What is Wireless Security Protocols
The IEEE 802.11 standard details specifications for wireless security protocols, network topologies, and spectrum allocation. Securing a wireless network is crucial because data transmitted over the air can be easily overheard by anyone within range. An effective wireless security strategy focuses on identifying endpoints and users, and protecting wireless data from tampering and eavesdroppers.
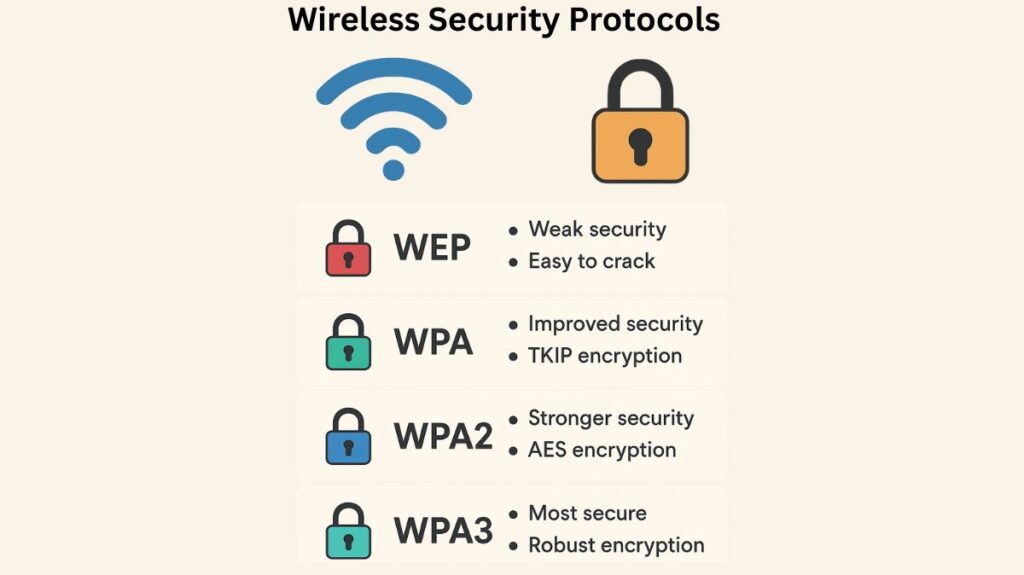
A message integrity check (MIC), encryption, and authentication are the essential elements needed for a secure wireless connection. Several versions of protocols, mostly certified by the Wi-Fi Alliance (WPA, WPA2, and WPA3), have contributed to the evolution of wireless security.
You can also read How Data Encryption Standard Works and Key Characteristics
Legacy and Deprecated Security Protocols
Open Authentication and Shared Key Authentication with WEP were the two fundamental options for client authentication provided by the original 802.11 standard. These techniques are now mostly regarded as outdated or ineffective.
Open Authentication
- With open authentication, all that is needed to connect to an Access Point (AP) is an 802.11 authentication request, providing unrestricted access to a WLAN.
- Its sole purpose is to confirm that the client is an 802.11 device; other methods, like a Virtual Private Network (VPN), are required for user identity authentication.
Wired Equivalent Privacy (WEP)
- WEP was the initial standard method defined in 802.11 to provide a security level “equivalent” to a wired connection.
- Encryption: The RC4 stream cipher algorithm is used by WEP.
- Keys: The client and AP must first exchange the same key (a 40-bit or 104-bit WEP key) in order to use this shared-key security technique.
- Vulnerability: Because of its well-known flaws, WEP was formally deprecated by the 802.11i amendment in 2004, rendering it extremely susceptible to compromise. Using it on a wireless network is not advised.
Temporal Key Integrity Protocol (TKIP)
- When WEP was known to be weak and the immediate implementation of more robust techniques was hindered by hardware constraints, TKIP was created as a stopgap expedient.
- It was the main encryption technique employed by the original Wi-Fi Protected Access (WPA) version.
- The underlying WEP RC4 encryption cipher is upgraded to 128-bit encryption via TKIP.
- TKIP incorporated several important security improvements, such as:
- To stop manipulation, use a Message Integrity Check (MIC).
- To help stop brute-force attacks, the Initialization Vector (IV) was doubled from 24 bits to 48 bits.
