Access Control Lists (ACLs), its components and structure, how it works, types of access control list, ACL rules, uses, benefits, and RBAC vs ACL were all covered in this blog.
Access control list definition in networking
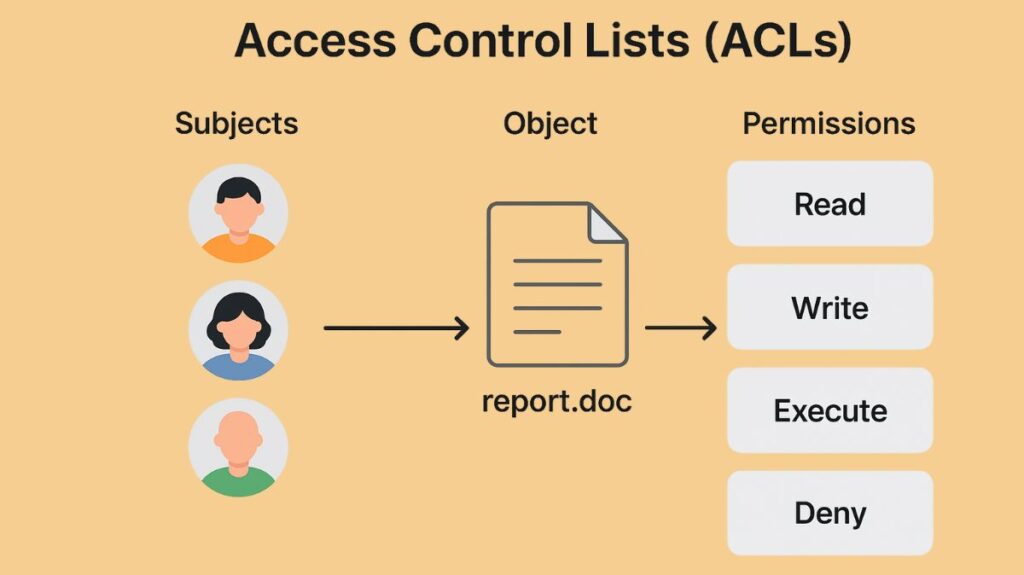
A series of rules known as an Access Control List (ACL) establishes which users or system processes are authorized to access a certain system resource, like a file, network, or cloud storage object, and what actions they are permitted to take. ACLs regulate access and stop unwanted use by defining who is and is not permitted, much like a guest list. They serve as a security filter and are frequently used in operating systems to control access to files and directories as well as in network devices like routers and firewalls.
Key Components and Structure
One or more Access Control Entries (ACEs) make up rule-based lists known as ACLs. Every ACE is a statement that usually specifies an object’s access permissions.
Also Read About NAC Use Cases And How Does Network Access Control Work
(Subject, Action, Effect) is a typical ACE format:
| Component | Description |
|---|---|
| Subject | The user ID, group ID (e.g., Group: MarketingTeam), or process requesting access. |
| Object/Resource | The target, such as a file, directory, network port, or database table. |
| Action/Permission | The allowed or denied operation, such as Read, Write, Execute, Modify, or Delete. |
| Effect | The result of the rule: Permit or Deny. |
Additional elements for network ACLs may consist of an ACL name, a sequence number for identification, comments for descriptions, the network protocol (such as IP, TCP, or UDP), and source and destination IP address definitions.
How Access Control Lists Work
The order of an ACL’s entries has a significant impact on how it operates:
- Request and Lookup: The system verifies the ACL linked to a resource (Object) when a user tries to perform an operation (Action) on it.
- Sequential Scan: The system reads the list’s ACEs one after the other, usually in a serial fashion from top to bottom.
- Match and Enforcement: No additional rules are reviewed; the first ACE that expressly matches the request’s attributes (user, resource, and action) is implemented right away.
- Implicit Deny: The request is normally rejected by default if the complete list is scanned and no matching ACE (particularly no explicit PERMIT) is discovered. Because of this implicit rejection, each ACL must include a minimum of one permission statement; if not, all traffic will be rejected.
The sequencing of rules is crucial because of their sequential nature, especially when it comes to explicit PERMIT and DENY assertions.
Example:
In a file system, a file named report.doc may have an ACL that says:
- User A: Read and Write
- User B: Just read
- User C: Refuse entry
In networking:
A router’s network ACL could be:
- Permit traffic from
192.168.1.0/24to the server. - Deny traffic from
10.0.0.0/8.
Also Read About What Are The Different Types Of Web Servers And How It Works
Types of access control list
ACLs are extensively utilized in a number of specialized situations in addition to two primary domains:
File System ACLs (FACLs)
Operating systems like Windows and Linux frequently employ them. By giving the operating system instructions on user access permissions and privileges (such as read, write, or execute), file system ACLs control access to files and directories.
Networking ACLs (NACLs)
Similar to firewalls, network ACLs are used on routers and switches to filter traffic and determine which network packets are allowed or prohibited from entering a network segment. They use parameters like IP addresses, ports, and protocols to filter traffic.
