What is EAP SIM?
Utilizing the security features of the Subscriber Identity Module (SIM) card used in mobile phones, the EAP-SIM (Extensible Authentication Protocol–Subscriber Identity Module) Protocol is an authentication method that allows users to authenticate to wireless networks, including Wi-Fi hotspots.
EAP-SIM is an EAP technique that enables mutual authentication between a GSM subscriber and the authenticator (usually a RADIUS server). It was first developed by the 3GPP and is detailed in RFC 4186.
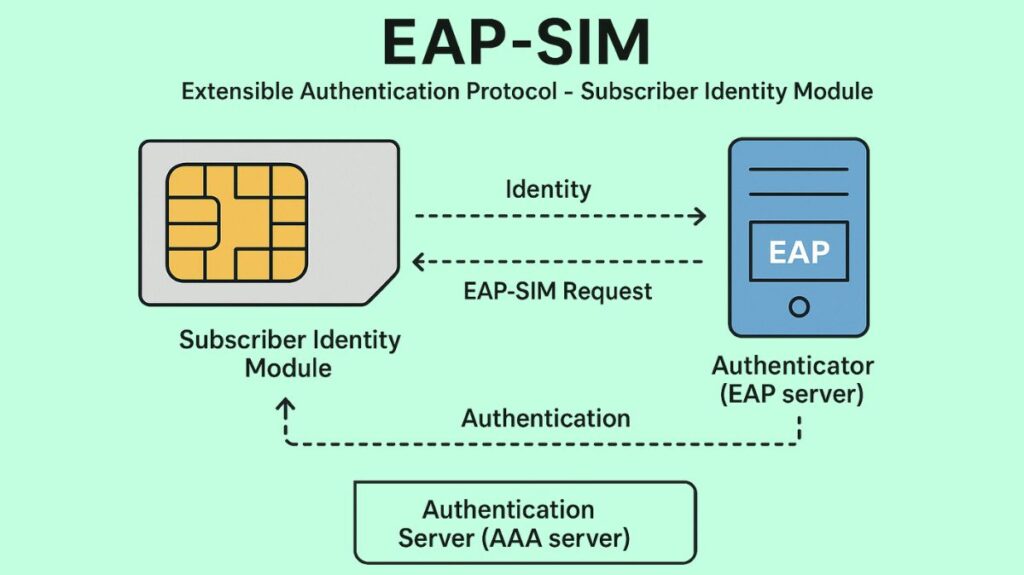
Components
The Global System for Mobile Communications (GSM) authentication and key agreement (AKA) method serves as the foundation for EAP-SIM. A challenge-response protocol is its foundation.
Key Components and Credentials:
- SIM Card: This device holds the user’s secret key, Ki, as well as the encryption and authentication protocols.
- Secret Key (Ki): Only the GSM operator’s Authentication Centre (AuC) (or HLR/HSS/AUSF in contemporary core networks) is aware of the shared secret key, Ki, which is kept on the SIM card.
- IMSI: A globally unique string of digits saved on the SIM, the International Mobile Subscriber Identity (IMSI) is used by the GSM subscriber to identify themselves.
- AAA/RADIUS Server: This authentication server verifies credentials by processing EAP exchanges and gaining access to the mobile core database (HLR/AuC).
You can also read What is EAP FAST, How it Works and Advantages of EAP-FAST
How EAP-SIM Works?
The Global System for Mobile Communications (GSM) authentication and key agreement (AKA) method serves as the foundation for EAP-SIM. The authentication server (RADIUS) and the client (a mobile device with a SIM) communicate via a challenge-response protocol.
Here’s a simplified breakdown:
- Identity Request: The client’s identification is requested by the access point. The customer gives either a temporary identity (pseudonym) or their International Mobile Subscriber Identity (IMSI).
- Challenge Generation (RADIUS): A series of arbitrary challenges is created for the SIM card by the RADIUS server, which has access to the mobile operator’s Home Location Register/Authentication Centre, or HLR/AuC.
- Challenge Forwarding: The client device receives the challenges through the access point.
- SIM Card Computation: These problems are sent to the client device’s SIM card. The SIM card calculates a response to each challenge using a secret key (Ki) that is only known to the HLR/AuC.
- Response Transmission: The client device receives the responses from the SIM card and sends them to the RADIUS server.
- Verification (RADIUS): The RADIUS server does the same calculation as the SIM card since it has the secret key (Ki) for that subscriber. The client is authenticated if the responses from the client match the responses calculated by the server.
- Key Generation & Access: A distinct session key is generated, and the client is given network access upon successful authentication.
With this secure communication between the SIM card and the Authentication Centre, the EAP-SIM architecture eliminates the need for a pre-established password between the client and the AAA server.
Usage
With key derivation based on GSM methods, EAP-SIM is defined as an authentication technique for 2G/3G mobile network standards.
Requirements for Deployment:
The following infrastructure is needed in order to implement EAP-SIM:
- A client (like wpa_supplicant) that can access the (U)SIM.
- A WLAN access point that supports EAP (e.g., WPA(2)-ENTERPRISE).
- The WLAN AP/Controller can access a RADIUS server that manages session key generation and authentication.
- In a production setting, the Home Location Register (HLR) of the Mobile Network Operator (MNO), where the SIMs are registered, must be accessible to the RADIUS server.
You can also read What is EAP-TTLS, Characteristics, Advantages and Use cases
Advantages of EAP-SIM
- Seamless Roaming: Makes it simple for users to move between Wi-Fi and cellular networks by enabling smooth and automatic authentication to Wi-Fi networks using their current cellular subscriptions.
- Strong Security: Makes use of the GSM/UMTS AKA’s strong security features, which are intended to safeguard mobile communications. The SIM card always contains the secret key (Ki).
- User-Friendly: Users don’t have to keep track of many Wi-Fi passwords. Their SIM card serves as the basis for the automatic authentication.
- No Certificates Required: Removes the requirement for complicated PKI maintenance or client-side digital certificates.
- Built-in Billing/Policy: Easily incorporated with the billing and service policies of mobile operators.
Disadvantages of EAP-SIM
- Tied to Mobile Carriers: Needs interaction with the authentication infrastructure (HLR/AuC) of mobile operators, which can be difficult for a non-telecom organization to set up.
- SIM Card Dependency: A physical SIM card (or its equivalent, eSIM) with a current subscription is required for the client device.
- Performance: Because of the back-and-forth communication and SIM card calculations, the challenge-response process may occasionally be a little slower than other EAP techniques.
- Less Common in Pure Enterprise Wi-Fi: Although it works well in telecom settings, traditional enterprise Wi-Fi networks are less likely to use it unless they are made especially for mobile operators or their customers.
Comparison with Related Protocols
EAP-SIM is distinct from, but related to, newer authentication methods:
- EAP-AKA: EAP-AKA is based on the Authentication and Key Agreement (AKA) method found in third-generation mobile networks, such as CDMA2000 and the Universal Mobile Telecommunications System (UMTS). Compared to EAP-SIM’s shoddy encryption and scant identity protection, EAP-AKA offers more sophisticated security measures.
- EAP-AKA’ and 5G-AKA: Even more recent protocols, EAP-AKA and 5G-AKA, are made for 4G and 5G networks and provide better key management and user equipment identity protection. Nowadays, legacy deployments are the main use for EAP-SIM.
Similar to using a key card to enter a restricted area, EAP-SIM integrates the Wi-Fi network with the cellular operator’s core authentication system. The key (the SIM) is validated against the master database (the AuC) to prove identity and automatically grant access without requiring a unique, temporary password for each entry point.
You can also read What is PEAP Protected Extensible Authentication Protocol?
