An attacker can obtain unauthorized access, disrupt operations, or steal data by taking advantage of network security vulnerabilities, which are basic weaknesses or defects in an organization’s hardware, software, network, or security procedures.
The actual method of exploiting these vulnerabilities is known as an exploit, whereas the potential for compromise is represented by these shortcomings. A successful exploit of a vulnerability may jeopardise the fundamental security goals of Availability, Integrity, or Confidentiality (CIA).
To classify these vulnerabilities according to the element or type of defect.
Also Read About Cisco ARP Spoofing Attack Prevention And Detection Guide
Common Network Security Vulnerabilities
The following are the main categories into which the most prevalent and serious vulnerabilities often fall:
Configuration and Policy Flaws
Human mistakes, procedural flaws, or inadequate security policy implementation are frequently the causes of these vulnerabilities.
Misconfigurations: Critical components such as firewalls, routers, operating systems, or cloud services may have their security settings incorrectly set, leaving vital ports open or using default, insecure settings.
Weak or Default Passwords: Credential theft is simple when default vendor credentials are used or when they are not changed.
Inadequate Access Controls: Giving staff greater permissions than necessary violates the Principle of Least Privilege and increases the possibility of insider attacks.
Absence of MFA (multi-factor authentication): Using just one password for authentication, which facilitates account takeover in the event that the password is compromised.
Insecure Wireless Networks: Unauthorised access and communication interception are made simple by Wi-Fi networks that do not have robust encryption (like WEP) or strong passwords.
How to Prevent this Vulnerability
- Modify Default Configurations: To guarantee increased security, always modify the default settings on hardware, software, and network devices.
- Role-Based Access Control (RBAC): Use role-based access control, or RBAC, to make sure staff members can only access the data they require to do their duties.
- Frequent Logging and Monitoring: Create strong logging and monitoring procedures to quickly identify and address any anomalous activity.
- Apply the Principle of Least Privilege (PoLP): Give users only the minimal amount of access required to carry out their responsibilities.
Software and Application Flaws
These problems are caused by flaws, unsafe coding techniques, or neglected system component maintenance.
Unpatched or Outdated Software and Firmware: Using operating systems, firmware, or apps that have not received the most recent security patches exposes them to known vulnerabilities. This is known as unpatched or outdated software and firmware. If patches are not applied, viruses may infect the machine and possibly the network as a whole.
Injection Flaws: Injection flaws are vulnerabilities that let a hacker insert malicious code (such as scripts or database queries) into a reliable program or data stream, resulting in risks like Cross-Site Scripting (XSS) or SQL Injection (data theft).
Vulnerable APIs: Application Programming Interfaces (APIs) that are not adequately secured and reveal private information or permit unauthorised access to essential services are known as vulnerable APIs.
Insecure Code/Buffer Overflow: Vulnerabilities like a buffer overflow, which enables an attacker to insert malicious code, can be caused by poorly written code or errors in error handling.
Also Read About Advantages And Disadvantages Of Discretionary Access Control
Causes of Software Vulnerabilities
- Insufficient validation of input
- Unconfirmed uploads
- Cross-site scripting
- Data that isn’t encrypted, etc.
How to Prevent Software Vulnerability
- Frequent Patching and Updates: As soon as software patches and updates are made available, apply them. Antiquated software creates a lot of vulnerabilities.
- Secure Coding Techniques: To prevent typical software flaws like buffer overflows and SQL injection, developers should employ secure coding techniques.
- Use Antivirus Software: To identify and get rid of malicious code, install and update antivirus and anti-malware software on a regular basis.
- Use Appropriate Input Validation: To guard against attacks such as SQL injection and cross-site scripting (XSS), make sure that input validation checks are in place.
Human and Social Engineering Flaws
Human behavior-related security concerns, such falling for phishing scams, creating weak passwords, or being unaware of security issues, make it simpler for hackers to take advantage of the system.
