Smurf attack meaning
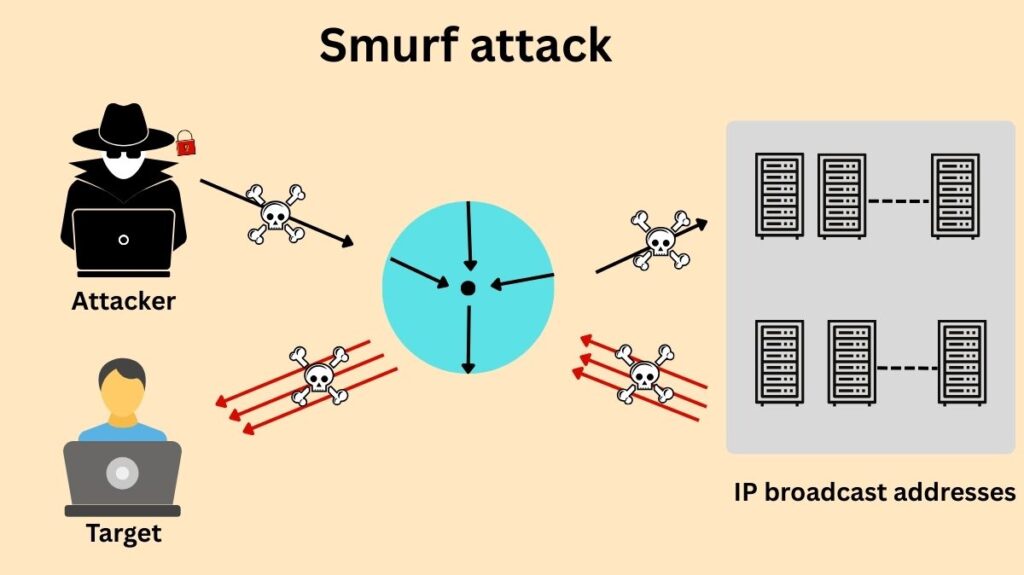
A Smurf attack is a type of distributed denial-of-service (DDoS) attacks that floods a targeted system with increased traffic by taking use of flaws in IP broadcast addresses and the Internet Control Message Protocol (ICMP). It functions at Layer 3, or the network layer.
The concept of small, numerous attackers (similar to the Smurfs cartoon characters) overwhelming a much larger opponent is the inspiration behind the attack’s name. Dan Moschuk (also known as TFreak) created the first Smurf attack creation program in 1997.
How a Smurf Attack Works
An amplification loop is produced by a Smurf attack using IP spoofing and IP broadcasting:
Spoofing: An ICMP “echo request” packet (a ping) is created by the attacker. This packet is purposefully created by the attacker using a spoof source IP address, which is the real IP address of the target.
Broadcasting: Instead of sending this spoof packet to a single device, the attacker transmits it to an IP broadcast address of a router or network. Every device on that network segment can receive and process a single packet to a broadcast address.
Amplification (The Reply Flood): The broadcast network sends the ICMP echo request to every server on the network after receiving the fake request. After that, every network device (or host) responds with an ICMP echo reply. All of these responses are sent back to the victim because the source IP was impersonated as their address.
Denial of Service: A huge flood (deluge) of ICMP echo replies from multiple hosts overwhelms the target, utilizing up its resources and bandwidth and perhaps resulting in the system crashing or going down.
It is comparable to a prankster phoning an office manager, posing as the CEO, and requesting that the manager instruct all staff members to contact the “CEO” (the victim’s number) back with an update.
Also Read About What Is A Baiting Attack And How Does Baiting Attacks Work
Amplification Factor
The amplification effect makes the attack successful. The number of devices (n) on the targeted broadcast network is multiplied by the attacker’s initial tiny packet.
- If both the source and destination addresses are broadcast addresses (an amplification factor of n²), a single ping can force a network with 100 hosts to process 10,000 packets.
- Very large networks with hundreds or thousands of hosts can produce amplification of more than 100 times, and typical amplification factors reported can vary from 20X to 70X. This enables attacks surpassing 1 Gbps to be produced by a low-bandwidth attacker.
Impact of a Smurf Attack
A successful Smurf attack has serious repercussions, such as:
- Service Outages: Applications and websites may experience total service outages if target networks are rendered unusable.
- Network Saturation: The communication network becomes paralysed when the deluge of traffic uses up all of its bandwidth.
