In this article, we learn about Hashed Message Authentication Code, Core Components, How HMAC Works, Benefits and Applications of HMAC
A cryptographic authentication method called the Hashed Message Authentication Code (HMAC) is crucial for confirming a message’s authenticity and integrity. It is a particular kind of MAC, or message authentication code.
A secret key and a common cryptographic hash function are used to create HMAC. Because only a party with the shared secret key can correctly produce or verify the HMAC tag for a given message, HMAC ensures authenticity in contrast to simple hashing, which just checks data integrity by identifying changes.
You can also read Dynamic Host Configuration Protocol and DHCP DORA Process
Core Components and Mechanism
Two communicating parties need to have the same shared secret key and agree on the algorithm in order to use HMAC.
Components
There are two main components needed for the HMAC calculation:
- A Shared Secret Key: A shared secret key is one that only the sender (the person who sent the message) and the intended receiver or recipients must know. The key, which is used to decipher messages, needs to be kept concealed and confidential. HMAC generates and verifies keys using the same copy, or symmetric key.
- A Hash Function (Algorithm): An algorithm known as a hash function, HMAC, makes use of general cryptographic hash functions. SHA-1, MD5, SHA-256, SHA-512, and RIPEMD-128/60 are popular options. The strength of the selected hash function has a significant impact on HMAC security.
How HMAC Works
The following steps are part of the HMAC process:
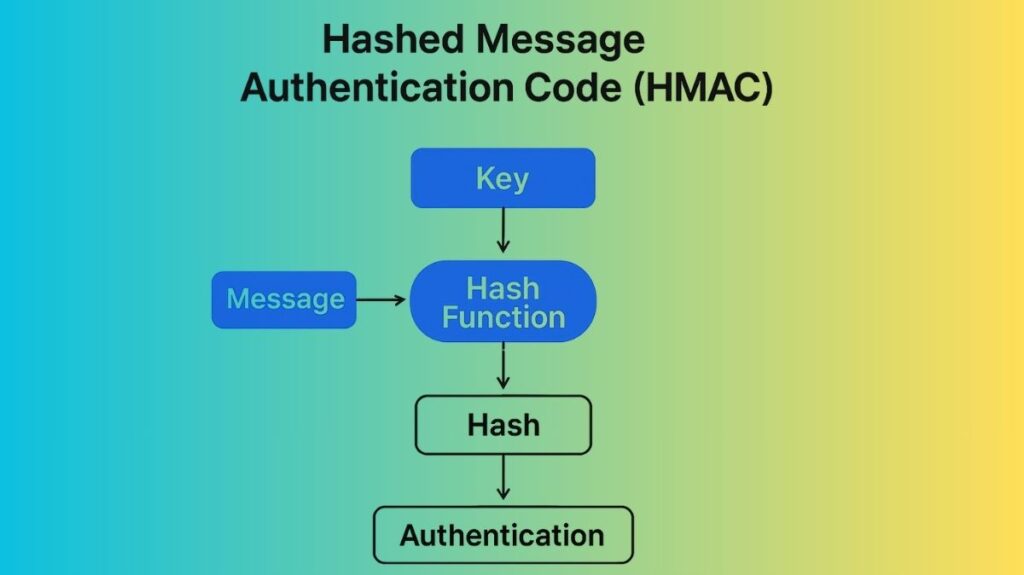
- Generation (Sender): The message and secret key are entered into the HMAC function by the sender. In two distinct passes, the function applies the cryptographic hash function several times. Two internal keys, an inner key and an outer key, are derived from the secret key. The hash function is applied first to the message combined with the inner key, and then again to that intermediate result combined with the outer key, producing the final HMAC tag.
- Transmission: The original message and the calculated HMAC tag (or hash value) are sent by the sender. The actual message might or might not be encrypted.
- Verification (Receiver): The recipient independently calculates a fresh hash value for the received message using their copy of the same secret key and the same hash method.
