Dynamic Host Configuration Protocol (DHCP), Key Features and Elements, DHCP DORA Process, DHCP Address Allocation Techniques, DHCPv6 and IPv6 Addressing, Security Concerns and Mitigation, and DHCP Address Conflicts were all covered in this blog.
Dynamic Host Configuration Protocol (DHCP)
On Internet Protocol (IP) networks, the Dynamic Host Configuration Protocol (DHCP) is a crucial network management protocol. Assigning IP addresses and other crucial network setup parameters to network-connected devices (clients) automatically is its main duty.
Devices may connect without human configuration to this automation, which also makes network administration easier and lowers errors like typos and IP address conflicts.
Essential Features and Elements
The client-server architecture is the foundation of DHCP’s operation.
Configuration Parameters
A DHCP server automatically supplies a number of parameters required for network communication on a device:
- IP address.
- Subnet Mask.
- Gateway (router address) by default.
- addresses of DNS servers.
- Lease (the duration of validity of the IP address assignment).
Additional configuration choices, including domain names, time servers (NTP), or boot setup parameters, can also be provided by the server.
Key Components
- DHCP Server: This part keeps track of IP addresses and configuration information and distributes addresses to clients on a dynamic basis.
- A device (such a PC, phone, or printer) that asks the server for and receives network settings is known as a DHCP client.
- A predetermined range of IP addresses that the DHCP server controls and that devices may lease is known as the IP Address Pool (Scope).
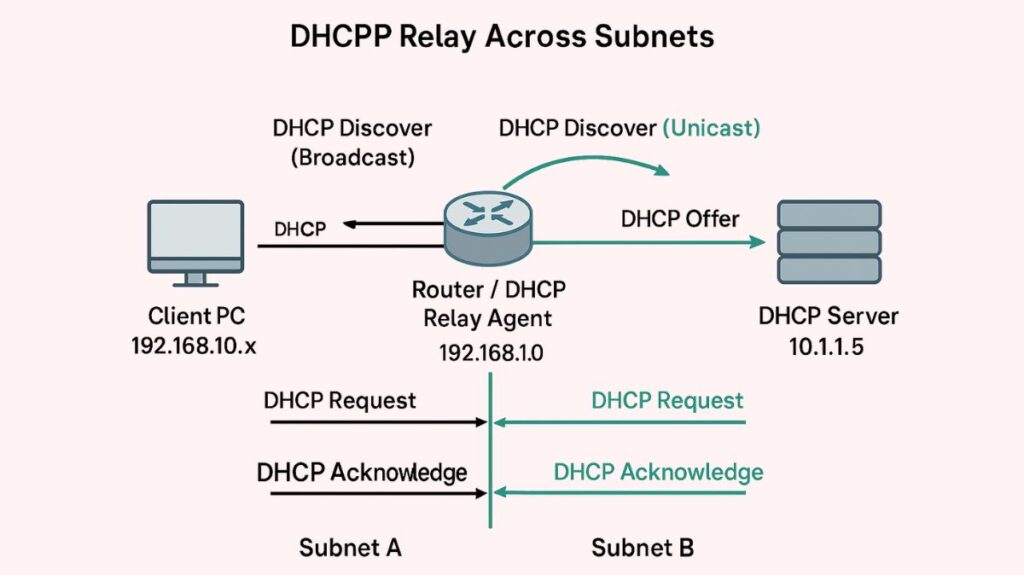
- A TCP/IP host, frequently a router, that serves as a bridge between clients and servers when they are not on the same subnet is known as a DHCP Relay Agent. After receiving the client’s broadcast, relay agents use unicast to send it to the DHCP server.
- Subnets are logical divisions of an IP network used for managing and organising IP distribution.
- Lease: The duration for which a client is given an IP address. The client must request a new lease or extend the existing one after it expires.
- DNS Servers: DHCP can give clients the DNS server details they need to resolve domain names.
- Default Gateway: To enable communication with clients outside of their subnet, the gateway router details are supplied.
- Options: Extra settings such as time servers, domain names, and subnet masks.
DHCP Packet Format
- Hardware Length (8 bits): MAC address length (6 bits for Ethernet, for example).
- Hop Count (8 bits): The most hops that a packet is capable of making.
- Requests and responses are matched using the 32-bit transaction ID that the client sets.
- Seconds (16 bits): The amount of time that has passed since the client began to boot up.
- Flags (16 bits): The broadcast reply requirement is indicated by the leftmost bit.
- Client IP Address (4 bytes): 0 if the client does not already have an IP address, else filled in.
