What is Wi-Fi eavesdropping?
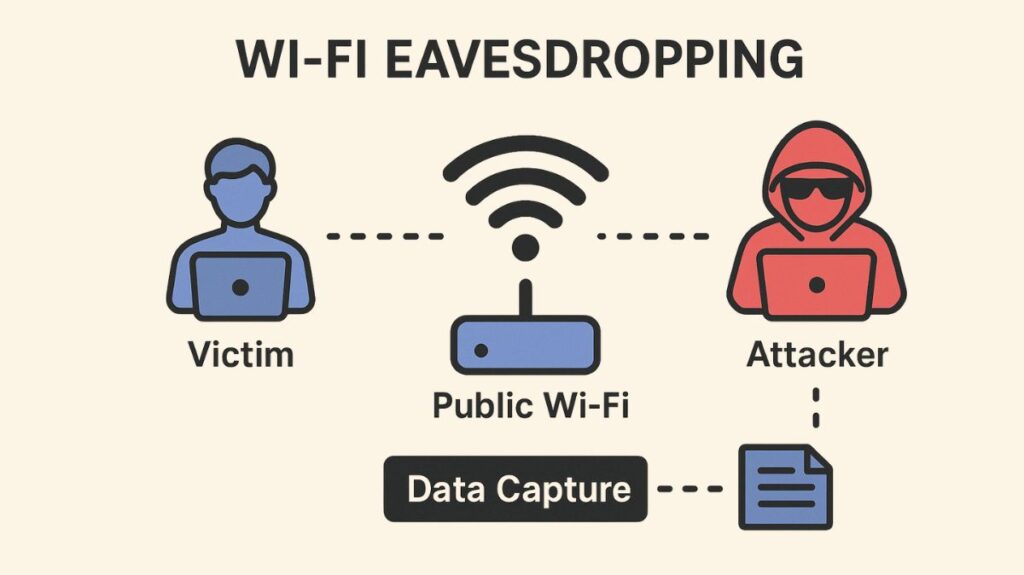
A cyberattack known as Wi-Fi eavesdropping, sometimes called Wi-Fi sniffing or snooping, entails the unlawful interception of data packets sent across a wireless network. Wi-Fi signals can be picked up by anyone nearby with the right equipment because they flow through the air.
Sensitive information like login credentials, personal information, financial information, credit card numbers, emails, and company information are the main targets of this attack. Users are particularly concerned about it if they regularly connect to unprotected or inadequately secured Wi-Fi networks, such as public hotspots in coffee shops, airports, and lodging facilities.
Also Read About SYN Flood Attack And Mechanism Of The SYN Flood Attack
How Wi-Fi Eavesdropping Works?
Wi-Fi eavesdropping works by recording wireless communications and examining the information they contain.
- Data packets sent over the wireless network are intercepted at the start of the operation.
- Packet Sniffing: To obtain the raw data packets, attackers employ specialised programs called packet sniffers (such as CommView or Wireshark).
- Data Extraction: An attacker can readily read, examine, and steal data that has been transferred without encryption. Each wireless frame’s data payload is jumbled by encryption, making it impossible for anyone in the middle to read it.
Common Eavesdropping Techniques
Often classified as a form of network eavesdropping, Wi-Fi eavesdropping often uses advanced active tactics, especially Man-in-the-Middle (MitM) attacks:
Man-in-the-Middle (MitM) Attacks
An eavesdropper breaches the network system and intercepts and transmits communications between two parties in a MitM attack. The attacker monitors or modifies the data flow while acting as a mediator in the communication, giving the impression that the sender and recipient are speaking directly.
Rogue Access Points (Evil Twins)
The most common technique for Wi-Fi eavesdropping is this one. It entails creating “evil twins,” or rogue Wi-Fi hotspots, that imitate trustworthy networks.
Creation of a Fake Network: A rogue Wi-Fi access point that imitates a genuine one is set up by the attacker to create a fake network. As an example, they give it the same SSID as a public network: “Starbucks_Guest_Wi-Fi.”
Luring Victims: To make their phoney network seem like the most dependable choice, the attacker frequently utilises a gadget with a better signal. Additionally, they may employ a method that forces users’ devices to automatically look for and connect to the evil twin by cutting them off from the real network.
