EAP AKA
EAP-AKA is an EAP technique that uses the Universal Subscriber Identity Module (USIM) card present in 3G, 4G, and 5G mobile phones to enable a client (usually a mobile device) to authenticate to a network. It is made for the Universal Mobile Telecommunications System (UMTS) and other cutting-edge mobile networks, and it is the replacement for EAP-SIM.
Similar to EAP-SIM, EAP AKA allows users to seamlessly and securely authenticate to non-3GPP access networks (such as Wi-Fi hotspots) using their current cellular subscription credentials saved on their USIM.
You can also read What is EAP-TLS Meaning, How EAP TLS Works & Advantages
Fundamentals and Context
- Basis in 3G Networks: EAP-AKA describes an EAP technique based on the Authentication and Key Agreement (AKA) mechanism used in third-generation (3G) mobile networks, including CDMA2000 and the Universal Mobile Telecommunications System (UMTS).
- Successor to EAP-SIM: EAP-AKA is the replacement for EAP-SIM, which was created for Global System for Mobile Communications (GSM) networks of the second generation (2G).
- SIM Dependency: EAP-AKA is dependent on the security information kept on the Universal Subscriber Identity Module (USIM) card, which is commonly present in mobile phones that are 3G, 4G, and 5G. The USIM is a program that UMTS carriers deliver on gadgets like smart cards.
- Infrastructure Use: By utilizing the third-generation mobile network authentication infrastructure, it enables devices (clients) to authenticate to non-3GPP access networks, including Wireless LANs (WLANs) or Wi-Fi hotspots, using their current cellular subscription credentials.
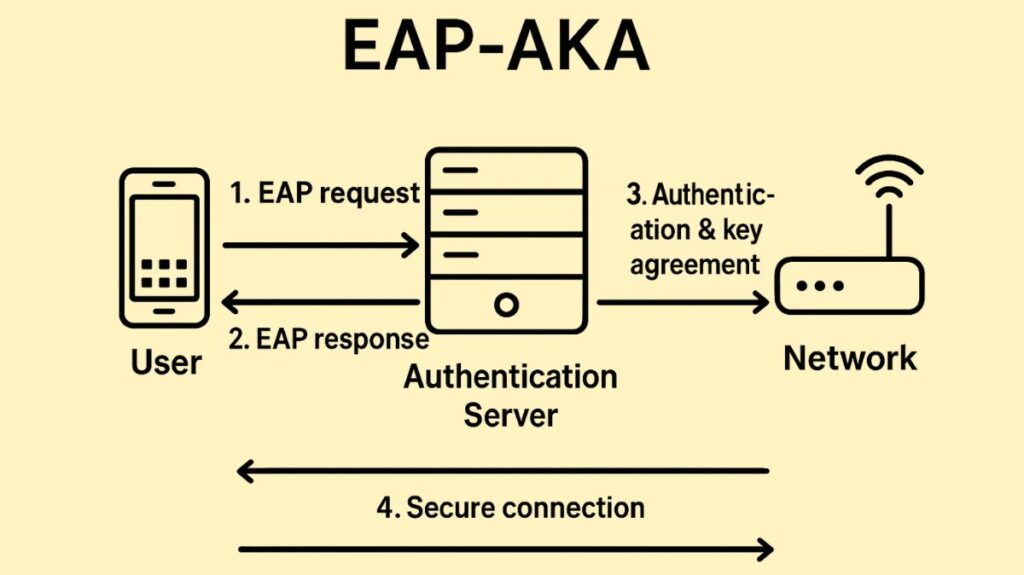
How EAP-AKA Works
EAP AKA uses a challenge-response protocol and key derivation between the client and the authentication server. It is based on the more reliable 3GPP AKA technique. There are multiple steps in this process:
- Identity Request: The client usually responds with its International Mobile Subscriber Identity (IMSI) or a temporary identity (pseudonym) when the access point (authenticator) asks for the client’s identity.
