This article covered core concepts, the AAA Process, access control, and the access control process in a computer network. What are the different types of access control in network security? implementation methods, importance, and challenges.
Access control
A security method or approach known as access control limits who or what is allowed to view or use resources in a computer network or computing environment. It is regarded as a foundational idea in security that reduces the risk to an enterprise or group.
Enforcing policies that confirm users are who they say they are and guarantee they are given the right access levels is the main purpose of access control. It establishes who is eligible for what resources and under what circumstances.
Access Control process in a computer network
Also Read About What is IP Spoofing Attack and How IP Spoofing Works
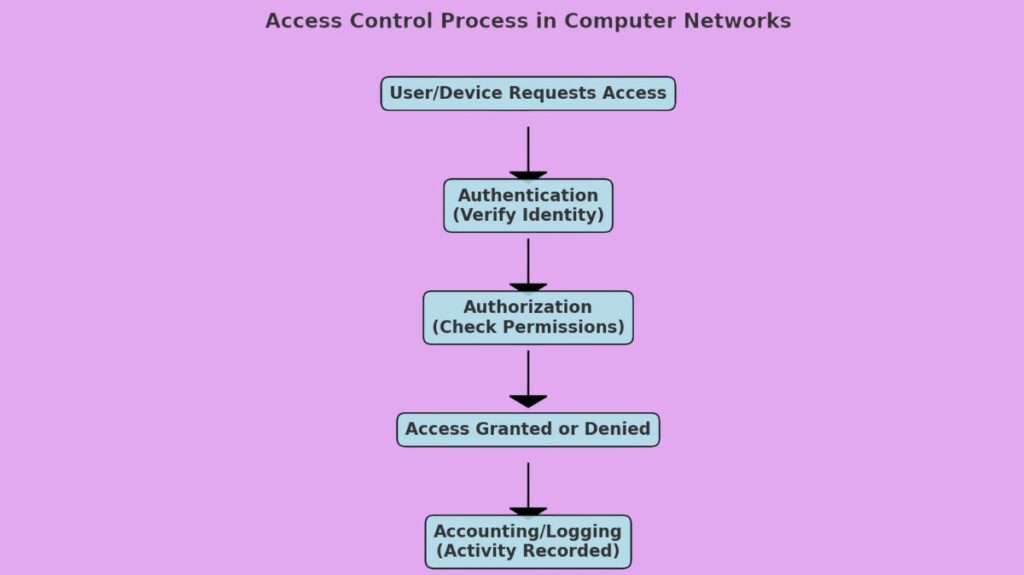
The initial stage in granting a person or device access to a network resource is authentication, in which the system confirms the requester’s identity (e.g., by the use of a digital certificate, password, or biometric method). Following identity verification, the system proceeds to authorisation, where it determines if the verified user is authorised to access the resource in question. This check determines whether access is allowed or refused. The last stage, accounting or logging, is when the system logs the specifics of the access attempt for security analysis, auditing, and monitoring, regardless of the result.
Examples
- A corporate firewall that restricts access to the internal database to IP addresses belonging to employees.
- WPA2/WPA3-protected Wi-Fi that only authorised users with the correct password can access.
- Before using cloud resources, multi-factor authentication (MFA) is required.
Core Concepts and the AAA Process
The principle of least privilege (POLP), which is frequently the foundation of access control, guarantees that users and devices are only given the minimal access privileges required to carry out their mandated tasks. The three-part AAA structure is frequently used to explain the process of implementing access control:
Identification
The first phase is identification, in which a subject (user, system, or device) asserts their identity, usually by supplying a username.
Authentication
The process of confirming the stated identification is known as authentication. Authentication establishes whether the individual is who they say they are. This step assesses the necessary login information, which could be physical cards or keys, biometric scans (such as fingerprint or retinal scans), PINs, or passwords. By requiring two or more authentication elements, multi-factor authentication (MFA) improves security.
Authorisation
Following successful authentication, this phase takes place. By defining the precise services, rights, and resources that the authenticated user is permitted to use or access, authorisation establishes the scope of access.
