DNS Spoofing Attack
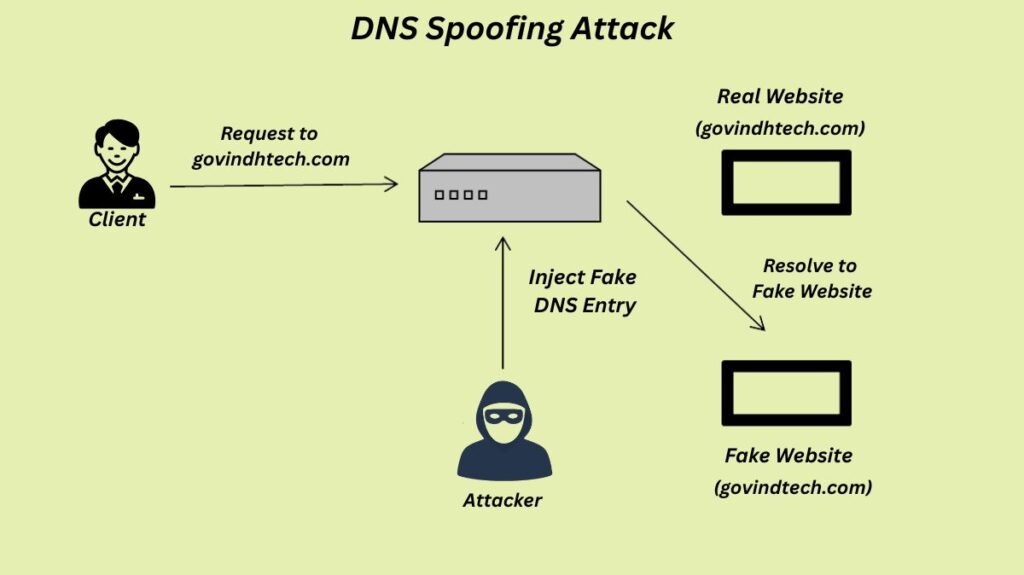
In order to cause human-readable domain names to resolve to the incorrect IP address, a cyberattack known as DNS Spoofing, or DNS Cache Poisoning, corrupts the Domain Name System (DNS). The ultimate effect is that users are taken to a server controlled by the attacker, which frequently hosts a phoney website that appears authentic, rather than the actual website they were hoping to access.
Mainly, DNS spoofing is used to spread malware, viruses, or phoney software updates, or to steal private information, including financial information and login passwords (phishing).
You can also read What is an Amplification Attack, How It Works and Prevention
How DNS Spoofing Works
The DNS protocol was originally created for a smaller internet environment and lacks robust security validation, which is why the attack takes advantage of its basic characteristics.
Normal DNS Process: When a user types a website name (e.g., www.bank.com), their device sends a request to a DNS resolver to find the corresponding numerical IP address. The DNS system converts the human-readable name into the IP address necessary for data routing.
Caching: The time to live (TTL) specifies how long the DNS resolver temporarily holds (“caches”) previously obtained translations in order to improve performance and expedite the operation.
Exploiting the Cache (Poisoning): The attacker makes use of DNS system flaws to introduce erroneous DNS information into the cache of the DNS resolver. In order to make it look as though the response originated from the genuine authoritative name server, the attacker sends a forged DNS response to the resolver. The malicious IP address of the attacker is mapped to the real domain name in this falsified response.
Redirection: Once the DNS resolver accepts and caches this malicious mapping, it becomes “poisoned” because the DNS protocol fails to properly verify the legitimacy of the answer. The attacker will use their fictitious IP address to direct any subsequent users that query that poisoned resolver for the legitimate domain to the counterfeit website.
It is challenging to execute DNS spoofing attacks since the attacker frequently has a few milliseconds to transmit the phoney response before the real authoritative server reacts. Successful attacks frequently depend on guessing elements such as the request ID number, the resolver port, and the authoritative nameserver that the query will be sent to.
Consequences and Risks
If DNS spoofing is successful, there could be serious dangers:
- Data and Financial Theft: Data and financial theft occurs when users are taken to phishing websites that mimic legitimate websites and enter private information without realizing it, such as passwords, login credentials, credit card numbers, or other private information.
- Malware Distribution: Sometimes through drive-by downloads, the malicious website can infect the user’s machine with malware, including ransomware, Trojan horses, botnets, computer worms, and viruses.
- Security Disruption: By impersonating websites belonging to internet security providers, attackers might render a user’s computer vulnerable by preventing it from receiving the required security updates.
- Widespread Impact: Many people may be impacted at once if a main DNS resolver or ISP server contains malware.
- Censorship: Governments may alter the DNS to restrict access to particular websites, but DNS manipulation can also be used for censorship.
Prevention and Mitigation Strategies
Both users and administrators can implement measures to protect against DNS spoofing:
For Users
- Use a VPN: To avoid MITM-style DNS tampering on local networks, use a Virtual Private Network (VPN), which encrypts your whole connection, including your DNS requests.
- Check for HTTPS and the Padlock: Always ensure the website URL begins with
https://and displays a padlock icon 🔒, especially before logging in. If the attacker fails to obtain a valid SSL/TLS certificate for their fake site, the browser will usually display a security warning.
- Clear DNS Cache: You can eliminate locally poisoned items by routinely cleaning the local DNS cache on your device.
For Server Administrators (Most Effective)
- Implement DNSSEC: By adding cryptographic digital signatures to DNS data, Domain Name System Security Extensions (DNSSEC) enable DNSSEC. By doing so, DNS resolvers can prevent the majority of cache poisoning attempts by confirming that the response they receive is genuine and unaltered.
- Use Encryption for DNS: By using protocols such as DNS over HTTPS (DoH) or DNS over TLS (DoT), DNS queries are encrypted, making it impossible for local network attackers to intercept and fake them.
- Update Software: To remove known vulnerabilities that hackers could exploit, patch and upgrade DNS server software on a regular basis.
You can also read What Is Wi-Fi Eavesdropping, The Threat Of Network Snooping?