Social Engineering
Social engineering is the practice of deceiving someone into disclosing private information or taking activities that jeopardise security. Typical techniques consist of:
- Phishing: Email scams that try to fool users into divulging login credentials.
- Phishing attacks conducted over the phone (Voice over IP) are known as vishing.
- Targeting well-known company executives who have access to important information is known as whaling.
Insider Threats
Threats from people with authorised access (workers, contractors) that could result in unintentional configuration mistakes, data exfiltration, or system sabotage are known as insider threats.
Physical Social Engineering
Strategies to obtain information or physical access, such Dumpster Diving (seeking clues in abandoned rubbish), Shoulder Surfing (gaining information by direct observation), or Tailgating (following an authorised user past a checkpoint).
How to Prevent Human Vulnerability
- Security Awareness Training: Provide personnel with frequent cyber security training to assist them recognise social engineering techniques, phishing scams, and other harmful activity.
- Employ Multi-Factor Authentication (MFA) and Strong Passwords: To protect user accounts, promote the use of MFA and difficult passwords.
- Frequent Security Audits: To guarantee adherence to security guidelines, conduct routine audits of employee conduct and access authorization.
- Watch Out for Questionable Emails and Links: Users should be taught not to open dubious email attachments, click on unknown links, or enter private information on unreliable websites.
Also Read About How To Prevent Watering Hole Attack, Examples And Risks
Hardware and Infrastructure Flaws
These have to do with the actual hardware, essential network elements, and underlying protocols.
IoT Device Exposure
Smart cameras, sensors, and other devices frequently have default settings or lax security measures, which hackers take advantage of to obtain initial network access or create sizable botnets for Distributed Denial of Service (DDoS) attacks.
Network protocol attacks
Exploits that target the operation of fundamental network protocols, such as TCP/IP, ARP, or DNS, are known as network protocol attacks. Among the examples are:
- Man-in-the-Middle (MITM) Attacks: An entity can eavesdrop or alter data by intercepting communication between two devices that think they are speaking directly.
- Layer 2 Vulnerabilities: Switching protocol flaws, like compromising the Spanning Tree Protocol (STP) root switch or using default Dynamic Trunking Protocol (DTP) setups to accomplish VLAN Hopping.
- CAM Table Overflow Attacks: These attacks overload the switch with MAC addresses in order to take advantage of memory constraints.
Physical Security Gaps
When servers, switches, or cables are not protected, they can be directly tampered with or stolen.
For example:
- Physical Attacks: Servers, laptops, and smartphones are examples of hardware that can be physically attacked. By stealing or altering hardware, attackers may be able to access vital systems.
- Firmware Vulnerabilities: Firmware, the software that operates on hardware, is susceptible to flaws. Because firmware flaws are not necessarily found or fixed as often as software, they might result in persistent attacks.
Also Read About What Is MAC Flooding Attack And Prevention Techniques
Hardware Vulnerability Causes
- Outdated equipment or systems
- Storage without protection
- Gadgets that aren’t secured, etc.
How to Prevent Hardware Vulnerability
- Protect Sensitive Data: To prevent unwanted access to data in the event of theft, be sure that all technology, including computers and smartphones, is encrypted.
- Employ Strong Authentication: To improve security, equip devices with biometric or multi-factor authentication.
- Safe Electronic Devices Physically: To avoid theft or physical manipulation, keep hardware equipment in safe places.
- Maintain Hardware Up-to-Date: To fix vulnerabilities and make sure the newest security measures are in place, upgrade hardware firmware on a regular basis.
Network Vulnerability
A network vulnerability is a weakness or flaw in a computer network’s architecture, setup, or operation that an attacker might use to obtain unauthorized access, steal information, or interfere with services. These weaknesses may be found in network settings, servers, protocols, or hardware (routers, switches).