Access
The confirmed identity is given access to the requested resource following the successful completion of authentication and authorisation.
Accounting (Auditing)
In order to establish a compliance audit trail and spot any access infractions, this component entails monitoring and documenting user behaviour, such as commands issued or connection duration.
Also Read About What Is Network Based Firewall, How It Works And Types
What are the different types of access control in network security?
There are two primary categories into which access control can be generally divided:
Physical Access Control: Campuses, buildings, rooms, data centres, and tangible IT assets are examples of physical locations and assets that are restricted by physical access control. High-security systems like a Mantrap and keycard or badge scanners are two examples.
Logical Access Control: Limiting access to computer networks, system files, data, processes, applications, and systems is known as logical access control. Examples include using a Virtual Private Network (VPN) to remotely access an employer’s network or entering a password to log into a laptop.
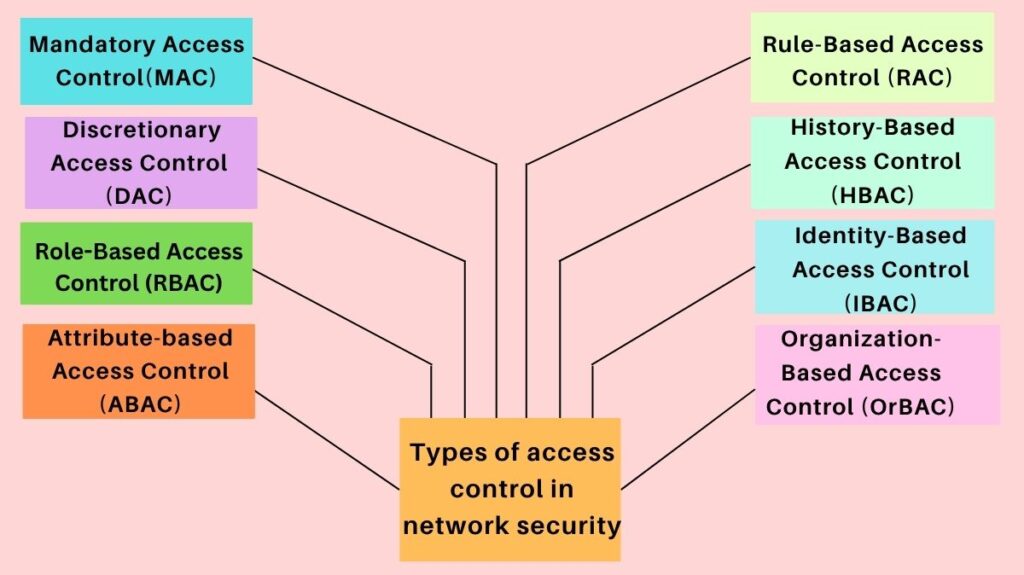
To establish and implement logical access policies, organisations use a variety of models:
| Access Control Model | Description | Example Use |
|---|---|---|
| Mandatory Access Control (MAC) | Access rights are strictly regulated by a central authority based on assigned security labels (classifications) for both the user and the resource. Users cannot set or change permissions. | High-security environments like military or government systems. |
| Discretionary Access Control (DAC) | The owner of the resource or data sets the policies and determines who can access the resource and can grant or revoke that access at their discretion. | File permissions (Read, Write, Execute) in operating systems like Windows or Linux. |
| Role-Based Access Control (RBAC) | Access is granted based on the role (e.g., “Manager,” “HR Specialist”) or defined business function the user holds within the organization; permissions are assigned to the role, not the individual. | An HR role having access to employee records but not server configurations. |
| Attribute-based Access Control (ABAC) | Access is determined dynamically by evaluating a set of rules and relationships using attributes related to the user, the resource, and environmental conditions (like time of day, location, or department). | Allowing access to specific financial files only if the user is from the Finance department and working during office hours. |
| Rule-Based Access Control (RAC) | Access is governed by specific rules defined by the system administrator, often based on contextual conditions like location or time. | Only allowing students to use labs during a certain time of day. |
| History-Based Access Control (HBAC) | Access is granted or declined by evaluating the history of activities of the inquiring party, including behavior, time between requests, and content of requests. | Denying a request if the request interval exceeds one query per second, based on past behavior. |
| Identity-Based Access Control (IBAC) | Network administrators manage activity and access based on individual requirements (unique user identities). | Granting specific, tailored access rights to a single unique user based on their personal needs. |
| Organization-Based Access Control (OrBAC) | This model allows the policy designer to define a security policy independently of the implementation (i.e., abstract roles and activities). | Defining access policies based on abstract organizational concepts before mapping them to specific users and resources. |
Network Access Control (NAC)
Network Access Control (NAC) is a specific use of access control.
