What is SSL stripping Attack?
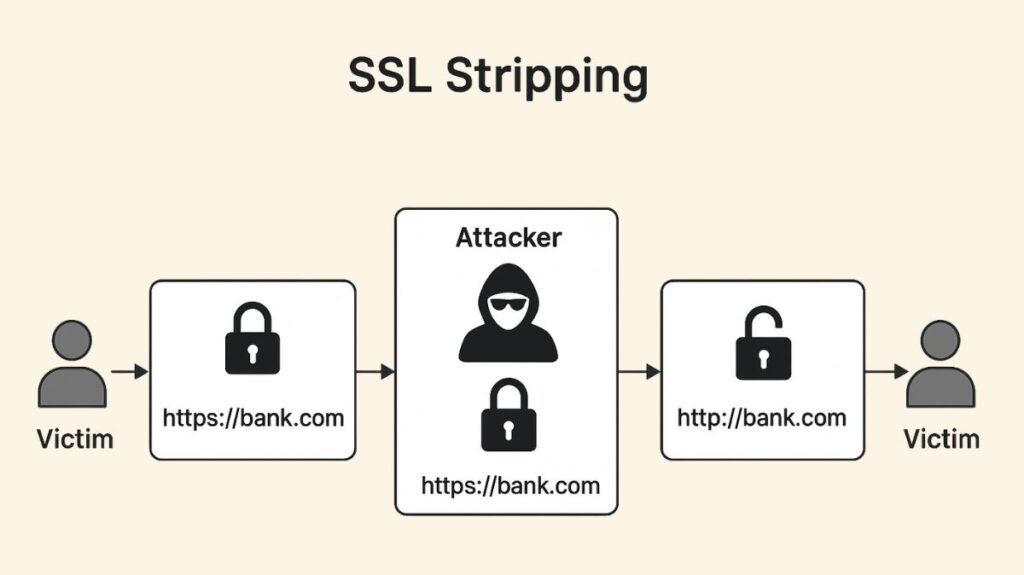
SSL stripping, also known as an SSL downgrade attack or HTTP downgrade attack, is a significant security threat categorized as a Man-in-the-Middle (MITM) attack technique.
SSL stripping’s main objective is to convert a victim’s secure HTTPS connection to an unencrypted HTTP connection without the victim’s knowledge. This effectively “strips” away the SSL/TLS protocol’s encryption, giving the attacker the ability to intercept, view, read, and alter all transmitted data in plain text.
The technique was first publicly suggested by American computer security researcher Moxie Marlinspike at Black Hat 2009.
You can also read What Is VLAN Hopping Attack? How Does VLAN Hopping Work
How SSL Stripping Attacks Work
The first, vulnerable stage of a web connection is exploited by SSL stripping. The method is based on the observation that when a person inputs the address of a website, their browser frequently tries to connect using the risky HTTP protocol first, before switching to HTTPS.
The attack unfolds through the following sequence of steps:
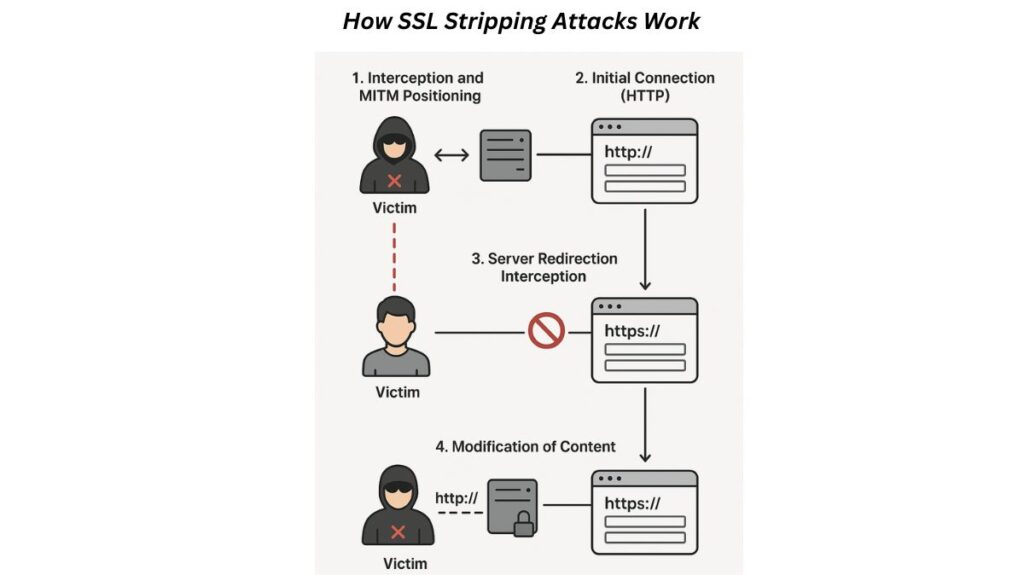
- Interception and MITM Positioning: The attacker initially places themselves in the middle of the genuine server and the victim. ARP spoofing, DNS cache poisoning/spoofing, or configuring a hostile Wi-Fi hotspot are some of the MITM techniques that are commonly used in conjunction with SSL stripping to obtain this first access.
