What is Unicast Reverse Path Forwarding
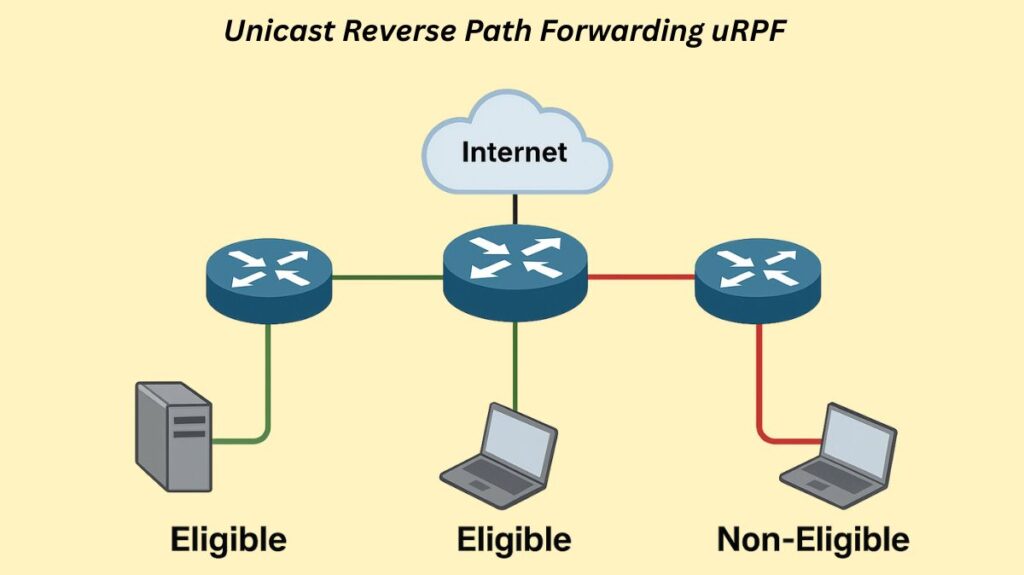
Network routers with Unicast Reverse Path Forwarding (uRPF) help guard against IP address spoofing and lessen the effects of Distributed Denial of Service (DDoS) and Denial of Service (DoS) attacks. It operates by comparing an incoming packet’s source IP address to the router’s routing table or Forwarding Information Base (FIB).
How Unicast RPF Works
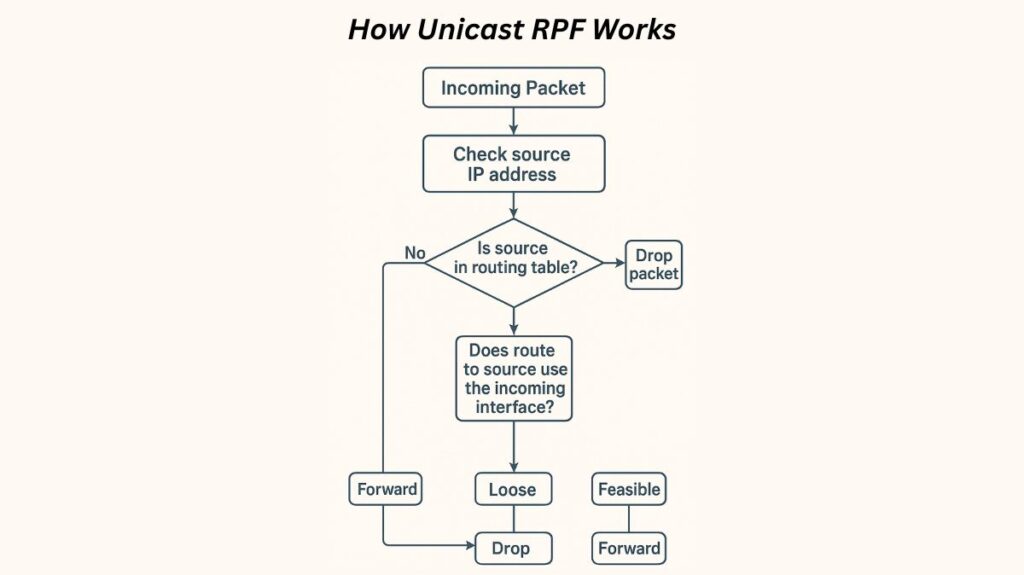
By using a reverse path lookup, uRPF adds a check on the packet’s source IP address in contrast to regular packet forwarding, which simply checks the destination IP address.
