What is native VLAN?
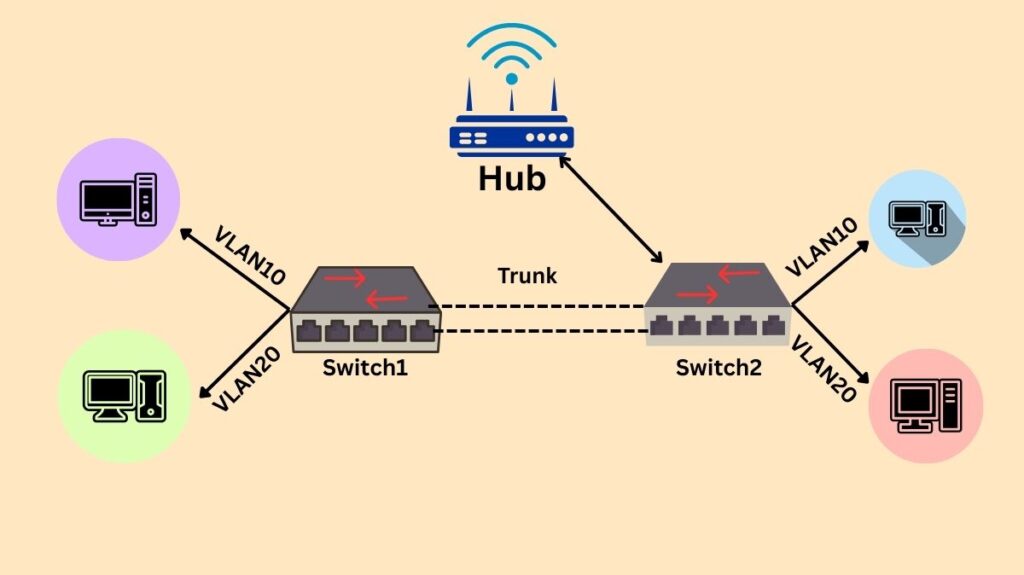
A network trunk link, which is a connection between two switches intended to have numerous VLANs, is traversed by untagged traffic via a Native VLAN, a unique VLAN. In order to ensure correct handling and prevent packet loss, devices that do not support VLAN tagging can nonetheless send traffic by allocating untagged frames to the Native VLAN. Many switches utilize VLAN 1 by default for this, however in order to prevent VLAN hopping attacks, it is best practice to switch the Native VLAN to a different one. especially related to trunk connectivity for IEEE 802.1Q.
How It Works
Untagged Traffic Handling: All frames from tagged VLANs are transmitted via a trunk link with a VLAN tag, which serves as an identifier for the particular VLAN. It frames are transmitted without a tag.
Backward Compatibility: To accommodate legacy devices that are unable to comprehend 802.1Q VLAN tagging, it was created.
VLAN Tagging: To identify which VLAN an Ethernet frame belongs to, the 802.1Q standard appends a VLAN tag to it when it contains other VLAN IDs.
Assignment of Untagged Frames: A switch assigns an untagged frame to the locally specified Native VLAN when it receives it on a trunk connection.
Purpose and Why it Exists
Backward Compatibility
The idea was developed to work with outdated systems or older devices that don’t support or comprehend VLAN tags (802.1Q VLAN tagging). It enables communication between an 802.1Q trunking port and a non-trunking device by transmitting frames for the Native VLAN untagged, which the older device may understand. Initially, legacy hub compatibility was the goal.
Control Protocols
Control protocols are essential for managing network control protocols that frequently deliver untagged frames, such Cisco Discovery Protocol (CDP), VLAN Trunking Protocol (VTP), and Spanning Tree Protocol (STP). The proper handling of these frames is guaranteed by the Native VLAN.
Maintaining Connectivity
The idea behind the Native VLAN is to make sure that, in the event that the trunk malfunctions or encounters problems, some network traffic can continue to pass over the full switched network. It assists in preventing packet loss that could result from configuration errors by giving untagged traffic a destination.
Important Features
- It don’t use access ports; they only use trunk ports.
- All other VLANs on a trunk port are carried with 802.1Q tags, but Native VLAN traffic is untagged.
- There can only be one Native VLAN per trunk, and for the trunk link to function properly, this VLAN must match on both ends.
- IEEE 802.1Q trunking is unique to the Native VLAN concept. For instance, untagged frames are not supported by Cisco’s proprietary Inter-Switch Link (ISL) trunking protocol since it automatically tags frames from every VLAN.
Also Read About Cisco Basic Switch Configuration Commands step by step guide
Default Native VLAN
Most switches, especially Cisco switches, have VLAN 1 set up as the Native VLAN by default. Additionally, VLAN 1 is usually the management VLAN by default.
