What is UDP flood attack?
A denial-of-service attack (DOS) known as a UDP flood occurs when malevolent actors create User Datagram Protocol (UDP) packets to a targeted server by impersonating a source IP address. The server responds with a “destination unreachable” packet if it is unable to locate an application linked to the UDP packets.
How it Works
In a UDP flood attack, the threat actor usually uses a tool to send a large number of UDP packets to a server on the target subnet, frequently from a spoofed host (i.e., a host with a faked source IP address). In order to identify closed ports, the attacking program typically searches through all of the server’s known ports. The server is compelled to respond with an ICMP port unreachable message for each UDP packet sent to a closed port.
This method produces a significant amount of ICMP replies because a server frequently has a large number of closed ports. A large amount of the available network bandwidth is used by this “lot of traffic on the segment”. The target system is overloaded by the constant barrage of UDP packets and the ICMP answers that follow, which causes sluggish transmission and response times or possibly crashes the device or service. A UDP flood assault’s outcome is strikingly similar to that of a typical DoS attack.
Because UDP is an unreliable and connectionless protocol, it is used for this kind of attack. UDP does not create a virtual circuit or need acknowledgements to deliver data, in contrast to TCP. This makes it effective for flooding since it enables an attacker to deliver a constant stream of packets without having to control session states.
Why it is Important
One of the cornerstones of information security (Confidentiality, Integrity, and Availability) is the availability of network services, which is directly threatened by UDP flood assaults, making comprehension and defence against them essential.
- Service Disruption: By interfering with network services, they can prevent authorised users from accessing devices or apps.
- Resource Exhaustion: The target server’s network bandwidth, CPU, and memory resources are heavily used by the constant traffic creation and ICMP replies, which can lead to crashes or performance degradation.
- Business Impact: These interruptions can have a significant negative influence on business operations by causing expensive network outages, lost productivity, and destruction or theft of important data and assets.
Also Read About Advantages And Disadvantages Of SNMP, How SNMP Work
Techniques
Attackers use a variety of methods to carry out UDP floods:
Direct Flood Attack
The easiest method is to send a lot of UDP packets to various ports on a targeted server. The packets usually include a spoof source IP address to hide the attacker’s identity. When the server receives a packet, it searches for an application that is listening on the specified port. If it detects none, it replies with an ICMP “Destination Unreachable” packet. The massive volume of ICMP responses and incoming UDP packets drains the server’s bandwidth and resources.
Amplification/Reflection Attacks
This kind of UDP flood is more potent and sophisticated. By using a third-party server, it amplifies the attack’s impact. The attacker sends a brief UDP packet containing the victim’s spoof source IP address to a vulnerable public server (such a DNS or NTP server). The public server then responds with a much larger response from the victim’s fake IP address. In effect, this amplifies the assault’s volume. Because an attacker’s single request can result in a response that is 50–100 times larger than the original packet, it is an extremely effective way to overload a target.
Fragmentation Attacks
This technique involves sending large UDP packets that are fragmented, or broken up, into smaller pieces before they arrive at their destination. The victim’s machine must then attempt to reassemble these damaged packets using its available resources. When packets are fragmented or unreassembled, the process uses a lot of CPU and memory, which can lead to a denial-of-service attack.
Advantages
A UDP flood assault has various benefits for a threat actor:
- Simplicity: The DoS attack is comparatively easy to execute.
- Efficiency for Disruption: Because UDP is connectionless, the attacker can send a large number of packets with no overhead on their end because they don’t have to keep track of a state for every connection.
- Bandwidth Exhaustion: The attack successfully uses up a sizable portion of the target network’s bandwidth, depriving genuine traffic of service.
- Anonymity: The attacker can conceal their genuine identity by using spoof source IP addresses, which makes it more difficult to determine where the attack originated.
Disadvantages
UDP flood attacks pose the following hazards to network defenders:
- Service Unavailability: Important network services and applications are inaccessible to authorised users.
- Resource Depletion: Critical network resources such as memory, CPU, and bandwidth are depleted by the attack.
