What is root guard?
In order to preserve the stability and integrity of a Layer 2 network topology, the Spanning Tree Protocol (STP) and Rapid Spanning Tree Protocol (RSTP) both include Root Guard, an essential network security feature. Enforcing the root bridge’s predefined position enhances switched network manageability and reliability.
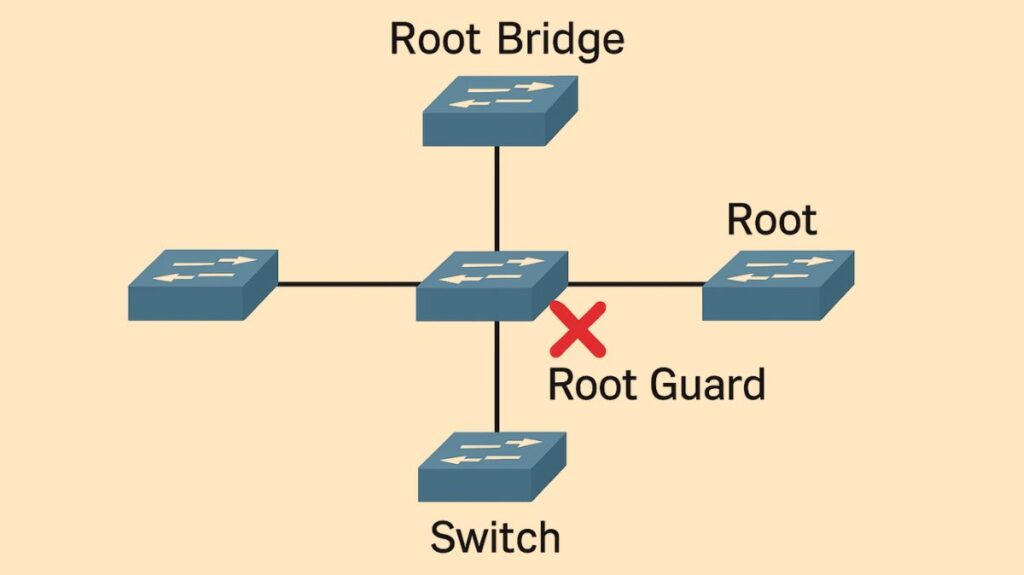
In STP, Root Guard protects your root bridge from unlawful switches.
Core Function and Purpose
The network administrator has no way to safely enforce the switched network’s topology using the conventional STP. Any bridge with a lower Bridge ID (BID) can be the root bridge, creating a poor forwarding topology. The forwarding topology depends on many aspects, including root bridge position.
Root Guard fixes this flaw:
- Root location Enforcement: The functionality offers a means of enforcing the network’s root bridge location. The area of the network where the STP root can be found can have a perimeter set up by administrators.
- Root Guard prevents unauthorized or misconfigured switches from overriding the root bridge. By transmitting superior Bridge Protocol Data Units (BPDUs), it stops any switch from taking over as the new root bridge.
- The root guard keeps the port it activates on the selected port. It stops a Root Port (RP) from being a Designated Port.
- The network must be protected from problems brought on by a “rogue root bridge” or a configuration error, like an access layer switch assuming the root role and directing data traffic over slower links.
Also Read About Advantages And Disadvantages Of SNMP, How SNMP Work
How it Works?