- A technique for key mixing that generates a distinct 128-bit WEP key for every frame.
- Status: If a better approach is available, TKIP should be avoided as it was deprecated in the 802.11-2012 standard.
Modern Wireless Protocols (WPA2 and WPA3)
WPA Version 2 (WPA2)
- Based on the full 802.11i amendment, WPA2 is the second iteration of the Wi-Fi Alliance standard.
- WPA2 employs the improved Advanced Encryption Standard (AES) algorithm for encryption and integrity.
- The Counter/CBC-MAC Protocol (CCMP) is the particular technique employed. For message integrity, CCMP combines Cipher Block Chaining Message Authentication Code (CBC-MAC) with AES counter mode encryption.
- The preferred technique over WPA, which makes use of TKIP, is WPA2.
WPA Version 3 (WPA3)
- WPA3, introduced in 2018, is the newest version designed to replace WPA2 by adding superior security mechanisms.
- Encryption and Integrity: WPA3 combines the Galois/Counter Mode Protocol (GCMP) with more robust AES encryption. Compared to CCMP, GCMP is thought to be a more effective and safe authenticated encryption suite.
- Protected Management Frames (PMF): In order to safeguard 802.11 management frames and stop malicious activity like spoofing, WPA3 mandates the use of PMF.
Authentication Modes
Personal mode (PSK) and Enterprise mode (802.1X) are the two main client authentication options that WPA, WPA2, and WPA3 support, depending on the deployment scale.
Personal Mode (PSK/SAE)
- Personal mode is usually meant for use at home or in small office/SOHO settings.
- The Pre-Shared Key (PSK), a key string set up on each client and access point, is the foundation of WPA/WPA2-Personal. AES-CCMP encryption is used by WPA2-Personal.
- Simultaneous Authentication of Equals (SAE) is used by WPA3-Personal.
- To prevent brute-force or dictionary attacks against the four-way handshake, an exploit that can occur in WPA/WPA2-Personal modes, SAE fortifies the key exchange procedure.
- Additionally, WPA3-Personal offers forward secrecy, which prevents hackers from decrypting data that has already been sent over the air, even if the password is stolen.
Enterprise Mode (802.1X/EAP)
- An Authentication Server (AS), often a RADIUS server, is necessary for centralized authentication in enterprise mode, which is designed for large networks.
- The IEEE 802.1X standard, a port-based access control mechanism, is used in this mode. The authentication framework of 802.1X is based on the Extensible Authentication Protocol (EAP).
- WPA3-Enterprise uses a 192-bit cryptography suite to provide excellent security.
- Methods of EAP Authentication (Applied in the 802.1X framework):
- EAP-TLS (EAP Transport Layer Security): The most secure approach is EAP-TLS (EAP Transport Layer Security), which necessitates the installation of digital certificates on each client device as well as the authentication server (AS). A Public Key Infrastructure (PKI) must be set up.
- PEAP (Protected EAP): Constructs a secure tunnel using Transport Layer Security (TLS). Compared to EAP-TLS, deployment is simpler because just the AS needs a certificate.
- EAP-FAST (Flexible Authentication via Secure Tunneling): Cisco created EAP-FAST, or Flexible Authentication via Secure Tunneling, to accomplish EAP-TLS security levels without the need for certificates. For mutual authentication, it makes use of a Protected Access Credential (PAC).
Open Network Security
By mandating the use of Opportunistic Wireless Encryption (OWE), which encrypts all wireless communication even in the absence of authentication, WPA3 further improves security for open or public Wi-Fi networks.
Summary Comparison of WPA Generations
| Feature | WPA | WPA2 (802.11i) | WPA3 |
|---|---|---|---|
| Authentication (Personal) | Pre-Shared Key (PSK) | PSK | Simultaneous Authentication of Equals (SAE) |
| Authentication (Enterprise) | 802.1X/EAP | 802.1X/EAP | 802.1X/EAP |
| Encryption/MIC | TKIP/MIC (RC4-based) | AES/CCMP | AES/GCMP (GCMP-256 for Enterprise) |
| Key Management | Dynamic key management | Dynamic key management | Forward Secrecy, PMF required |
| Status | Avoid/Deprecated | Recommended minimum | Recommended/Highest Security |
You can also read What Is iBGP? Features, Advantages & How To Configure iBGP
