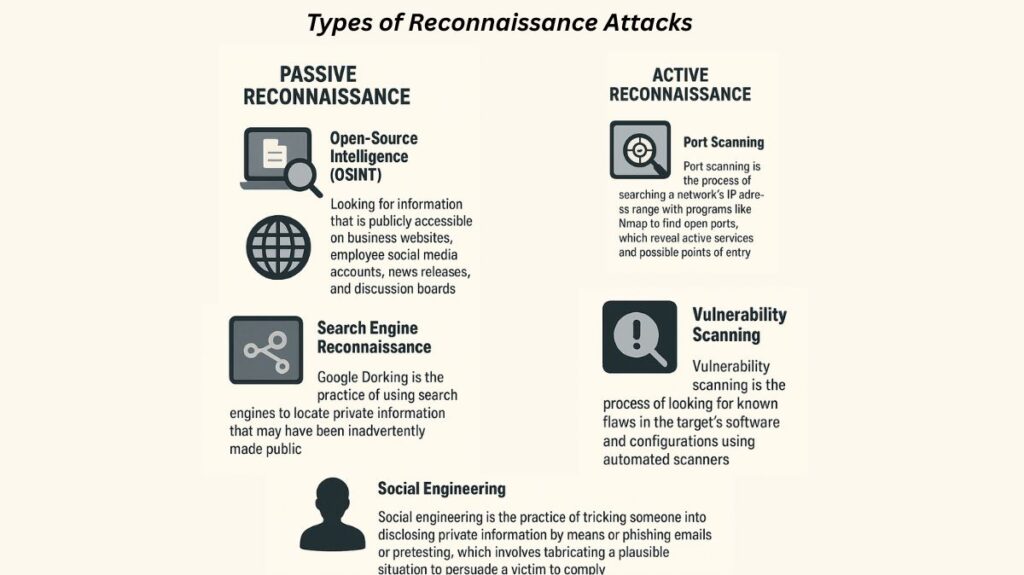
Reconnaissance is broadly categorized into two main types based on how they interact with the target.
Passive Reconnaissance
This approach entails obtaining data without interacting with the target’s systems directly. Since there is no direct communication with the network, it is low-risk and challenging to identify.
- Open-Source Intelligence (OSINT): Looking for information that is publicly accessible on business websites, employee social media accounts, news releases, and discussion boards.
- WHOIS Lookups: Searching open databases for information about a domain registration, such as DNS records and owner details.
- Search Engine Reconnaissance: Google Dorking is the practice of using search engines to locate private information that may have been inadvertently made public.
Active Reconnaissance
This approach, in which the attacker engages with the target system to collect data, is more straightforward and detectable. It produces more precise and useful information, but it is riskier.
- Port Scanning: Port scanning is the process of searching a network’s IP address range with programs like Nmap to find open ports, which reveal active services and possible points of entry.
- Vulnerability Scanning: Vulnerability scanning is the process of looking for known flaws in the target’s software and configurations using automated scanners.
- Social Engineering: Social engineering is the practice of tricking someone into disclosing private information by means of phishing emails or pretexting, which involves fabricating a plausible situation to persuade a victim to comply.
Social Reconnaissance
Through social engineering, attackers obtain details about the personnel and internal organization. This frequently entails gathering information via social media or even using honey trap methods.
Common Techniques and Tools
Port scanning: To locate open ports and identify services that are currently operating, tools such as Nmap are used to scan a network’s IP addresses.
Vulnerability Scanning: Vulnerability scanning is the process of using technologies to identify known security flaws in systems and software.
Information Gathering: Information gathering includes finding public IP addresses, listing subdomains, and searching for domain information (such as WHOIS lookups).
Social Media Analysis: Social media analysis is the process of gathering data about the company and its personnel from websites such as Facebook and LinkedIn.
Advantages
Bypasses Defenses: Because passive reconnaissance doesn’t communicate with the network, firewalls and intrusion detection systems are unable to detect it.
Higher Success Rate: An attacker’s primary attack will be more accurate and successful the more information they have.
Cost-Effective: A large quantity of information is publicly available, and many reconnaissance technologies are open-source or free.
Disadvantages
Time-Consuming: It can take a lot of time and work to get enough relevant data.
Risk of Detection: Active reconnaissance methods, such as port scanning, have the potential to create digital traces and set up security notifications.
Information Overload: The attacker may gather so much information that it is hard to sort through and locate essential information.
Applications
Cyberattacks: From straightforward phishing schemes to intricate nation-state-sponsored espionage, reconnaissance is the first and most important phase in almost all assaults.
Ethical Hacking & Penetration Testing: To test an organization’s defenses and find weaknesses before an actual attacker can take advantage of them, security experts employ reconnaissance tactics.
Business Intelligence: Depending on the information gathered, competitors may employ OSINT for competitive analysis, which may conflate legal and illicit behavior.
You can also read Types of Mitigation Techniques, How it Works and Advantages
