VPN tunnels
A safe, encrypted virtual pathway or communication channel created between two or more devices over an untrusted public network, like the Internet, is known as a VPN tunnel. It is a fundamental idea in Virtual Private Networks (VPNs).
A VPN tunnel’s main function is to safely transfer private information over a public network architecture. Data is shielded from manipulation or eavesdropping by employing a tunnel. Unauthorised access to sent data is prevented by the secure channel.
How VPN Tunneling Works?
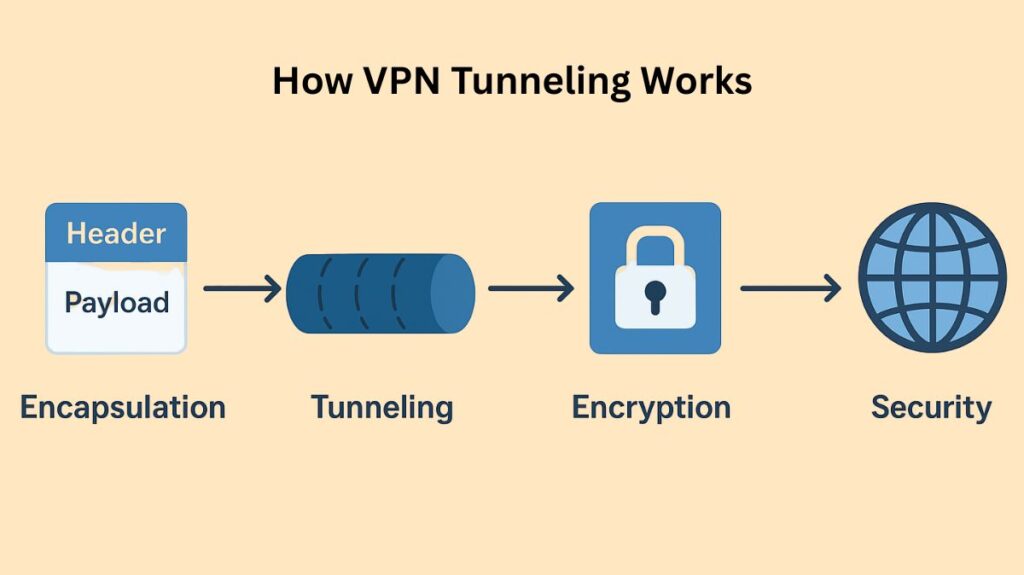
Encapsulation and encryption are two essential procedures for the setup and functioning of a VPN connection.
- Encapsulation and Tunnelling
The process of inserting an integrated data packet with routing information into another packet is known as tunnelling. Another name for this procedure is encapsulation.
- Mechanism: A packet is wrapped inside another packet to accomplish encapsulation. The original packet becomes the payload itself since its header and contents are placed into the surrounding packet’s payload section.
- Routing: The tunnel is the path that the packets take. Transparent data transmission from the source network to the destination network is made possible by tunnelling.
- Protocol Flexibility: By encapsulating the unsupported packet inside the supported one, encapsulation enables data that utilizes one network protocol (such as IPv6) to go over a network that only supports another protocol (such as IPv4).
Also Read About Components of DHCP Dynamic Host Configuration Protocol
- Encryption and Security
A VPN tunnel uses encryption and other security measures to keep the enterprise’s packet private while it travels over the unprotected Internet, whereas the term “tunnel” generally solely refers to encapsulation.
- Procedure: Two devices (close to the Internet’s edge) establish a VPN tunnel in order to provide security. They add extra headers required for secure traffic and encrypt the original IP packet, rendering its contents unintelligible (cypher text).
- Data Flow: Prior to leaving the device, the data is encrypted. After receiving the encrypted data, the VPN server decrypts it using keys before sending it to the network that is supposed to receive it. The encrypted tunnel is also traversed by data on its way back to the user.
- Benefits of the secure VPN tunnel include anti-replay protection, data integrity (confirming the packet was not altered), secrecy (privacy), and authentication (confirming the sender).
Three Main Steps of Tunnel Creation
These three steps are involved in setting up a VPN tunnel:
- Authentication: The user’s device’s VPN client software connects to a distant VPN server (gateway). To confirm they are authorised parties, the client and server authenticate one another via credentials, shared secrets, or digital certificates.