Data Interception: All of your internet traffic is passed through the attacker’s equipment as soon as you join the phoney network. This gives them the ability to track and intercept all of your data, particularly when you visit unencrypted websites (HTTP). Additionally, they can downgrade safe connections (HTTPS) to insecure ones via methods like SSL stripping, which exposes your data.
Because they are inexpensive and simple to set up, fraudsters commonly employ tools like Wi-Fi Pineapples to construct these rogue access points.
Also Read About ICMP Attacks Types: Ping Flood, Smurf & Tunneling Explained
SSL Stripping and Cleartext Exploitation
Users may be forced to downgrade secure HTTPS connections to insecure HTTP by attackers using a MitM attack (a technique known as SSL stripping). This gives the attacker access to private information in cleartext, or unencrypted, form.
Risks and Consequences
Wi-Fi eavesdropping puts people and organisations at serious risk in a number of ways:
- Financial Loss and Identity Theft: Direct financial theft may result from the theft of login credentials, credit card numbers, and banking information.
- Data Breach and Espionage: Workers who connect to hostile networks run the danger of exposing private company information, putting the company’s security and intellectual property at risk.
- Conversations Compromise: Interception and manipulation are two ways that confidential conversations might be jeopardised.
- Phishing and malware: Connected devices can be compromised by manipulating intercepted data streams to contain malware. Additionally, users may be tricked by fake networks into divulging personal information that is exploited in phishing scams.
Preventing Wi-Fi eavesdropping
Using encryption to secure the wireless network is crucial to preventing Wi-Fi eavesdropping. Effective actions consist of:
How to Keep Yourself Safe
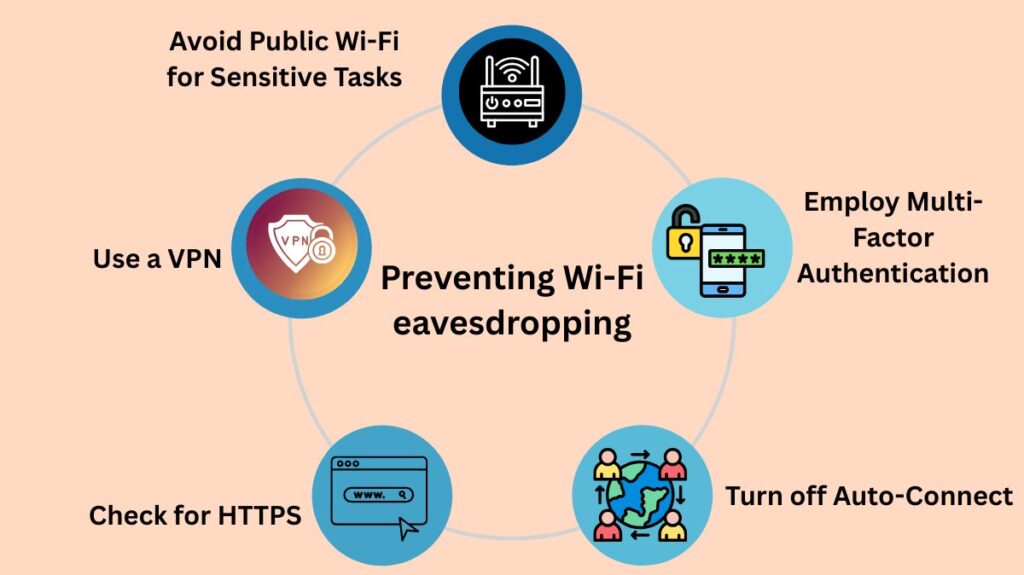
- Avoid Public Wi-Fi for Sensitive Tasks: Avoid using public Wi-Fi networks for sensitive tasks like online banking, shopping, or email account login.
- Use a VPN: A Virtual Private Network (VPN) A VPN encrypts all of your online communications. By doing this, your data is protected by a private, secure tunnel that prevents anyone who might be listening in on the network from reading it.
- Check for HTTPS: Verify that the website URL you are seeing begins with https:// and has a padlock icon in the address bar. This is known as HTTPS. This means that you have an encrypted connection to the website.
- Turn off Auto-Connect: Set up your gadgets so they don’t join known Wi-Fi networks on their own. By doing this, you can stop your gadget from inadvertently becoming a part of an evil twin network.
- Employ Multi-Factor Authentication (MFA): MFA offers an essential second layer of security, keeping hackers out of your account even if they manage to steal your password.
Also Read About How Does Pretexting Work and Examples of Pretexting