- Severe network congestion may result from the large amount of traffic produced, particularly from ICMP replies.
- Difficulties in Detection: Although DoS assaults are usually detectable, it might be difficult to differentiate malicious floods from genuine high traffic without sophisticated analysis.
- Inherent UDP Characteristics: The “fire-and-forget” characteristic of UDP makes it even more problematic because it has any inherent flow control or reliability to organically limit the flood.
Also Read About CISCO IFS IOS File System Advantages And Disadvantages
UDP flood attack Uses
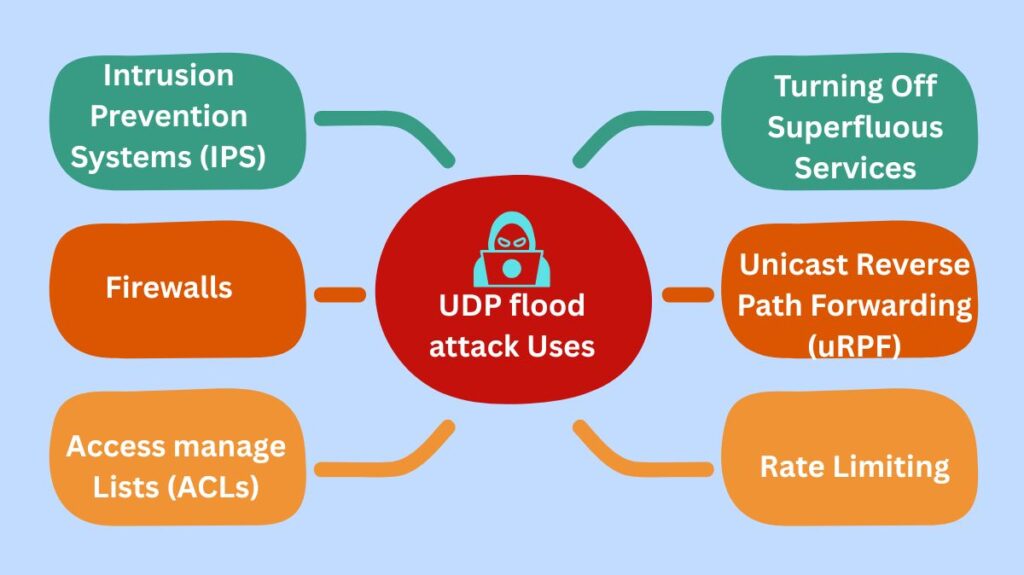
UDP flood attacks can be lessened by implementing a number of security measures:
Intrusion Prevention Systems (IPS)
Positioned in the network path, these devices actively filter packets according to anomalous traffic patterns or known exploit signatures. They are able to identify malicious UDP flood traffic and either block or reroute it. Contextual data can be used by NGIPS to keep an eye out for zero-day attacks.
Firewalls
Stateful firewalls are essential because they can monitor connection status and spot unusually large UDP traffic volumes coming from certain sources. They can be set up to use UDP port numbers to filter packets. Stateful inspection may be more difficult for UDP, though, because it lacks the “tightly controlled state information” that TCP does.
Access manage Lists (ACLs)
Set up on routers, ACLs can restrict some UDP traffic, including that from fake source IP addresses, filter undesired UDP packets, and manage traffic flow in order to apply security regulations.
Turning Off Superfluous Services
A lot of outdated or underutilised UDP small services (including Echo, Discard, and Chargen) are frequently turned on by default on network devices and can be used by attackers to cause denial of service attacks. Potential attack vectors are decreased by turning off these superfluous services.
Unicast Reverse Path Forwarding (uRPF)
By determining whether arriving packets have a source address that would typically exit the same interface and rejecting those that don’t, this capability can be enabled on interfaces to prevent attacks employing spoof IP packets.
Rate Limiting
During an assault, a server might avoid being overloaded by its own responses by imposing rate restrictions on particular kinds of traffic, such as ICMP replies. Rate limitations are also supported by DAI and DHCP snooping to guard against DoS attacks on the switch CPU.
Also Read About Network Device Management Software: Centralized Control
