This page covers Intrusion Detection System (IDS) Core Functionality and Characteristics, Detection Methods, How an IDS Works, Classification, Importance and Benefits, Limitations and Evasion Techniques, IDS vs Firewall vs IPS, and more.
Intrusion Detection System (IDS)
A security tool or application known as an intrusion detection system (IDS) keeps an eye on a network or system in a passive manner for indications of suspicious activity, policy violations, or hostile conduct. Its main purpose is to identify possible risks and notify administrators of them; it doesn’t automatically block traffic.
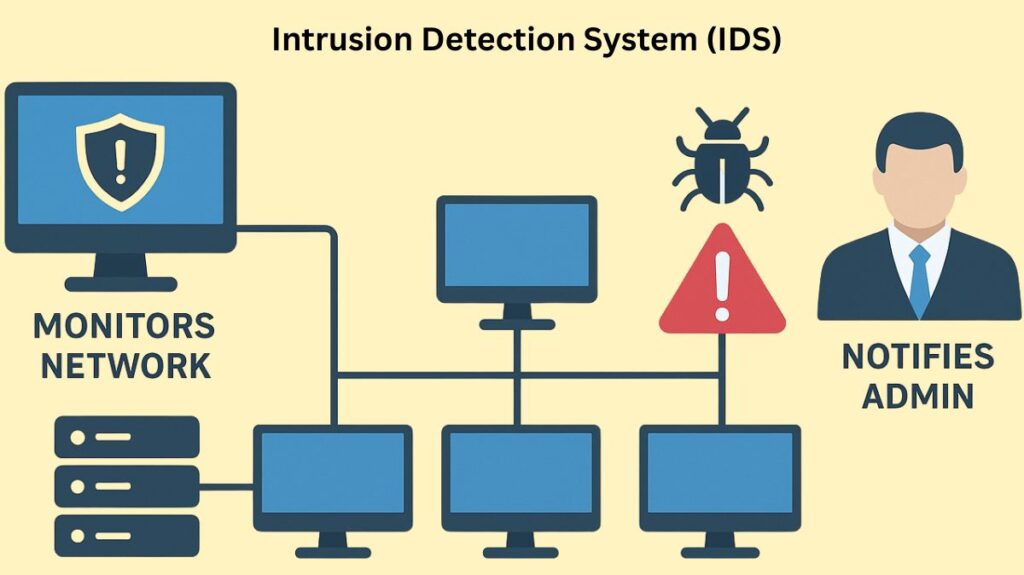
Core Functionality and Characteristics
The passive and detection-focused features of the intrusion detection system are what make it unique:
Passive Detection: One type of passive detection system is an intrusion detection system (IDS). In contrast to an intrusion prevention system (IPS), an intrusion detection system (IDS) is able to identify an attack, record the incident, and produce an alert; however, it does not automatically reject or stop the attack from spreading further throughout the network.
Response Action: The IDS’s primary functions include recording the event data and producing an alert (such as sending an email or alerting a Security Information and Event Management (SIEM) system) when a possible threat or policy violation is discovered.
Placement (Out-of-Band): Usually, an intrusion detection system is set up “off to the side,” or out of band, so that traffic does not flow through it directly. Usually via a network tap or mirrored port, it gets a copy of the traffic stream to examine.
Performance Impact: Its out-of-band location has the advantage of not delaying the initial network traffic. Moreover, network flow and throughput are unaffected in the event that the IDS sensor malfunctions.
How an IDS Works
An intrusion detection system (IDS) keeps an eye on network traffic in order to spot trends and indications of unusual activity. It looks for patterns and pre-established rules in network behavior that could point to an intrusion.
Placement Strategy An IDS’s placement is crucial:
- The most popular location is behind the firewall, which gives the intrusion detection system (IDS) excellent view into incoming network data.
- Internal Network: Installing an intrusion detection system (IDS) inside the actual network exposes attacks or questionable activity occurring within the network, making it more difficult for intruders to move freely after they have gained access.
Also Read About What is uRPF Unicast Reverse Path Forwarding & How it Works
Detection Methods
IDS solutions identify threats using a variety of methodologies:
- Signature-Based Detection (SIDS): This technique looks for recognized patterns (signatures) in network packets that are connected to particular risks, including malicious instruction or byte sequences in traffic. This technique can quickly identify assaults whose signatures are already in its database, but it cannot identify novel or unidentified attacks for which there is no pattern.