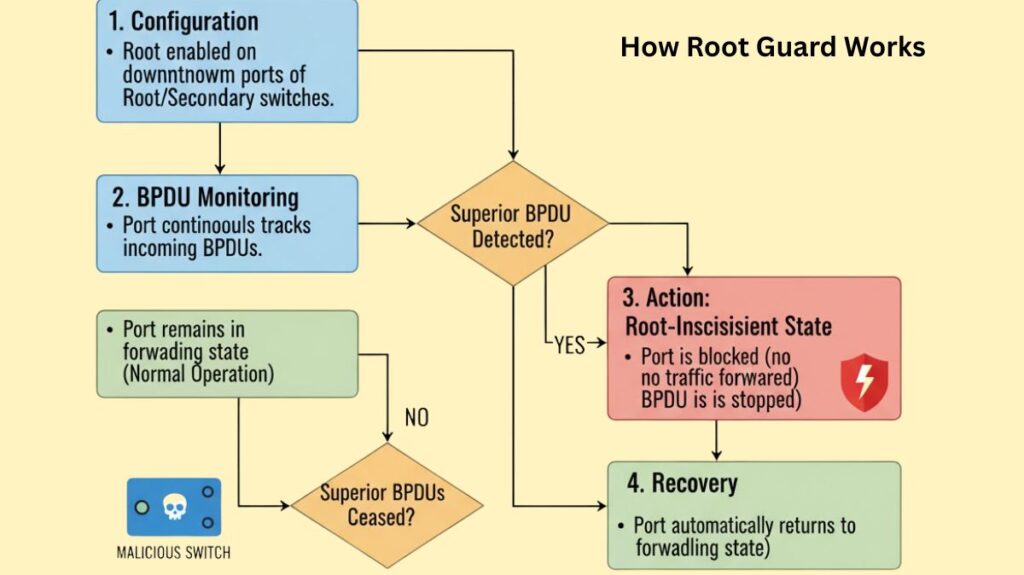
- Configuration: Switch ports that link to switches that shouldn’t be the root bridge or have any impact over the root election have Root Guard set up. On your primary and secondary root switches’ allotted ports, point downstream to other switches.
- Ports monitor incoming Bridge Protocol Data Units (BPDUs).
- Superior BPDU Detection: The Root Guard feature activates if the port receives a superior BPDU, which claims a better root path than the root switch.
- Action: A Root-Inconsistent state is applied to the port right away.
- The port is essentially stopped and ceases to forward traffic while it is in the Root-Inconsistent state.
- By doing this, a network topology recalculation is avoided and the undesirable switch is prevented from becoming the new root bridge by stopping the superior BPDU from spreading further.
- Recovery: Until the superior BPDUs are no longer received, the port will stay in the Root-Inconsistent condition. The port will automatically return to its typical forwarding state as soon as the BPDUs return to their typical (inferior) condition.
Also Read About What is Dynamic ARP Inspection, How it Works & Configuration
Root guard configuration
Placement Methodology
Root Guard should be activated on interfaces that link to other switches, notably edge or access layer switches, where the root bridge should not be. It is discouraged on main core switch links. It must be enabled on all ports where the root bridge cannot be seen.
Cisco Setup
Interface configuration commands are used to set up Root Guard. Keep in mind that the precise command differs slightly based on the IOS version and Cisco platform:
| Platform | Command Example | Notes |
|---|---|---|
| Catalyst 6500/6000 and 4500/4000 (Newer IOS) | spanning-tree guard root | This command is used in all releases for Catalyst 4500/4000. |
| Catalyst 2900XL/3500XL, 2950, 3550 | spanning-tree rootguard | This command is used on these older platforms. |
Newer Cisco Catalyst Series switches and different Cisco IOS software versions support the capability.
Root Guard vs BPDU Guard
Despite being STP security upgrades, Root Guard and BPDU Guard have different uses and implementations:
| Feature | Primary Goal | Action When Triggered | Recovery | Typical Placement |
|---|---|---|---|---|
| Root Guard | Prevents a switch from becoming the root bridge. | Puts the port into the root-inconsistent state (blocking traffic but listening for BPDUs). | Automatic. | Designated ports on core/distribution switches connecting to other switches that should not be the root. |
| BPDU Guard | Prevents any BPDU transmission on access/edge ports. | Puts the port into a permanent errdisable state (administratively shut down). | Manual reenable or configured errdisable-timeout is required. | Access ports configured with PortFast, connecting to end-user devices. |
BPDU Guard restricts STP participation if a BPDU is received, but it allows participation if the device does not try to become root.
UniDirectional connection Detection (UDLD) and loop guard address STP loops caused by unidirectional connection failures (the “two roots problem”). Root Guard cannot fix these loops. Moreover, a switch that has Root Guard activated cannot have Loop Guard enabled on it.
Also Read About What is Port Security and Benefits of Port Security
