Let us discuss about Simple Network Management Protocol, How it work, applications, Advantages And Disadvantages Of SNMP.
Simple Network Management Protocol

An application-layer protocol called SNMP allows network devices to communicate management information. The Transmission Control Protocol/Internet Protocol (TCP/IP) family includes SNMP, one of the most popular network protocols for controlling and keeping an eye on network components in a range of sectors.
History
The publication of RFC 1065, “Structure and Identification of Management Information for TCP/IP-based Internets,” in 1988 marked the beginning of SNMP. A standardized database of IP-based network device variables (such as configuration settings, status data, and counters) and a straightforward mechanism for tracking and controlling them were the main concepts.
You can also read What Is Routing Loop Prevention? Guide To Network Stability
How does SNMP Work
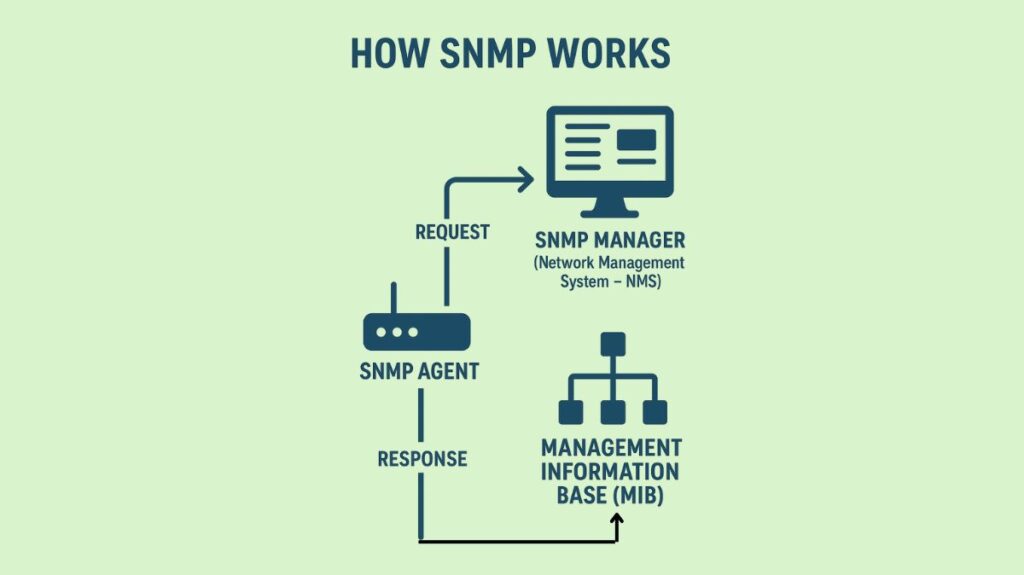
A Management Information Base (MIB), SNMP agents (managed nodes), and an SNMP manager are the three primary components of an SNMP system.
SNMP Manager (Network Management System – NMS): Often known as a Network administration Station (NMS), this is a network administration program that runs on a computer or server. Network administrators are notified, traps are gathered, data is analysed, and devices are polled for information.
SNMP Agent: Software that gathers and saves information about the configuration, status, and counters of each managed device such as a server, router, or switch is what this is.
Management Information Base (MIB): Variables (objects) on each SNMP agent are stored in this hierarchical database. What can be retrieved or set on a managed device is specified by the MIB. A tree structure’s distinct Object IDs (OIDs), which can be either words or numbers, are used to identify variables in the MIB.
You can also read Cisco Discovery Protocol, How CDP Works, And Benefits of CDP
SNMP Messages
GET messages (Get, GetNext, GetBulk): The NMS uses this to poll a device and get particular data from the agent’s MIB. For the effective retrieval of massive volumes of data, SNMPv2c introduces GETBULK.
SET messages: By which the NMS writes data to MIB variables in order to modify a device parameter or initiate an action on a managed device.
TRAP messages: Unsolicited notifications that an SNMP agent sends to the NMS in response to a threshold or important event (such as a high CPU utilization or an interface going down). Traps do not have application layer error recovery; instead, they employ a “fire-and-forget” procedure over UDP.
INFORM messages: Comparable to traps, but with SNMPv2’s increased dependability. The agent will send the Inform message again unless the NMS acknowledges receipt. Informs are more reliable than traps, but they have a little higher overhead.
