Trunking Protocol
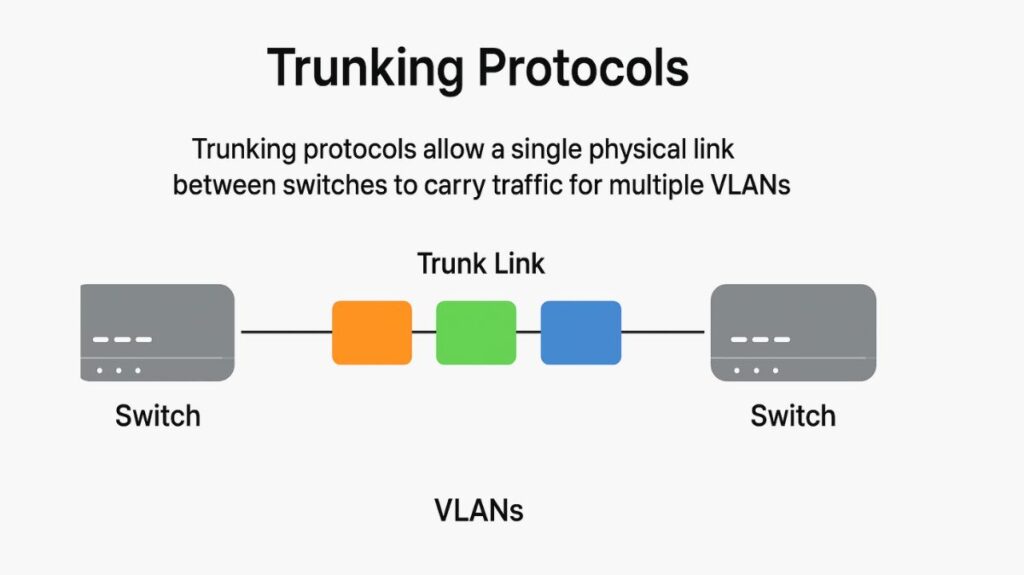
Trunking protocols are essential mechanisms that allow a single physical link between network devices, usually switches, can carry traffic for numerous Virtual Local Area Networks (VLANs) at the same time with trunking protocols. Often called frame tagging or VLAN identification, switches utilize these tags to identify frames that belong to various VLANs as they move across the network.
How Trunking Protocols Work
Trunking protocols work fundamentally by labelling data frames as they move across the trunk link. Every data frame has a little header allocated to it that indicates the VLAN to which it belongs. The frame is routed to the appropriate VLAN when the tag is read when it reaches its destination switch. What distinguishes trunking from merely combining several physical lines is this labelling procedure.
You can also read What Is Dynamic Trunking Protocol CISCO And Characteristics
Benefits of Trunking
Trunking provides contemporary network infrastructures with a number of noteworthy benefits, including:
- Increased Bandwidth Utilization: Through trunking, several VLANs can share a single, high-capacity link rather than needing their own physical link.
- Network Scalability: Adding new VLANs is simple and doesn’t need running new cables.
- Simplified Network Design: It lowers the complexity of physical cabling and the number of switch ports needed.
- Flexibility: By enabling logical network segmentation, trunking improves security and manageability.
- Cost Reduction: Lower infrastructure and maintenance costs result from fewer cables and network connections.
Key Trunking Protocols
In network trunking, a number of essential protocols are employed, some of which are proprietary and others are industry standards:
IEEE 802.1Q (Dot1Q)
- The industry-standard protocol for tagging frames is 802.1Q, which guarantees equipment from various manufacturers can work together. That is currently the most popular trunking protocol.
- Method of Tagging A 4-byte (32-bit) tag is added straight to the Ethernet frame header. Included in this tag are:
- VLAN ID (VID): Up to 4096 VLANs can be specified by this 12-bit field, which indicates which VLAN the frame belongs to.
- Priority Code Point (PCP): A 3-bit variable that is used to prioritize Quality of Service (QoS).
- Drop Eligible Indicator (DEI): When there is network congestion, a 1-bit field is utilized to indicate which frames can be dropped.
- Canonical Format Identifier (CFI): Token Ring frames may be sent over Ethernet lines more easily because to this 1-bit field.
- A “native VLAN,” which is supported by Native VLAN 802.1Q, allows frames that belong to this VLAN to be routed over the trunk untagged. Configuration can be made simpler, but careful monitoring is needed to prevent security problems like VLAN hopping attacks. For this, a unique and unused VLAN is suggested.
Canonical Format Identifier (CFI)
- One Cisco-exclusive legacy trunking protocol is called Proprietary ISL. Although it was important historically, 802.1Q has mostly replaced it because it is not a standard. A lot of the more recent Cisco switches don’t support ISL.
- Captioning ISL encapsulates the original Ethernet frame in a new ISL header (26 bytes) and trailer (4 bytes), increasing the frame size by 30 bytes in contrast to 802.1Q’s internal tagging. Additional information that is helpful in some network configurations, including source and destination MAC addresses, can be carried by it.
- No Native VLAN There is no native VLAN concept in ISL; all traffic is tagged.
- VLAN Support It can accommodate up to 1000 VLANs.