- Initial Connection (HTTP): The victim’s browser uses the unencrypted HTTP protocol to send a first request to the target website.
- Server Redirection Interception: In a typical scenario, the authentic server would reply to this HTTP request by sending a redirect command (such as a 302 redirect) telling the browser to switch to the secure HTTPS protocol right away. This command to reroute is intercepted by the attacker.
- The Downgrade (Stripping): The attacker creates two distinct connections at the same time by using a proxy server, which serves as a “bridge.”
- The attacker poses as the user while keeping a secure HTTPS connection with the authentic server.
- The attacker impersonates the website while maintaining an insecure HTTP connection with the victim’s browser.
- Modification of Content: The attacker analyzes the packets, modifies the TCP/IP responses, and actively removes or alters any requests to use HTTPS (i.e., strips the redirection). The attacker also rewrites all links on the webpage from
https://tohttp://before forwarding the content to the user.
- Data Exposure: By tricking the user’s browser into thinking that there isn’t a secure HTTPS version of the website, this modification forces the browser to keep communicating via the plain text HTTP connection. Any important information the user sends such as credit card numbers or login credentials is transmitted in plaintext to the attacker, who logs it before securely sending it to the actual server. The person is still not aware that their info has been compromised.
You can also read What Is MAC Flooding Attack And Prevention Techniques
Risks and Consequences
Because they enable attackers to function covertly and prevent victims from realizing that their security has been compromised, SSL stripping attacks are extremely risky.
The consequences include:
- Stolen sensitive information: Financial data, sensitive business data, login credentials, and personally identifiable information (PII) are all sent in unencrypted and are susceptible to interception.
- Identity theft and account compromise: Credentials can be obtained by attackers to gain unauthorized access to accounts.
- Data Manipulation and Fraud: An attacker may change the information that is communicated or sent back to the user, possibly inserting malicious content, rerouting users to phishing websites, or even altering transaction information.
- Loss of Trust: Successful assaults can cause users to lose faith in a company and harm its reputation.
Detection and Prevention
Because the user thinks they are securely interacting with the website (or that a secure connection is unavailable) and the server thinks it is securely communicating with the attacker, SSL stripping is hard for both users and servers to detect.
Prevention for Website Owners (The Most Effective Defense)
In order to avoid SSL stripping on the server side, HTTP Strict Transport Security (HSTS) must be implemented.
- The browser is forced to switch to an HTTPS connection via HSTS, even if the web server tries to deliver HTTP content.
- The browser will never try to connect to that website insecurely via HTTP again after HSTS information has been saved.
- To ensure security even before the initial connection attempt, administrators can submit their domain to the HSTS preload list that is included into widely used browsers.
- Using HTTPS for all pages on a website not just sensitive ones is also essential for patching vulnerabilities.
Detection and Mitigation for Users
Users can employ both detection and mitigation strategies:
- Vigilance: Users should always look for the padlock symbol and verify that the URL begins with
https://before entering confidential information.
- VPN Use: By stopping the attacker from carrying out the initial MITM assault (such as ARP spoofing or DNS cache poisoning) necessary for SSL stripping, a Virtual Private Network (VPN) can lessen the impact of the attack. This is particularly crucial while utilizing public Wi-Fi sites.
- Browser Warnings: Users should be aware of any warnings, certificate issues, or signs that the connection is “not secure.”
You can also read What Is A Pharming Attack? How To Prevent Pharming Attacks