- Validation: The message is deemed authenticated (having come from someone who knows the secret key) and its integrity is maintained (having not been changed in transit) if the receiver’s freshly calculated HMAC tag matches the received HMAC tag. The message is rejected as tampered with or not legitimate if the hash values do not match.
The HMAC formula defines the intricate structure of the calculation, which uses XOR operations in addition to inner and outer padding (ipad and opad).
You can also read Site-to-Site VPNs Are Also Known As Router-To-Router VPNs
Benefits of HMAC
Because it is hard to forge without knowing the secret key, HMAC is a safe and dependable method. Without the key or code, the procedure makes the contents of the communication meaningless, and the final message is thought to be unchangeable and impenetrable.
The cryptographic strength of an HMAC is reliant on three factors:
- The cryptographic strength of the underlying hash function.
- The size and quality of the key.
- The size of the hash output length, in bits.
Compared to a conventional hash function, HMAC offers higher security because it includes a key. By requiring the secret key, HMAC prohibits an eavesdropping attacker from altering the data during transmission, as they would be unable to recalculate the right hash for the altered packet.
Applications of HMAC
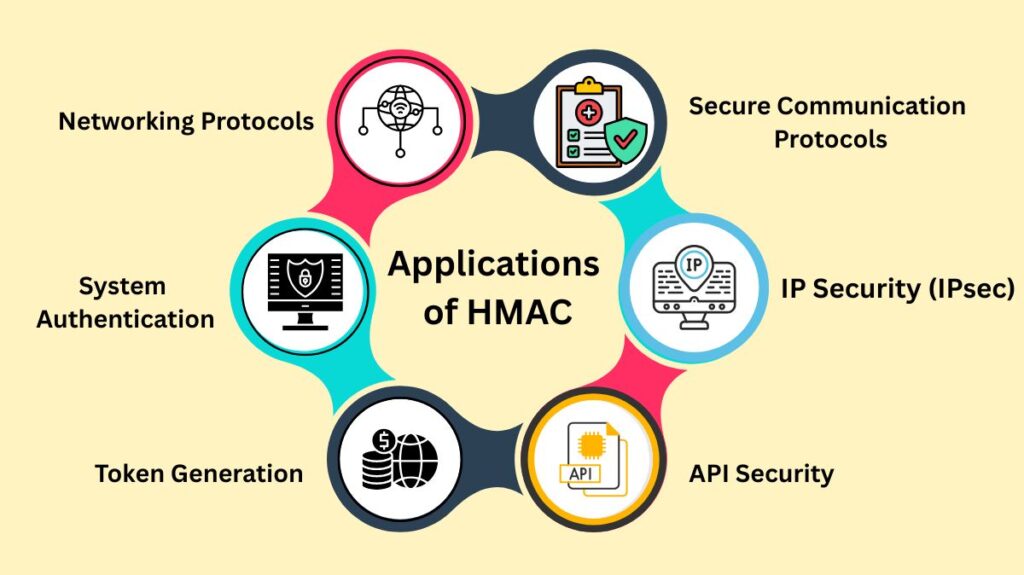
HMAC is a core component in various security implementations where data integrity and authenticity are critical:
- Secure Communication Protocols: It is widely used in protocols such as HTTPS, SSL/TLS, SSH, and SFTP.
- IP Security (IPsec): HMAC provides data integrity and is used for continuous authentication between VPN peers. Protocols like the Authentication Header (AH) rely on HMAC.
- API Security: HMAC is often used for authenticating API requests (API request signing) to ensure they originate from a legitimate source.
- Token Generation: It is used in creating secure tokens, such as JSON Web Tokens (JWTs), to verify their content and ensure they have not been tampered with.
- System Authentication: Used to generate secure hashes for storing passwords and for verifying email addresses during account activation.
- Networking Protocols: Used in SNMPv3 security levels (
authNoPrivandauthPriv) for authentication.
You can also read IP VPN Technology CISCO Secure Enterprise Connectivity