- Anomaly-Based Detection (AIDS): Developed to identify emerging threats and unidentified malware. It creates a baseline model of reliable behavior using machine learning. Behavior is marked as suspicious if it substantially departs from this model. Although this method can identify assaults that haven’t been discovered yet (like zero-day exploits), it is prone to false positives, which occur when normal but odd activity is mistakenly reported as malicious.
- Other Methods: Other techniques include Reputation-Based Detection, which blocks traffic from IP addresses or domains linked to malicious conduct, and Policy-Based Detection, which monitors activity against administrative security regulations.
Classification of Intrusion Detection Systems
IDS systems are mainly divided into groups according to the areas in which they are installed and the range of activities they keep an eye on:
| Type | Acronym | Description |
|---|---|---|
| Network Intrusion Detection System | NIDS | Monitors traffic to and from all devices on the entire subnet, deployed at strategic points within the network. |
| Host Intrusion Detection System | HIDS | Installed on individual hosts (endpoints/devices). It monitors local activity, such as system files (comparing snapshots) and inbound/outbound packets for that device only. |
| Hybrid Intrusion Detection System | Hybrid IDS | Combines two or more approaches, typically blending host data with network information to develop a comprehensive view. |
| Application Protocol-Based IDS | APIDS | Monitors and interprets communication on application-specific protocols, usually residing within a group of servers (e.g., monitoring SQL transactions between a web server and a database). |
| Protocol-Based IDS | PIDS | Resides at the front end of a server, controlling and interpreting the protocol (e.g., monitoring HTTPS protocol stream to secure a web server). |
Importance and Benefits
Because it may detect attacks that manage to get past firewalls and other primary defenses, intrusion detection systems (IDS) provide an additional layer of protection to a cybersecurity setup.
Important advantages include:
- Threat Detection: IDS finds questionable activity and notifies the system administrator before serious harm is done.
- Improved Visibility: It helps find security flaws by producing insightful data about network activity.
- Compliance: By keeping an eye on network activity and producing the required paperwork and reports, IDS can assist an organization in meeting compliance standards.
- Faster Response: Compared to manual monitoring, immediate warnings enable firms to identify and address any threats more rapidly.
Also Read About What Is Root Guard In Networking? Root Guard Vs BPDU Guard
Limitations and Evasion Techniques
IDS solutions are useful, but they have various drawbacks and restrictions.
- False Alarms (False Positives): IDS have the potential to produce false positives, which can warn about innocuous activity and lead to needless worry or “operator fatigue.”
- No Prevention: Although an intrusion detection system (IDS) can identify and warn of attacks, it cannot prevent them on its own; the use of an IPS or firewall is necessary.
- Resource and Maintenance Requirements: In order for IDS to continue working, it needs to be updated and tuned on a regular basis, which can take time.
- Encrypted Traffic: Without the associated decryption key, the majority of intrusion detection systems are unable to process encrypted packets, enabling incursions to continue undetected.
Attackers employ a variety of strategies to avoid detection:
- Breaking up a packet into tiny pieces in order to evade detection systems that seek out big signatures is known as fragmentation.
- Address Spoofing/Proxying: Using phony or inadequately secured proxy servers to conceal the attack’s origin.
- Pattern Evasion: Modifying attack techniques just enough to evade detection by intrusion detection systems that search for particular patterns.
- Obfuscation/Encoding: Using techniques like Base64 or hexadecimal to conceal harmful content, or making a communication difficult to understand.
- Coordinated Attacks: When several attackers or ports are used to scan a network, the IDS becomes confused and correlation becomes challenging.
IDS vs IPS
Intrusion Prevention System (IPS) vs. IDS Core detection capabilities are shared by IDS and IPS, but their deployment and response strategies are very different:
| Feature | IDS (Intrusion Detection System) | IPS (Intrusion Prevention System) |
|---|---|---|
| Function | Detects malicious activity and alerts | Detects and actively blocks malicious activity |
| Mode of Operation | Passive (monitor only) | Active (monitor + prevention) |
| Placement in Network | Out-of-band (receives copied traffic via SPAN/TAP) | Inline (directly in the traffic flow) |
| Traffic Handling | Does not affect traffic flow | Can block, drop, or modify traffic |
| Response | Alerts security team | Takes immediate preventive action |
| Accuracy Issues | False positives generate alerts only | False positives can block legitimate traffic |
| Use Case | For monitoring, logging, and forensic analysis | For real-time threat prevention and control |
| Analogy | Security camera (watches and alerts) | Security guard (watches and stops intruders) |
IDS = Detection + Alerts (no blocking).