- Resource Exhaustion: In order to process the large number of ICMP replies, the victim system’s resources (such as CPU and RAM) are used up.
- Business Losses: Lost sales and revenue are a direct result of downtime.
- Reputation Damage: When services are regularly unavailable, users may come to distrust them.
Also Read About Advantages And Disadvantages Of Packet Filtering Firewall
Smurf Attack Prevention
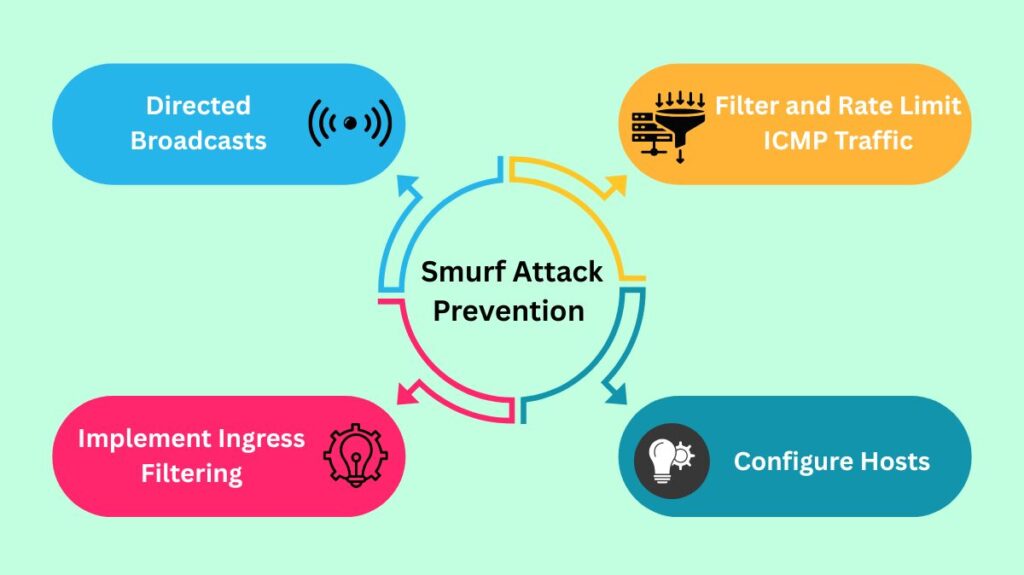
Proper network configuration is necessary for the traditional Smurf attack repair. Hardening network infrastructure is the main focus of preventative methods because the attack depends on improperly designed networks being utilised as “Smurf amplifiers”:
Disable IP Broadcast Forwarding (Directed Broadcasts): The most important precaution is to turn off IP broadcast forwarding, often known as directed broadcasts. Broadcast packet forwarding must be turned off on network routers. Although this is frequently turned off by default on modern routers, networks that are outdated or improperly configured may still be at risk.
Implement Ingress Filtering (BCP 38): At the network edges, ISPs and network operators should reject attacking packets based on their falsified source address, which is the victim’s IP.
Filter and Rate Limit ICMP Traffic: Incoming ICMP echo requests from outside networks can be prevented by configuring firewalls and routers. By using rate limitation, ICMP packet flow is managed to keep the network from becoming overloaded.
Configure Hosts: When a packet’s destination address is a broadcast address, hosts and routers can be set to ignore it.
Modern Relevance
The late 1990s saw a lot of successful smurf attacks. Today, the original Smurf attack is much less feasible due to the widespread adoption of remedies, such as turning off directed broadcasts.
Nonetheless, many modern DDoS amplification methods (such as DNS and NTP amplification) are still based on the broad idea of amplification via third parties. The following contemporary security issues resurrect the Smurf threat:
IoT Device Exploitation: Since many IoT devices come with default settings that react to ICMP requests, the proliferation of IoT devices offers new possible reflection points.
IPv6 Architecture: Traffic can be multiplied by taking advantage of IPv6’s enhanced multicast capabilities.
Cloud Infrastructure: Reflection assaults are more likely to occur in public cloud environments with shared network infrastructure.
Advanced Attacks: To find weak networks, change source addresses, and initiate multi-vector attacks that blend Smurf and other DDoS techniques, contemporary attackers employ advanced automation and artificial intelligence.
Similar to the Smurf attack, the Fraggle attack uses UDP packets directed at ports 7 (Echo) and 19 (CHARGEN) for amplification rather than ICMP echo requests.
Also Read About Man In The Middle MitM Phishing Attacks And How It Works?