Dynamic Trunking Protocol (DTP)
- Cisco Proprietary Negotiation Both the trunk port status and the trunk encapsulation type (either 802.1Q or ISL, for switches that support both) are automatically negotiated by the Cisco-proprietary DTP protocol. It works with 802.1Q or ISL but is not a tagging protocol in and of itself.
- Trunking Modes DTP only handles trunk negotiation if the other switch’s port is DTP compatible. There are multiple modes that Cisco Catalyst switches support:
- Access: It is not permitted to trunk the port; it always functions as an access (non-trunk) port.
- Trunk: Always acting as a trunk port, the port tries to turn the nearby link into a trunk.
- Dynamic Desirable: The port dynamically determines whether to begin using trunking by actively initiating and responding to negotiation messages.
- Dynamic Auto: In order to respond and discuss whether to employ trunking, the port must first passively wait for trunk negotiation signals.
- Nonegotiate: This command can only be used if the neighbour interface is manually designated as trunk or access, and it stops the interface from producing DTP frames.
- Recommendation In order to avoid unauthorized trunk negotiation, Cisco generally advises against utilizing DTP for automatic negotiation and instead advises manually configuring switch ports to trunk mode (switchport mode trunk).
You can also read Cisco VLAN Troubleshooting Commands And VLAN Issues
VLAN Trunking Protocol (VTP)
Cisco Proprietary Management
Designed to control the creation, removal, and renaming of VLANs within a switched network, VTP is a proprietary Layer 2 communications protocol owned by Cisco. Synchronizing VLAN definitions and preserving VLAN information consistency among switches in the same VTP domain are its goals. ISL and 802.1Q trunks can be used to send VTP ads.
VTP Domain
Every switch that belongs to the same domain has the same VTP domain name. Cisco switches can be manually configured or inherit a VTP domain name when they get an advertisement. By default, they do not have one.
VTP Modes
There are three main modes:
- Server (Default mode): Permits VLAN creation, update, and deletion. Any modifications performed in this mode are broadcast to every other switch within the same VTP domain. NVRAM is used to save configurations.
- Client: VLANs cannot be created or deleted, however VTP changes are received and forwarded. If the switch is reset, configurations are lost since incoming updates are not stored in NVRAM.
- Transparent: Does not update its VLAN database or take part in VTP itself, although it does forward VTP summary ads via trunk lines. Switches in transparent mode are able to keep their own local database apart from other switches.
Configuration Revision Number
A 32-bit value used to monitor changes to the VLAN database. Clients alter their configuration if the received number exceeds their own, and this number rises by one with each change made to a server switch.
VTP Pruning
By limiting flooded Broadcast, Unknown Unicast, and Multicast (BUM) traffic on trunk lines that route to switches in certain VLANs that have no customers, this function conserves capacity. throughout it to be active throughout the whole VTP domain, it must be enabled on a single VTP server.
VTP Versions
- Version 1 Default for Cisco switches that are older. If the domain and version match, transparent switches will only relay VTP messages. The standard VLAN range (1–1005) is supported.
- The Version 2 for contemporary Cisco switches by default. Transparent switches transmit VTP messages without checking the version number or domain name. Extended VLAN range (1006-4094) is supported in transparent mode.
- In ads, Version 3 supports the wider VLAN range (1006-4094) (V1 and V2 only function with 1-1005). Private VLANs and Multiple-Spanning-Tree (MST) data are supported. By using primary/secondary server ideas, it provides improved authentication and more control over the VLAN database to avoid revision overwrite problems. In addition, it allows you to fully disable VTP, unlike v1/v2, which simply provide transparent mode.
Exam Relevance and Usage: Exam Many businesses decide to disable VTP because it is mainly ignored in the current CCNA 200-301 exam blueprint.
Link Aggregation Control Protocol (LACP)
IEEE 802.3ad defines LACP as a port trunking technique that merges several physical links into a single logical link. Its main objective is to boost bandwidth and offer redundancy between switches and other network devices, as well as between a switch and a server.
You can also read IP Connectivity Requirements, How it Works, and Importance
Trunking Protocols Use Cases
In contemporary network architectures, tunnelling protocols are essential, especially in:
- Enterprise Networks: Dividing up departments (such sales, IT, and human resources) for security and efficiency in enterprise networks.
- Data Centers: Separate network environments for various tenants or applications.
- Service Provider Networks: Providing services via common infrastructure to numerous clients.
- Inter-VLAN Routing: For traffic routing across various VLANs, inter-VLAN routing trunking is essential, particularly in “router-on-a-stick” (ROAS) configurations, in which a router employs VLAN trunking on a single Ethernet interface.
Trunking Configuration and Verification (Cisco Switches)
Basic Configuration: Simply adding the switchport mode trunk interface subcommand on both sides of the link can statically configure trunking.
Encapsulation Command: On switches that support both ISL and 802.1Q (e.g., Cisco Catalyst 3560), the switchport trunk encapsulation {dot1q | isl | negotiate} command is used to configure or negotiate the trunking type.
Verification: Commands like show interfaces [name] switchport can be used to validate trunk configurations, showing the administrative and operational modes, and the trunking encapsulation. show vlan brief can verify VLANs.
Troubleshooting: Common trunking issues include interface status (must be up/up), matching encapsulation types, and allowing necessary VLANs on the trunk. Mismatched native VLANs can also cause issues.
You can also read Basic VLAN Configuration: Guide To Setting Up A Virtual LAN