SNMP Types
There are various SNMP versions, with the main distinction being in the security features they offer:
SNMPv1: The first version, as specified in RFC 1157. Only UDP is used, and plaintext authentication with community strings is supported. The MIB is accessed by community strings, which are essentially clear-text passwords.
SNMPv2c: Similar to SNMPv1, an addition to SNMPv2 provided support for SNMP communities. Performance gains, particularly with GETBULK, and more thorough error messages through INFORM messages are two benefits it offers. SNMPv2c is mainly UDP-based, however it can be set up to utilise TCP, and it still employs plaintext community strings.
SNMPv3: The standard version, which offers notable improvements in security. What it offers is:
- Message integrity: Verifies that correspondence hasn’t been altered while in route.
- Authentication: Verifies a message’s provenance by using hashed passwords and usernames, which are never sent in plain form.
- Encryption (privacy): Encrypts the contents of messages to stop hackers from reading and intercepting them. SNMPv3 is compatible with both TCP and UDP.
You can also read What Is A QoS Quality of Service CISCO Benefits And Types
Advantages of SNMP
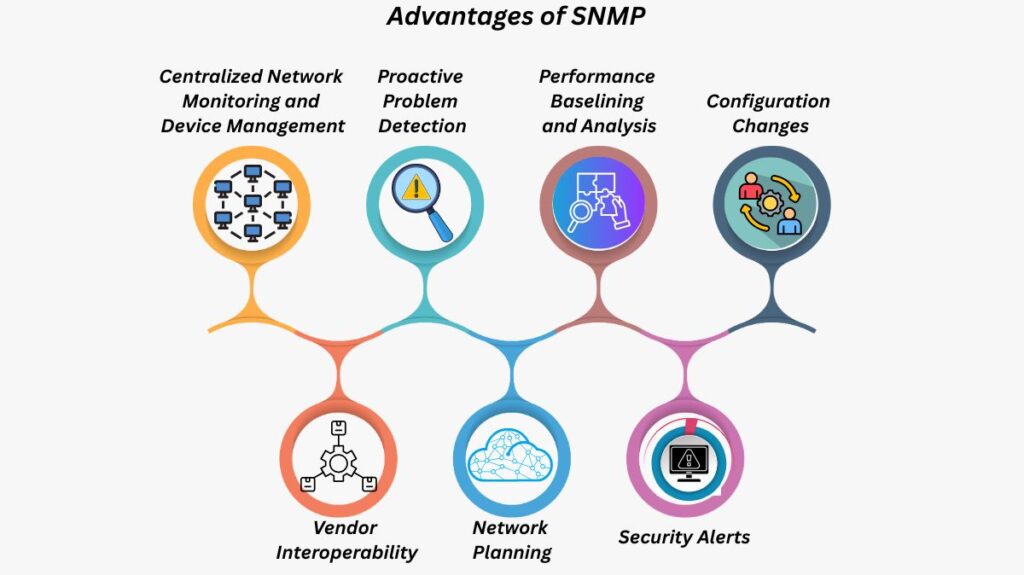
For network operations, SNMP is an essential tool because of its many advantages:
Centralized Network Monitoring and Device Management: It gives NMSs the ability to track devices, identify problems, and collect performance data.
Proactive Problem Detection: Agents can deliver traps or notifications when thresholds are exceeded (e.g., high CPU utilisation, interface failures), which administrators can set.
Performance Baselining and Analysis: NMS has the ability to sample values (such as CPU utilization) on a regular basis in order to assess trends, find deviations, and set baselines.
Configuration Changes: Device reconfiguration is possible for administrators using SNMP Set messages.
Vendor Interoperability: SNMP is extensively supported by equipment from various vendors as an Internet standard protocol.
Network Planning: Decisions on network architecture and expansion plans are aided by the performance statistics gathered.
Security Alerts: Port security violations and other security events can be detected by SNMP traps.