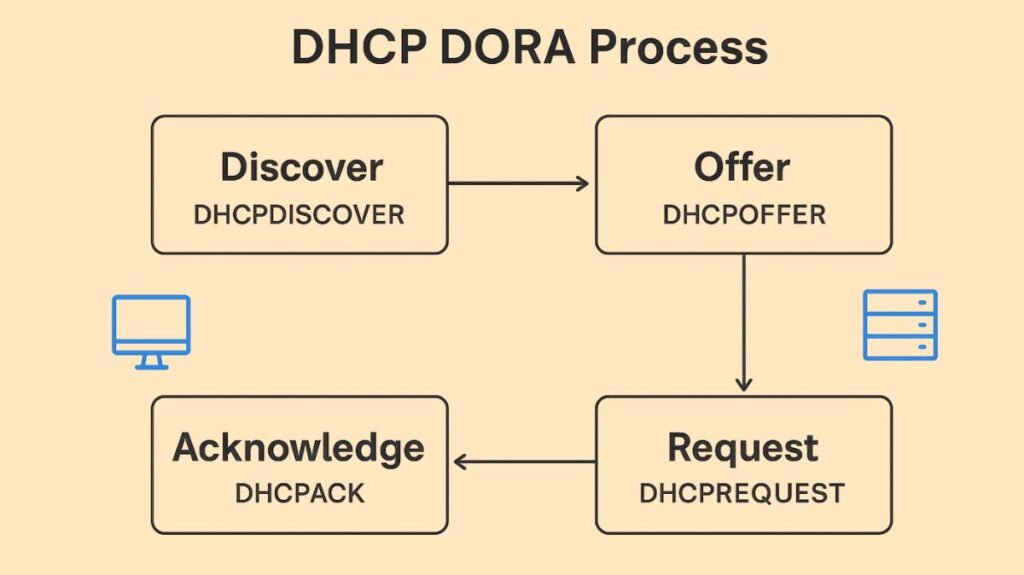
DHCP DORA Process
DHCP uses the connectionless User Datagram Protocol (UDP) to function at the Application Layer. UDP port 67 is used by the server, and UDP port 68 is used by the client.
The abbreviation DORA serves as a summary of the four main messages that are usually exchanged between the client and server:
Discover (DHCPDISCOVER): This message is broadcast when a client initially connects to the network in order to locate any DHCP servers that are available. The packet is sent with a source IP address of 0.0.0.0 and a destination IP address of the broadcast address, 255.255.255.255, because the client does not have an IP address. Most of the time, the Layer 2 broadcast address is all Fs (ff:ff:ff:ff:ff:ff).
Offer (DHCPOFFER): Any DHCP server that gets the Discover message replies by sending a DHCPOFFER message and setting aside an IP address for the client. The suggested IP address, subnet mask, default gateway, and lease term are all included in the deal.
Request (DHCPREQUEST): The client broadcasts a DHCP Request message formally requesting to lease the provided configuration after choosing one offer, usually the first one received. Any additional servers that offered to accept can do so by broadcasting this request, which returns the IP address to their pool of accessible servers.
Acknowledge (DHCPACK): To validate the lease and complete the assignment of the IP address and network configuration information, the chosen DHCP server sends a final DHCP Acknowledge message. Additionally, the server adds the client’s IP address and lease duration permanently.
Eight potential messages are defined by the DHCP protocol:
Also Read About What is IP Spoofing Attack and How IP Spoofing Works
DHCP Discover Message
- When the client and server communicate, this is the initial message that is produced.
- The client host generates this message to determine whether or not a DHCP server or servers are present in a network.
To locate the DHCP server, this message is sent to every device connected to the network. The length of this message is 342 or 576 bytes.
DHCP Offers Message
- In this message, the server will reply to the host with the unleased IP address and further TCP configuration details.
- The server broadcasts this message. The message is 342 bytes in size.
- The client host will accept the first DHCP OFFER message it receives if the network has several DHCP servers. In order to identify the server, the packet also includes a server ID.
DHCP Request Message
- A client broadcasts a DHCP request message in response to an offer message.
- To determine whether another host with the same IP address is present in the network, the client will generate a gratuitous ARP.
- The message is sent to the server, indicating that the IP address has been accepted if no other host responds, indicating that there are no hosts in the network with the identical TCP setup. This message also includes a Client ID.
Also Read About Cisco ARP Spoofing Attack Prevention And Detection Guide
DHCP Acknowledgment Message
- The server will bind the IP address provided with the lease time and make an entry with the specified client ID in response to the request message received. The IP address supplied by the server will now be available to the client.
- The client host’s IP address and lease duration will now be entered by the server.
- No other host will receive this IP address from the server.
DHCP Negative Acknowledgment Message
- A DHCP NACK message is sent to the client whenever a DHCP server gets a request for an IP address that is invalid based on the defined scopes.