All devices trying to connect to a network are subject to security policies enforced by NAC. Before giving the device complete network access, it checks its security posture (such as whether the antivirus software is up to date and whether the necessary updates are installed).
Usually, NAC operates in two phases:
- A gadget is examined for conformity prior to admittance. Devices that don’t comply are put in a quarantine network to be fixed.
- After granting access, the device’s usage is continuously tracked, and access may be limited in accordance with security regulations and the user’s job.
Implementation Methods
In computer networks, access control systems can be implemented utilizing a variety of technologies and techniques:
Virtual Private Networks (VPNs)
When employees are geographically dispersed, companies frequently employ virtual private networks, or VPNs, to enable safe, remote access to network resources.
Access Control Lists (ACLs)
Lists of instructions known as access control lists (ACLs) are applied to the interfaces of network devices, such as routers and firewalls, to filter undesirable packets and enforce security regulations by allowing or prohibiting traffic according to predetermined criteria. By filtering according to protocol, port number, and source/destination IP addresses, extended ACLs offer more precise control.
Network Access Control (NAC)
Devices trying to join to a network are subject to security regulations enforced by Network Access Control (NAC). Before allowing complete network access, NAC checks a device’s security posture (e.g., requiring the most recent antivirus software or necessary upgrades).
802.1X
A port-based authentication and access control protocol called 802.1X is used to prevent unwanted access to LAN devices such as switches and wireless access points.
Centralized Management Systems
Group-based access control can be used with security tools such as the Identity Services Engine (ISE), which defines policies using Scalable Group Tags (SGTs) to regulate user group communication.
Also Read About What A Network Is And What Are Benefits Of Networking
Importance
In order to assist organisations adhere to different data privacy requirements, access control is essential. These consist of:
PCI DSS
The payment card ecosystem is safeguarded by the Payment Card Industry Data Security Standard (PCI DSS). Ensuring user identity and allowing or prohibiting transactions depend on an access control system.
HIPAA
The purpose of the Health Insurance Portability and Accountability Act (HIPAA) is to prevent the disclosure of patient health information without the agreement of the patient. Limiting access to authorised users, making sure that no one may access data that is outside of their privilege level, and averting data breaches all depend on access control.
SOC 2
An auditing process called Service Organisation Control 2 (SOC 2) was created for service providers who keep client data on cloud servers. It compels businesses to establish and adhere to stringent policies and processes around consumer data and guarantees that providers preserve the privacy of their clients. In order to enforce these stringent data security procedures, access control systems are essential.
ISO 27001
Organisations in all sectors must adhere to security standards established by the International Organisation for Standardisation (ISO) to show their clients that they take security seriously.The ISO’s gold standard for certification of information security and compliance is ISO 27001. To adhere to this security standard, access controls must be put in place.
Challenges
Nevertheless, access control methods have difficulties, especially in contemporary IT environments:
- Distributed IT Systems: It can be challenging to manage access across geographically dispersed systems that integrate cloud services with real-world hardware, virtual machines, and systems.
- Policy Management: To maintain the system current, coordination between the IT department, which turns policies into code, and policymakers, who draft policies, is necessary.
- Monitoring and Reporting: To guarantee adherence to legal requirements and company policies, organisations must continuously assess their access control systems.
- User Experience: Employees may misuse or avoid access management technology if it is hard to use, which could lead to security and compliance flaws.
Also Read About What is an Amplification Attack, How It Works and Prevention