IPS = Detection + Prevention (blocks threats in real time).
Many businesses integrate these features into a single system known as an Intrusion Detection and Prevention System (IDPS).
IDS vs Firewall
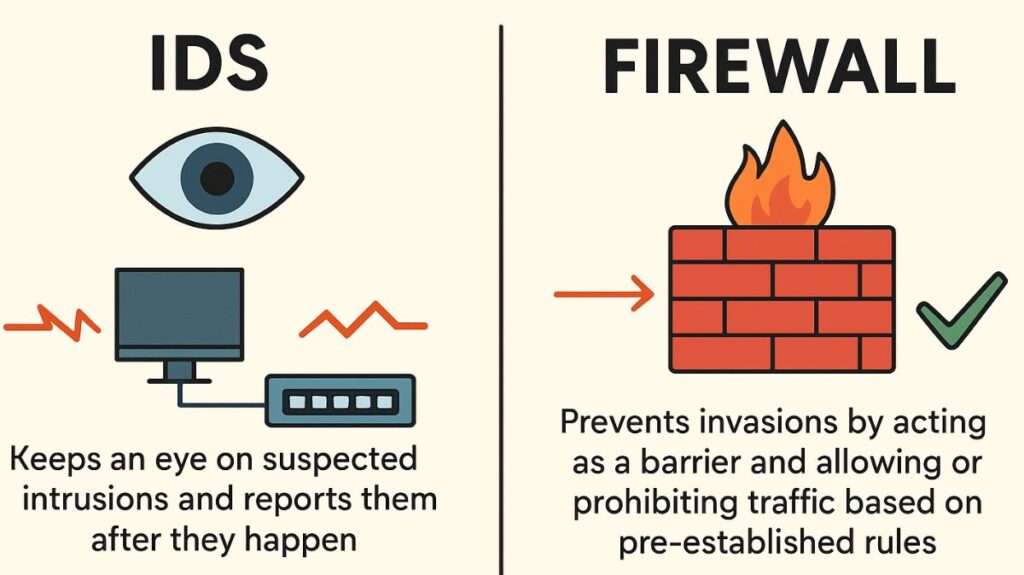
IDS vs Firewalls Although they are both related to network security, their main goals are different:
| Feature | IDS (Intrusion Detection System) | Firewall |
|---|---|---|
| Primary Function | Monitors network traffic for suspicious activity and alerts administrators. | Controls and filters incoming and outgoing network traffic based on security rules. |
| Main Purpose | Detection of attacks or unauthorized access. | Prevention of unauthorized access. |
| Operation Layer | Works mainly at the network and application layers. | Operates at the network and transport layers. |
| Action Type | Passive-alerts or logs suspicious activities. | Active- blocks or allows traffic based on rules. |
| Response | Detects and reports intrusions; may use automated responses in IPS systems. | Prevents unauthorized access by blocking malicious packets. |
| Traffic Monitoring | Monitors all network traffic for anomalies or attack patterns. | Filters traffic based on predefined access control lists (ACLs). |
| Awareness | Can detect internal and external threats. | Primarily defends against external threats. |
| Placement in Network | Typically placed inside the network to monitor internal activities. | Usually placed at the network perimeter (gateway). |
| Example Technologies | Snort, Suricata, Zeek (Bro). | Cisco ASA, pfSense, Palo Alto Firewall. |
| Integration | Can work alongside a firewall for comprehensive security. | Forms the first line of defense in a network. |
- Firewall: Prevents invasions by acting as a barrier and allowing or prohibiting traffic based on pre-established rules. Network access is restricted by firewalls.
- IDS: Keeps an eye on suspected intrusions and reports them after they happen. IDS assists in identifying threats that have evaded the firewall. IDS monitors for internal attacks, but firewalls typically do not alert users to attacks coming from within the network.
Also Read About Common Network Security Vulnerabilities And Exploitation