- Unsecured Wireless Networks: Attackers can readily access Wi-Fi networks that are not adequately secured with encryption or strong passwords. An attacker can conduct assaults against linked systems, obtain access to devices, and intercept conversations once they are inside the network.
- Open Ports: An attacker may use an unneeded or open port on a device as a gateway. Firewalls must be configured correctly to guarantee that only the ports that are required are open and usable.
- Man-in-the-Middle (MITM) Attacks: In an MITM attack, two parties’ communications are intercepted and changed. Sensitive data, including financial information or login passwords, might be intercepted and misused if it is delivered without encryption.
Causes of Network Vulnerability
- Communication without protection
- Malicious software or malware, such as viruses, keyloggers, worms, etc.
- Attacks using social engineering
- Firewalls that are not configured correctly
How to Prevent Network Vulnerability
- Employ Strong Encryption: Make sure that SSL/TLS and other encryption techniques are used to protect sensitive data when it is being transmitted over a network.
- Secure Wi-Fi Networks: To avoid unwanted access, use WPA3 encryption and strong passwords on wireless networks.
- Intrusion Detection Systems (IDS) or Intrusion Prevention Systems (IPS) are used to monitor and safeguard network traffic, whereas firewalls are used to restrict unwanted network traffic.
- Limit Open Ports: To lessen attack surfaces, shut down any unused open ports on devices. Check the network for open ports on a regular basis.
Also Read About Types Of Access Control In Network Security: DAC, MAC & More
Exploitation Methodologies (The Threats)
Grasp how vulnerabilities turn into active threats that could endanger an organization’s assets and data requires a grasp of the concept of a network security exploit.
An exploit is a method or instrument used to breach a system or network by taking advantage of a vulnerability. If a vulnerability is there, a malevolent user must apply an exploit (similar to a pry bar in an analogy) to pose a real threat.
Network attacks that use exploits typically fall into a number of categories, such as denial-of-service (DoS) attacks, access attacks, reconnaissance attacks, and attacks against human weaknesses.
Tools attackers commonly use
- Masscan (scanning/recon) with Nmap
- The exploit framework Metasploit
- Scapy and hping3 (spoofing and packet building)
- Bettercap (LAN MitM) and Ettercap
- Tcpdump (sniffing) and Wireshark
- MAC flooding and Wi-Fi attacks(mdk3, macof)
- Botnets and malware that resembles Mirai (massive DDoS)
Typical goals of network exploits
- Theft of credentials (password/login capture)
- Interception and exfiltration of data (PII, sensitive files)
- Moving from one host to another inside a network is known as lateral migration.
- System outages caused by DoS or DDoS attacks
- Persistence: install backdoors to get access over time.
- Combining encryption or service interruption with ransomware or extortion
Detection signals & indicators
- An abrupt increase in ARP traffic or a large number of pointless ARP responses.
- A single switch port has an unusually high number of MACs.
- DNS requests to strange domains or unexpected DNS answers.
- Large number of incomplete SYN packets (SYN flood).
- SSID of a new or unidentified wireless access point broadcasting firm.
- Unexpected BGP route modifications and router/firewall configuration changes.
- Notifications from IDS/IPS (based on anomalies or signatures).
Mitigations & best practices (practical)
- Patch operating systems, apps, and network device firmware as soon as possible.
- Microsegmentation for critical systems; network segmentation/zero trust: restrict lateral movement.
- ACLs and least privilege: limit who can access what.
- Use MAC limitations and port security on switches; make use of storm control, root guard, and BPDU Guard.
- Switch ports require 802.1X authentication in addition to Network Access Control (NAC).
- Disable insecure protocols (FTP, SMBv1, WEP, SSLv3, Telnet, and FTP) and use TLS everywhere.
- Harden DNS by limiting recursive resolvers and using DNSSEC where necessary.
- Servers can reduce SYN/UDP floods by implementing rate limiting or connection limits.
- Cloud providers’ and ISPs’ mitigations of DDoS attacks and scrubbing for public services.
