What is WPA2 Enterprise
The highest level of security for Wi-Fi networks is WPA2-Enterprise, sometimes known as WPA2-802.1X or 802.1X Mode. It is especially designed for big firms, corporations, universities, government agencies, and other establishments that need strong security and centralized user authentication.
WPA2-Enterprise employs distinct, personalized credentials (such a username/password or certificate) for authentication for each user or device, in contrast to WPA2-Personal (PSK), which depends on a single common password for all users.
You can also read Wireless Local Area Network WLAN Creation and Components
Core Architecture and Protocols
The IEEE 802.1X standard is used by WPA2-Enterprise for network access control and authentication. The 802.1X standard uses a three-party architecture and enables identity-based networking.
Three Essential Components
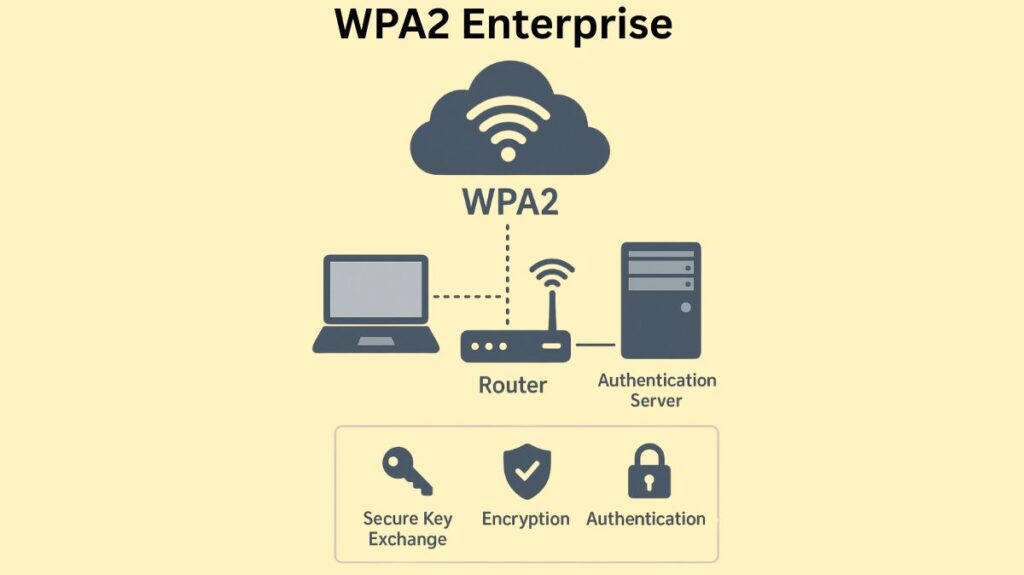
The WPA2-Enterprise structure requires three primary components to function:
- Supplicant (The Client): The device (such as a laptop or phone) requesting network connectivity is known as the supplicant (the client). Usually, the supplicant executes client software on the operating system and supplies the credentials.
- Authenticator (The Access Point or WLC): This device serves as a proxy and manages the connection port. It provides the server with the supplicant’s identity. The authenticator function in a wireless network is usually performed by the Access Point (AP) or Wireless LAN Controller (WLC).
- Authentication Server (The RADIUS Server): The authentication server, often known as the RADIUS server, is the main server that centrally controls network access regulations and compares user credentials to a database (such as Active Directory). Typically, it is a server for the Remote Authentication Dial-In User Service (RADIUS). This mode requires the infrastructure of a RADIUS server.
Authentication Framework
The Extensible Authentication Protocol (EAP) framework is integrated into the 802.1X standard. The real authentication framework for safely transferring credentials is called EAP. EAP supports a number of specialized techniques, including PEAP and EAP-TLS.
The Authentication and Key Generation Process
The authentication process, driven by 802.1X, works as follows:
- Initiation: The Supplicant makes an effort to establish a connection with the Authenticator (AP).
- Identity Exchange: Using the supplicant’s credentials or certificate, the authenticator asks for their identity. To connect with the AP, the supplicant first utilizes Open Authentication.
- Verification: The Authenticator communicates with the Authentication Server (RADIUS) via EAP to transmit the identity data. The credentials are then verified by the RADIUS server using its user database.
- Access Grant & Key Derivation: After authentication is successful, the RADIUS server provides access and returns to the Authenticator a secret key called the Pairwise Master Key (PMK). The identical PMK is likewise derived by the Supplicant.
- Secure Session: The WPA2 4-Way Handshake, which dynamically creates a distinct temporary session key (PTK/GTK) for data encryption, is then carried out by the Authenticator and Supplicant using this PMK.
You can also read Cisco WLC GUI Security Settings And Advanced WLAN Settings
Security and Key Management
WPA2-Enterprise offers enterprise-grade security due to several key features:
- Individual Authentication: To connect, each user needs a distinct login, password, or digital certificate. With this method, the vulnerability brought on by a single hacked password is avoided.
- Dynamic Key Management: Every user’s session key is created by the system on the fly. In the case that a single Pre-Shared Key (PSK) is compromised, this stops one user from decrypting another’s intercepted traffic, which is a serious security vulnerability.
- Encryption: WPA2-Enterprise uses the Counter Cypher Mode with Block Chaining Message Authentication Code Protocol (CCMP) in conjunction with the Advanced Encryption Standard (AES) for encryption. Data integrity and secrecy (encryption) are both offered by AES-CCMP.
- Centralized Control: By centralizing the administration of user credentials, the RADIUS server makes it possible to immediately revoke access for particular users and makes user tracking and access control easier.
Certificate-based authentication (CBA), which does away with passwords and employs digital certificates for security, is another way to improve WPA2-Enterprise. EAP-TLS, for instance, is a very secure EAP technique that necessitates certificates on both the authentication server and the client.
Configuration and Requirements
Wireless LAN Controller (WLC) configuration
To configure WPA2-Enterprise on a WLAN using a WLC interface:
- In the Layer 2 Security settings, choose 802.1X.
- After that, wireless clients will be authenticated against one or more RADIUS servers using 802.1X and EAP.
- The WLAN needs to be set up and connected to a RADIUS server. The IP address or addresses of the RADIUS server or servers should be used to configure the WLC.
- As a middleware device, the WLC manages communication with the authentication server via EAP and regulates user access via 802.1X. The WLAN configuration allows for the configuration of up to six distinct RADIUS servers.
Key Differences from WPA2-Personal
| Feature | WPA2-Personal (PSK) | WPA2-Enterprise (802.1X) |
| Authentication | Single Pre-Shared Key (PSK) for everyone. | Unique credentials (username/password or certificate) per user/device. |
| Server Needed | No, the router handles it. | Yes, a RADIUS Server is required. |
| Key Management | All users can decrypt all captured traffic if the single PSK is compromised. | Unique session keys are dynamically generated for each user, preventing one user from decrypting another’s traffic. |
| Target Environment | Homes and Small Offices. | Large Organizations and Corporations. |
| Security Level | Strong (if PSK is strong) | Strongest (Enterprise-grade security) |
You can also read WPA2 or WPA3: Wi-Fi Protected Access 3 security improvements