- Example: The server sends this message to the client when it has no unused IP addresses or when the pool is empty.
DHCP Decline
- A DHCP decline message is sent to the server by the DHCP client if it finds that the provided configuration settings are incorrect or different.
- The client sends a DHCP refuse message to the server indicating that the provided IP address is already in use when any host responds to the client’s gratuitous ARP.
DHCP Release
To release the IP address and stop any remaining lease time, a DHCP client sends the server a DHCP release packet.
DHCP Inform
- The client uses DHCP information to retrieve other local configuration options, like a domain name, if the client has manually received an IP address.
- Without assigning a new IP address, the DHCP server responds to the DHCP notify message by creating a DHCP ack message with a local configuration appropriate for the client.
- The client receives this DHCP ack message unicast.
Also Read About What is IP Routing, How IP Routing Works, and Types
DHCP Address Allocation Methods
DHCP servers can assign addresses using a variety of techniques:
Dynamic allocation: For a predetermined amount of time (lease), the server distributes addresses from a reserved pool.
Automatic allocation: An IP address from the specified range is permanently assigned by the server, frequently giving the client their old IP address in preference.
Manual allocation (Reservation): An administrator assigns a fixed IP address to a client’s unique identification, like a MAC address.
DHCPv6 and IPv6 Addressing
Stateless Address Autoconfiguration (SLAAC) and Stateful DHCPv6 are the two ways that IPv6 automatically generates a global unicast address.
Stateful DHCPv6: This protocol offers both the network ID and the host ID and functions conceptually similarly to DHCP in IPv4. For messages sent to DHCPv6 servers, DHCPv6 utilises the multicast address FF02::1:2. To route these messages, a DHCPv6 relay agent must substitute the DHCPv6 server’s unicast address for the multicast address.
SLAAC or Stateless DHCPv6: SLAAC, also known as Stateless DHCPv6, uses Neighbour Discovery Protocol (NDP) packets to let a device know its full global unicast address. Stateless DHCPv6 is frequently used in conjunction with SLAAC to offer extra configuration choices, including DNS server addresses, that SLAAC is unable to manage.
Security Concerns and Mitigation
Due to its absence of built-in authentication procedures, DHCP is susceptible to some types of attacks.
Key Threats
- A Man-in-the-Middle (MITM) attack may be made possible by rogue DHCP servers (spoofing), which are unapproved servers that join the network and assign harmful IP configurations (such as erroneous default gateways or DNS addresses).
- DHCP Starvation Attacks: To lease every IP address in the pool (scope), an attacker uses a large number of DHCP Discover messages with fake client MAC addresses (DHCP chaddr). As a result, legitimate clients looking for an address are subject to a denial-of-service (DoS) issue.
Mitigation with DHCP Snooping
Implementing DHCP Snooping on Layer 2 switches reduces the impact of both DHCP spoofing and hunger attacks.
By analysing incoming DHCP signals, DHCP Snooping works similarly to a firewall or Access Control List (ACL):
Trusted vs. Untrusted Ports: Switch ports can be classified as either untrusted (where clients connect) or trusted (allowing all incoming DHCP messages, usually connecting to the authentic DHCP server or relay agent). Incoming messages marked as DHCP server messages (Offer/ACK) are always rejected by untrusted ports.
Binding Table: A dynamic DHCP Snooping binding table is created by DHCP Snooping. Along with the client’s IP address, MAC address, VLAN, and switch port, this table documents successful DHCP leases. For Dynamic ARP Inspection (DAI) to validate ARP communications, this table is essential.
Filtering Client Messages: By ensuring that the client hardware address (chaddr) field in the DHCP message and the Ethernet frame source MAC address match, DHCP Snooping filters client messages (Discover and Request) on untrusted ports. The message is rejected if the values do not match, which is a tactic employed in hunger attacks.
Rate restriction: To defend the switch CPU from DoS attacks, DHCP Snooping allows optional rate restriction, which sets a maximum amount of DHCP packets per second per port (for example, by using ip dhcp snooping limit rate number). When this limit is exceeded, the port becomes err-disabled.
DHCP Address Conflicts

When two hosts share an IP address, it’s known as a DHCP address dispute.
- Detection: Before allocating an address, the DHCP server uses the Ping utility to look for conflicts. In order to find duplicates, the client also uses its newly given IP to transmit a gratuitous ARP broadcast.
- Resolution: In the event that a conflict is found, the IP address is taken out of the DHCP pool and won’t be redeployed until the problem is manually fixed by an administrator.
Later Windows operating systems may use Automatic Privat to automatically configure an IP address and subnet mask in the 169.254.0.1 through 169.254.255.254 range if a client does not receive a DHCP offer.
Also Read About What is DHCP Option 82? How it Works, Benefits & Components