- Authentication Vector Request: To obtain a set of authentication vectors for the subscriber, the Authentication, Authorization, and Accounting (AAA) server, typically RADIUS, interacts with the mobile operator’s core network, which may include the Home Location Register/Authentication Centre (HLR/AuC) or Home Subscriber Server (HSS).
- Authentication Vector Components: Each vector contains four key components:
- RAND (Random Challenge): The mobile device is given a random number.
- AUTN (Authentication Token): Used by the USIM to verify the network.
- XRES (Expected Response): The response the server expects to receive from the USIM.
- CK (Cipher Key) & IK (Integrity Key): Keys derived for secure communication.
- Challenge Transmission: The client device receives the AUTN and RAND from the RADIUS server.
- USIM Computation: The client forwards the RAND and AUTN to its USIM card. The USIM performs critical functions:
- Network Authentication: It allows mutual authentication by confirming the AUTN to make sure the network is authentic.
- Response Generation: It calculates a RES (Response) using RAND and its secret key (K). (The SRES parameter in GSM and the RES parameter in 3G AKA are equivalent.)
- Key Derivation: RAND and its secret key (K) are used to derive session-specific CK and IK.
- Verification and Access: The RADIUS server receives the computed RES from the client. If the server’s stored XRES and the returned RES match, authentication is successful, and the client is given access. The master session key is obtained by the server using the CK and IK.
You can also read EAP and How Does Extensible Authentication Protocol Work?
Advantages of EAP AKA
EAP-AKA offers several significant advantages for modern network convergence:
- Strong Mutual Authentication: To prevent rogue access points, it offers robust mutual authentication, in which the network authenticates the client and the client (via the USIM) authenticates the network (using AUTN).
- Seamless Mobility/Roaming: With the help of their current cell subscriptions, users can have safe, automatic access to Wi-Fi networks, facilitating smooth roaming.
- Enhanced Security: Strong key generation and cryptographic algorithms, as well as robust encryption and communication integrity protection, are among the additional security features that come with being based on the 3GPP AKA.
- Simplified Deployment: It makes deployment easier for users by doing away with the requirement for client-side digital certificates.
Common Use Cases
EAP AKA is the preferred method for:
- 3G/4G/5G Offloading to Wi-Fi: Enabling mobile operators to seamlessly transfer subscriber data traffic from their cellular networks to Wi-Fi networks.
- Carrier Wi-Fi: Providing secure, automatic access to operator-branded Wi-Fi hotspots for mobile subscribers.
- Fixed-Mobile Convergence: Key for services that integrate cellular and Wi-Fi access for a unified user experience.
- Devices with USIMs: Smartphones, tablets, and other devices with USIM/eSIMs.
Disadvantages of EAP-AKA
- Complexity: Deployment by non-telecom entities is complicated by the need for substantial interaction with the core network architecture of mobile operators (HLR/AuC or HSS).
- USIM Card Dependency: Dependency on a valid USIM card (or eSIM equivalent) with an active subscription is required for the client device.
- Performance: The multi-step challenge-response method may add some latency, similar to EAP-SIM.
- Specific to Mobile Ecosystem: In situations involving mobile network operators and their subscribers, it is most advantageous.
Evolution in 5G
EAP-AKA has changed to accommodate more recent technologies:
- EAP-AKA’: This is the EAP-AKA version that supports 5G. It explains the EAP using the most recent iteration of the 3GPP, often known as the 5G method, which is standardized by the IETF as RFC 9048.
- EAP-AKA-PFS: The IETF is currently standardizing this variation, which is intended to complement EAP-AKA with forward secrecy in accordance with zero-trust principles.
EAP AKA works similarly to a security fingerprint scanner at a border crossing: when you show your identity card (USIM), the network verifies the scanner itself (network authentication via AUTN) in addition to determining whether your face matches the picture (client authentication). Before extremely secure keys are generated to open the gate and encrypt all ensuing traffic, this strong, mutual verification makes sure that the user and the access network are authentic.
You can also read What is MSCHAPv2, How it Works & MSCHAPv2 Key Features