- Encryption and Key Exchange: During a cryptographic handshake, the client and server discuss and decide on the session keys (such as Diffie-Hellman) and encryption techniques that will be used to encrypt the data.
- Tunneling/Encapsulation: The Encapsulating Protocol is a new header that encapsulates the encrypted Passenger Protocol, the original data packet. The Carrier Protocol is used to send the whole secured packet over the Internet.
Also Read About How Does Address Resolution Protocol Work And ARP Table
Types of VPN Tunnels
VPN tunnels can be classified according to their deployment model or operational control.
Based on Operational Control
Two tunnelling methods that are related to connection management are supported by VPNs:
Voluntary Tunnelling: All connection setup is managed by the VPN client. After the client establishes a connection with the ISP, the VPN client application uses this active connection to construct the tunnel on the VPN server. There are two steps in this process.
Compulsory Tunnelling: All connection setup necessary for the VPN is managed by the carrier network provider. The client connects to the carrier normally in this one-step method, and the carrier serves as a middleman to connect to the VPN server. Compulsory tunnelling allows the ISP full administrative control over the tunnels while concealing the VPN server’s connectivity information from the customers. This approach for client verification uses broker devices, often known as the Network Access Server (NAS) or VPN Front End Processor (FEP).
Based on Deployment (Tunnel Usage)
VPN tunnels are used to implement two major types of Virtual Private Networks (VPNs) connections:
| VPN Type | Connection Characteristic | Tunnel Functionality | Typical Protocol |
|---|---|---|---|
| Site-to-Site VPN | Connects two entire private networks (e.g., branch office to headquarters). Tunnels are typically configured by network engineers and left operating permanently. | Network-to-Network | IPsec |
| Remote Access VPN | Connects individual hosts (telecommuters, mobile users) to a company network. The user’s device creates the secure connection, which is usually on-demand. | Host-to-Network (Client-to-Site) | TLS/SSL, OpenVPN, WireGuard |
Also Read About APIDS Application Protocol-Based Intrusion Detection System
Common VPN Tunneling Protocols
Tunneling protocols define the rules for establishing, maintaining, and securing the connection.
| Protocol | Description | Characteristics and Use |
|---|---|---|
| IPsec (Internet Protocol Security) | An industry standard that operates at the Network Layer (Layer 3). | Adds security features, including encryption and integrity checks. It is traditionally used for Site-to-Site VPNs. Often paired with IKEv2. |
| OpenVPN | An open-source protocol known for its flexibility and strong encryption (using AES 256-bit). | Highly secure and versatile, using either TCP (reliable/slower) or UDP (faster) transport. |
| WireGuard | A modern, lightweight VPN protocol praised for its high performance and security (using state-of-the-art encryption). | Known for being extremely fast and suitable for mobile devices. |
| L2TP/IPsec (Layer 2 Tunneling Protocol) | L2TP creates the tunnel, but IPsec is required for encryption and security. | Widely compatible, offering moderate security and speed. The dual layers of security can potentially slow down transmission speed. |
| SSTP (Secure Socket Tunneling Protocol) | Utilizes SSL/TLS encryption, often over TCP port 443. | Known for robust encryption and its ability to bypass firewalls because it does not depend on fixed ports. Primarily used on Windows systems. |
| PPTP (Point-to-Point Tunneling Protocol) | One of the oldest protocols. | Facilitates easy setup, but its encryption is not as strong as newer protocols, leading to significant, well-known security vulnerabilities; largely considered obsolete. |
| GRE (Generic Routing Encapsulation) | A tunneling protocol that creates virtual point-to-point links. | Can encapsulate many protocols but is non-secure by default and does not inherently offer encryption; it must be used with IPsec to be secured. |
It’s also crucial to remember that a VPN’s split tunnelling capability lets users separate their network traffic. While some traffic bypasses the VPN and accesses the internet directly, some traffic is routed through the secure, encrypted VPN tunnel. Although speed and bandwidth can be increased, the untunneled traffic is left unprotected.
Also Read About Protocol Based Intrusion Detection System PBIDS Advantages