Disadvantages of SNMP
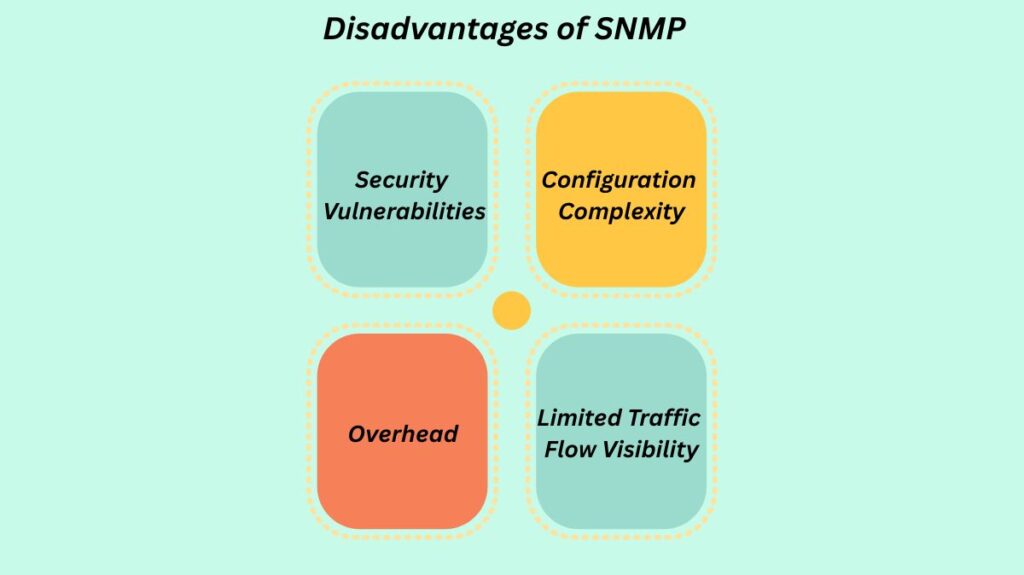
Security Vulnerabilities (SNMPv1/v2c): SNMPv1 and SNMPv2c’s main drawback is that they employ clear-text community strings, or passwords, which are susceptible to sniffing attacks. They are therefore a major security risk and an easy-to-spoof protocol.
Configuration Complexity (SNMPv3): SNMPv3 contains a lot more configuration choices and might be difficult to set up, even if it is more secure.
Overhead (Informs): The overhead of inform messages is slightly higher than that of fire-and-forget traps because they require NMS acknowledgement.
Limited Traffic Flow Visibility: Cisco IOS NetFlow and other tools are able to distinguish between distinct traffic flows, such as source/destination IP, ports, protocols, etc., while SNMP mainly reports on device statistics, such as CPU, RAM, and interface problems.
You can also read CISCO LLDP Link Layer Discovery Protocol Advantages, Types
Applications of SNMP
Numerous facets of network administration make extensive use of SNMP, including:
Monitoring Network Device Health: Monitoring the CPU, memory, interface status (up/down), interface packet counts, throughput, consumed bandwidth, and CRC faults.
Configuration Management: SNMP Set messages can be used to configure certain settings or modify device properties.
Troubleshooting: Supplying vital information for diagnosing network issues by detecting deviations or comparing current measurements to a baseline.
Security Operations: Notifications of incidents such port security infractions.
Network Planning: Collecting data in order to plan future network expansion, use-based billing, and network traffic accounting.
Integration with NMS: To query, gather, store, and display network data, Network Management Systems (NMS) such as Cisco Prime, SolarWinds, and HP Openview rely extensively on SNMP.
Configuration
The SNMP agent is activated when a snmp-server global command is configured for the first time, however it is normally disabled by default in Cisco IOS.
SNMPv1 and SNMPv2c Configuration SNMPv1 and SNMPv2c use community strings, which function as clear-text passwords, for authentication. Due to their shared use of communities, SNMPv2c and SNMPv1 configurations are fairly similar.
You can also read Network Device Monitoring: Control Plane & Protocol Insights
SNMPv2c Configuration (Get and Set Support)
On a Cisco router or switch, set up SNMPv2c using the global configuration commands shown below:
snmp-server community string {RO|RW} [acl-name]: This necessary command determines the access level as either read-only (RO) or read-write (RW) and sets the community string (password). To limit access, you can optionally specify an IPv4 or IPv6 ACL.
- Read-only (RO): Ggives the NMS the ability to read MIB variables without altering them.