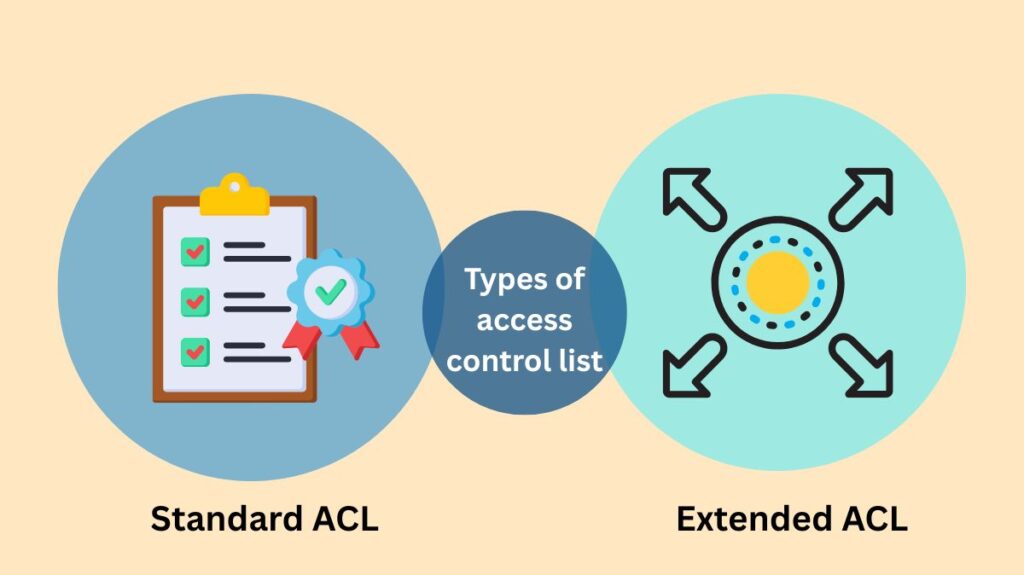
On the basis of granularity, networking ACLs are further divided into:
| Type | Description | Placement Rule (General) |
|---|---|---|
| Standard ACL | Filters traffic solely using the source IP address. They permit or deny the entire protocol suite and cannot differentiate between specific IP traffic types (e.g., TCP, UDP). | Generally applied close to the destination. |
| Extended ACL | Filters traffic using more characteristics, including Source IP, Destination IP, source port, and Destination port. This allows specifying which IP traffic should be allowed or denied. | Generally applied close to the source. |
Another way to group network ACLs is by management style:
Numbered access-list
Numbered access lists are those that, once generated, cannot be removed; that is, if we wish to remove a rule from an access list, we are not allowed to do so. The entire access list will be erased if we attempt to remove a rule from it. Both regular and extended access lists can be utilized with the numbered access list.
Named access list
In this kind of access list, an access list is identified by a name. Unlike numbered access lists, named access lists can be deleted. These work with both extended and standard access lists, much like numbered access lists.
Also Read About Disadvantages Of Web Application Firewall And WAF Functions
Rules for ACL
- Near the destination, the standard Access-list is typically used (but not always).
- Usually, but not always, the extended Access-list is used in close proximity to the source.
- Only one ACL per interface, per protocol, and per direction can be assigned; that is, only one inbound and one outbound ACL per interface is allowed.
- If we are utilizing a numbered Access-list, we are unable to remove a rule from it. The entire ACL will be deleted if we attempt to remove a rule. We can remove a particular rule if named access lists are being used.
- Prior to putting the access lists into effect, carefully consider the entire scenario because each new rule that is added will be positioned at the bottom of the list.
- Since every access list ends with an implicit denial, we should at the very least include a permit statement; if not, all traffic will be rejected.
- The names of extended access lists and standard access lists cannot be the same.
Other Uses
ACLs are also utilised to implement security policies in a number of different systems:
- Network Security: By permitting or rejecting packets according to IP addresses, ports, and protocols, routers and firewalls use network ACLs to regulate traffic flow.
- Operating Systems: ACLs are used to control access to files and directories in Windows and Linux, giving administrators the ability to give or refuse permissions to particular individuals or groups.
- Cloud Storage: ACLs are used by cloud providers like Google Cloud and Azure to specify who has access to particular buckets and items as well as their level of authority.
- Databases: Used to manage who can access which views or tables and what actions (updating, inserting, and querying) they are permitted to take.
- Web servers are commonly used to restrict access to particular websites or web pages according to user agents or IP addresses.
- Virtual private networks, or VPNs, are used to restrict distant users’ and external devices’ access to network resources.
Benefits
ACLs offer a strong foundation for controlling access to resources.
By limiting unwanted access to private information and network resources, ACLs improve security. They give you fine-grained control over who can use a resource and how. ACLs aid in network traffic management, enhancing efficiency and limiting access to particular services in networking environments. They also give admins access attempt records so they can keep an eye on activity.
RBAC Vs ACL
RBAC and ACLs are two radically different methods of access control.
| Feature | Access Control List (ACL) | Role-Based Access Control (RBAC) |
|---|---|---|
| Focus | Object-Centric: Permissions are attached directly to the resource. | Subject-Centric: Permissions are attached to a role, and the user is assigned the role. |
| Granularity | High: Can specify permissions for nearly every single user on every single resource. | Medium: Permissions are grouped into roles, which are more coarse-grained. |
| Scalability | Poor for large organizations; administrative overhead increases significantly. | Good; adding a user involves simply assigning a role. |
RBAC is typically chosen for company-wide systems in large organisations because of its superior scalability and manageability, while ACLs are best suited for extremely precise, fine-grained control over a small number of resources.
Also Read About NTP Server Configuration And How Does NTP Server Work?