The following validation procedure takes place when a router with uRPF enabled receives a packet on an interface:
- Reverse Path Lookup: To find the anticipated outgoing interface it would use to carry traffic back to the packet’s originating IP address, the router consults its routing table (FIB).
- Validation Check: The router contrasts the actual incoming interface where the packet arrived with the intended outgoing interface, or the “best path” back.
- Action:
- If the check passes, the packet is considered legitimate and is forwarded.
- If the check fails (e.g., the packet arrived on an unexpected interface, or the source address is completely unreachable), the packet is considered spoofed and is dropped.
A packet from a certain source can only enter the network via an interface that is logically on the path back to that source this method. For the uRPF check to work on Cisco routers, Cisco Express Forwarding (CEF) must be enabled.
You can also read What is Dynamic ARP Inspection, How it Works & Configuration
uRPF Operating Modes
Unicast RPF can be configured in various modes, with Strict Mode and Loose Mode being the most common:
| Feature | Strict Mode (rx / active-path) | Loose Mode (any / feasible-paths) |
|---|---|---|
| Checks Performed | Two checks: 1. Is the source IP in the routing table? 2. Is the receiving interface the best reverse path to the source IP? | One check: 1. Does the source IP have any route in the routing table? (The receiving interface does not matter) |
| Path Requirement | Requires that the incoming interface matches the router’s best known outgoing interface for that source. | Only requires a route to exist, regardless of the interface. |
| Use Case | Best for networks with symmetrical routing and single-homed customer-facing interfaces, offering strong spoofing protection. | Used in multi-homed or asymmetric routing environments, such as the ISP core or peering points, where legitimate traffic may arrive on alternate paths. |
| Asymmetric Routing | May drop legitimate traffic if the return path is different from the arrival path. | Tolerates asymmetric routing. |
A less popular option that provides a compromise between Strict and Loose modes and permits a certain amount of asymmetric routing is the viable-Path option, which determines whether the incoming interface matches any of the viable (alternative) routes to the source address contained in the FIB.
Deployment Considerations
To secure the network, uRPF should be implemented at the network’s edge (on interfaces that are visible to customers). On the other hand, because network core (internal) interfaces are very likely to encounter routing asymmetry, it is strongly advised against enabling uRPF on these interfaces.
In order for uRPF to operate efficiently on the ISP-to-ISP edge, where forwarding characteristics (many ISP peers, varied pathways) render Strict Mode impractical due to the best path selection restrictions of routing protocols, Loose Mode had to be developed.
Handling Failed Checks and Default Routes
If a packet fails the uRPF check, it is counted and, by default, is silently discarded.
- Fail Filters: If a packet fails the uRPF check, you can apply custom actions like accepting, rejecting, reporting, or sampling by configuring an optional fail filter.
- BOOTP and DHCP Packets: Bootstrap Protocol (BOOTP) and Dynamic Host Configuration Protocol (DHCP) packets (source 0.0.0.0, destination 255.255.255.255) are not automatically accepted when uRPF is enabled; instead, they require the application of a fail filter to be specifically accepted.
- Discarding via Null Route: Packets whose source address points to a discard interface (such as Null0) can be discarded using loose mode. This capability is used to quickly drop traffic from known attack sources over the network edge through techniques like Remote Triggered Null Route filtering, which is frequently triggered by BGP updates.
The presence of a default route (0.0.0.0/0) can change how uRPF behaves, particularly if the default route uses an interface configured with uRPF.
- If a default route uses the interface on the majority of routers, Loose mode automatically accepts all packets.
- All packets are accepted in loose mode on some systems (routers with MPCs and the MX80), with the exception of those whose source is determined by the default route, which are rejected.
- If the source address matches any route (default or learnt) that can be reached through the interface, the packet is allowed in Strict mode.
You can also read What is an Amplification Attack, How It Works and Prevention