- Read-write (RW): Enables writing and reading (Gets and Sets).
snmp-server location text-describing-location: Recording the device’s actual position is optional.
snmp-server contact contact-name: (Optional) Recorded the device’s contact person.
ip access-list standard ACL_NAME: To limit SNMP access to authorized NMS hosts, create an ACL (optional).
SNMPv2c Configuration (Trap and Inform Support)
In order to set up an SNMPv2c agent to provide an NMS unsolicited alerts (Traps or Informs):
snmp-server host {hostname | ip-address} [informs] version 2c notification-community: Configures the SNMP agent to send either Traps (default) or Informs to the specified NMS host, using a notification-community string. Use this command once for each NMS host.
snmp-server enable traps [type-of-trap]: Enables the sending of all supported types of Trap and Inform messages.
SNMPv3 Configuration
SNMPv3 replaces community strings with users and groups to configure its security features.
snmp-server group name v3 {noauth | auth | priv} [read viewname] [write viewname] [access acl-name]: Defines a user group and its security level (noauth, auth, priv), and can optionally define MIB views and an ACL.
- noauth: No authentication, no privacy.
- auth: Authentication (MD5 or SHA) but no encryption.
- priv: Authentication and encryption (DES, 3DES, or AES).
- MIB Views:
v1defaultis a predefined MIB view that includes most of the MIB. Thewrite v1defaultparameter allows Set operations.
snmp-server user username group-name v3 [auth {md5 | sha} auth-password] [priv {des | 3des | aes {128 | 192 | 256}} priv-password]: In order to configure an SNMPv3 user, you must include their username, encryption key and method (DES, 3DES, or AES), authentication password and algorithm (MD5 or SHA), and SNMP group reference.
You can also read Network Device Maintenance Applications And How It Works
Verification
Use the display commands listed below to confirm the SNMP setup and functionality:
show snmp: Shows information about the global SNMP status and counter, such as the quantity of SNMP packets sent and received, illegal operations, bad versions, unidentified community names, requested variables, changed variables, and trap PDUs. This command does not repeat setup settings; instead, it concentrates on status and counter information.
show snmp community: Shows the community strings that have been specified, together with their access levels (RO/RW) and any related ACLs.
show snmp location: Shows the device’s configured location.
show snmp contact:The configured contact name is displayed.
show snmp host: Provides the IP address or hostname of the NMS that is set up to receive SNMP notifications (informs or traps), as well as the security model (for SNMPv3), notification type, username, and UDP port.
show snmp user: (For SNMPv3) Shows information about SNMPv3 users that have been configured, such as group name, authentication protocol, privacy protocol, Engine ID, and username.
More Details
Application Layer Protocol: The Application layer (Layer 7) of the TCP/IP architecture is where SNMP functions.
Transport Protocols and Ports: UDP ports 161 and 162 are primarily used by SNMP messages for NMS-to-agent communication and agent-to-NMS notifications, respectively. Although TCP can be enabled for SNMPv2c, SNMPv1 and SNMPv2c mostly use UDP, and SNMPv3 uses both TCP and UDP.
Community Strings: Community strings are used in SNMPv1 and SNMPv2c as straightforward plaintext passwords. An NMS can read MIB variables using read-only (RO) community strings, but it cannot alter them. In contrast, read-write (RW) community strings enable both reading and writing.
SNMPv3 Security Levels: SNMPv3 defines security levels: noAuthNoPriv (no authentication, no privacy), authNoPriv (authentication with hashing like MD5 or SHA, but no encryption), and authPriv (authentication and encryption using DES or DES-256).
MIB Views: The idea of MIB views is supported by SNMPv3, which define a subset of the MIB to restrict access to particular sections for particular managers.
Securing SNMP: Limiting SNMP communications to known NMS hosts only via ACLs is advised to improve security. It is best to use SNMPv3 because of its encryption and authentication features. Until secure versions are set up, it is acceptable to disable SNMPv1/v2c or SNMP completely.
Remote Monitoring (RMON): A more comprehensive picture of the network rather than simply individual devices is made possible by RMON, an extension of SNMP that improves monitoring capabilities by introducing new data categories in the MIB. RMON continues to be a part of SNMP, and RMON cannot function without SNMP.
You can also read CISCO IFS IOS File System Advantages And Disadvantages