Advantages of Native VLAN
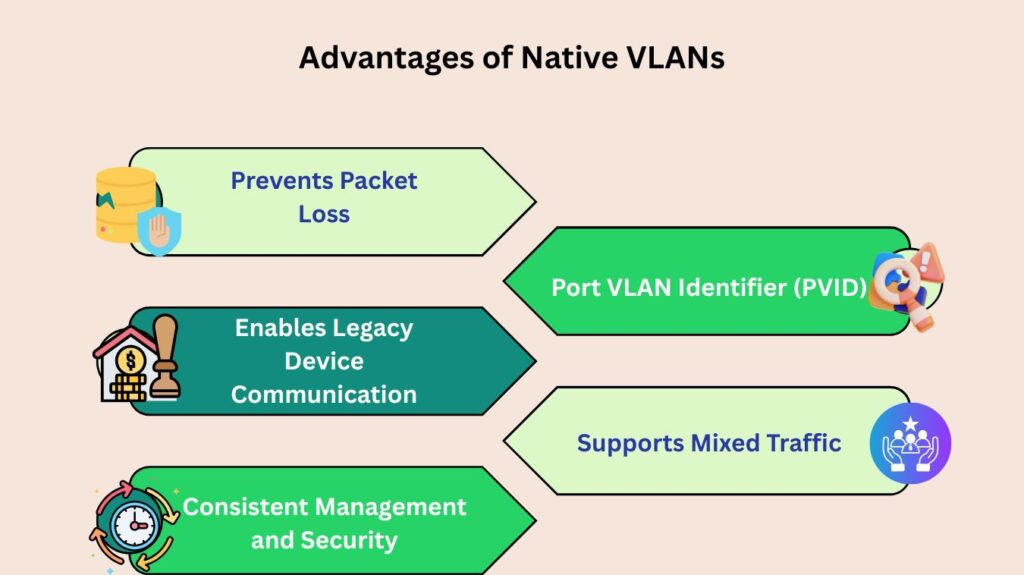
Prevents Packet Loss: It makes sure that untagged traffic is not dropped by allocating it to a particular VLAN.
Enables Legacy Device Communication: Traffic can still be sent over the network using the Native VLAN by devices that do not support VLAN tagging.
Consistent Management and Security: By designating a “home” for untagged packets, it offers a consistent method of managing and safeguarding network traffic.
Port VLAN Identifier (PVID): Each physical port is given a Port VLAN identification (PVID), which acts as an untagged frame identification. Every untagged frame that is received on a port has a PVID associated with it.
Supports Mixed Traffic: It allows both tagged traffic from other VLANs and untagged traffic for the Native VLAN to pass across the trunk link.
Also Read About What Is VLAN Trunking? How It Works, Advantages & Protocols
Security Concerns and Best Practices
The possibility of VLAN hopping attacks is a significant security risk associated with it. A frame double-tagged with a target VLAN could be sent by an attacker, which would result in the frame being routed to an unexpected VLAN.
The following are some best practices to reduce these risks:
Changing the Native VLAN: Setting the Native VLAN from VLAN 1 to an unused dummy VLAN ID (such as VLAN 99 or VLAN 666) is highly advised. No user-facing traffic should be sent over this unused VLAN. By doing this, security is improved and vulnerabilities related to the default VLAN 1 configuration are avoided.
VLAN 1 Should Not Be Used for User Traffic: VLAN 1 should not be used for any user traffic.
Consistent Configuration: For a trunk link to function properly, it needs to be set up exactly the same on both ends.
Tagging Native VLAN Traffic: Using globally or per-trunk force trunk ports to tag Native VLAN traffic is an additional mitigation strategy.
Configuration Example (CLI)
To set up a switch interface (such as Gig1/0/1) with a Native VLAN (such as VLAN 999):
switch(config)#vlan 999switch(config)#int Gig1/0/1switch(config-if)#switchport trunk encapsulation dot1qswitch(config-if)#switchport mode trunkswitch(config-if)#switchport trunk native vlan 999
Troubleshooting and Mismatches
- A Native VLAN mismatch occurs when the Native VLAN configurations on either side of a trunk link are different.
- The Cisco Discovery Protocol (CDP) will display warning messages on the console or in system logs if there is a discrepancy.
- In order to stop the impacted port from forwarding traffic, the Spanning Tree Protocol (STP) will put it in a Port VLAN ID (PVID) inconsistent state.
- A mismatch won’t usually harm user data, which is usually tagged, but it could cause traffic in the Native VLAN to hop to another VLAN, which could result in unexpected network behaviour or security flaws.
Also Read About Cisco Basic Switch Configuration Commands step by step guide
Verification Commands
The following commands can be used to examine the Native VLAN and additional trunking parameters:
show interfaces trunkshow interfaces switchport