- SIEM for correlation, IDS/IPS, and flow monitoring (NetFlow/sFlow).
- Secure wireless: use strong passphrases, keep an eye out for rogue access points, and use WPA3/WPA2-Enterprise.
- Close unused ports and turn off unnecessary services.
- Robust credentialing procedures and MFA lower the cost of credential theft.
- Vulnerability scanning and asset inventory will help you determine what needs to be patched.
- Plan for logging and responding to incidents: have backups and playbooks.
Network Security Vulnerabilities And Exploitation
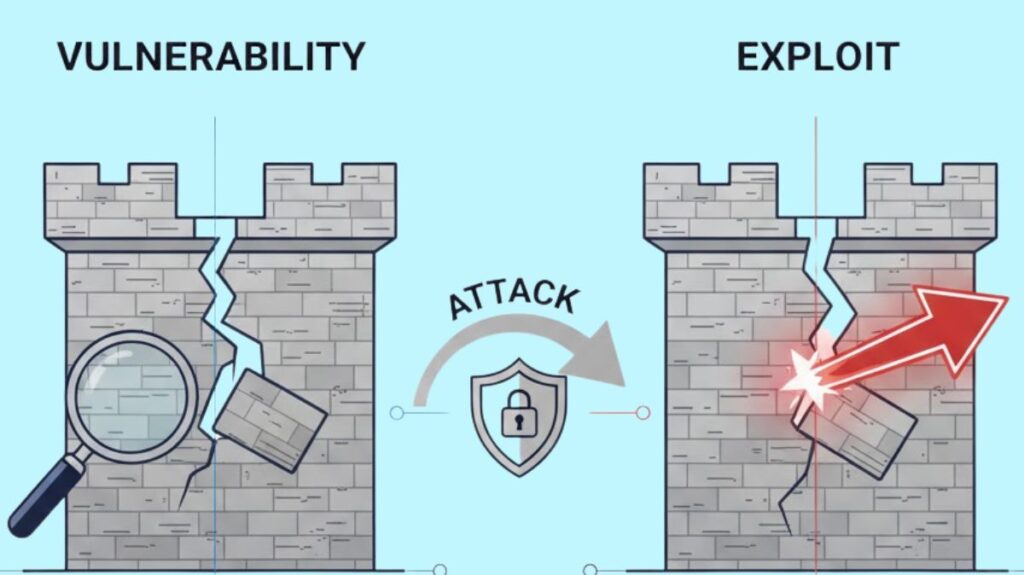
| Feature | Vulnerability | Exploit |
| What it is | A flaw, weakness, or error in a system’s design, implementation, or configuration. | A piece of software, code, or a sequence of commands that takes advantage of a vulnerability. |
| Nature | The potential for harm. (Passive) | The act of causing harm. (Active) |
| Analogy | A locked door with a flawed, easily pickable lock. | The lock-picking tool and the action of using it to open the door. |
Notable Recent and Historical Exploits (Examples)
- A serious remote code execution (RCE) flaw in the popular Apache Log4j Java logging framework is known as Log4Shell (CVE-2021-44228). Due to its widespread use, it was one of the most serious vulnerabilities found, enabling unauthenticated RCE on compromised systems.
- ProxyLogon (CVE-2021-26855): A group of flaws in Microsoft Exchange Server that gave hackers the ability to execute code remotely and get around authentication, resulting in serious scale breaches.
- A Windows Domain Controller’s Domain Administrator privileges could be obtained by an attacker to ZeroLogon (CVE-2020-1472), a critical privilege escalation vulnerability in the Microsoft Netlogon Remote Protocol.
Organisations must adopt a defense-in-depth strategy that includes frequent patching and upgrades, network segmentation, multi-factor authentication (MFA), robust firewall/IDS/IPS systems, and security awareness training for employees in order to guard against network security attacks.
Also Read About Man In The Middle MitM Phishing Attacks And How It Works?
