Dynamic ARP Inspection (DAI)
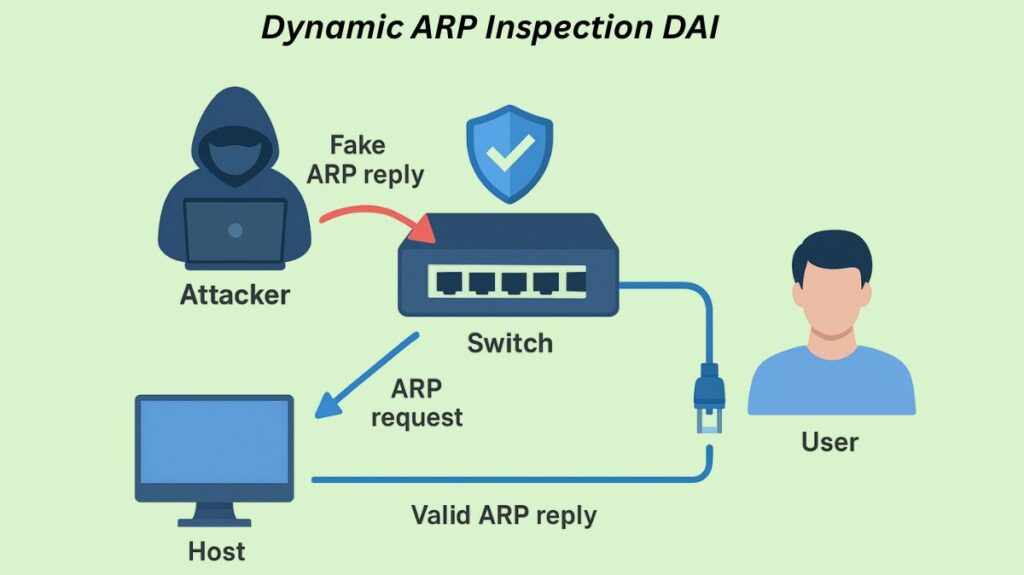
By intercepting ARP packets, comparing their IP-to-MAC address bindings to a trusted database (usually the DHCP snooping database), and discarding those with invalid bindings, Dynamic ARP Inspection (DAI) is a network security feature that stops ARP spoofing (also called ARP poisoning) attacks. By guaranteeing that switches on untrusted ports only forward valid ARP queries and responses, DAI guards against man-in-the-middle attacks.
You can also read Benefits of 802.1X and How 802.1X Authentication Works
Purpose and The Threat it Mitigates
The fundamental purpose of DAI is to protect against ARP spoofing (or ARP poisoning) attacks.
ARP Insecurity: An IP address is mapped to a MAC address via the Layer 2 technique known as ARP. Because it believes every ARP response it gets, even if it isn’t requested, it is intrinsically vulnerable (Gratuitous ARP).
ARP Spoofing/Poisoning: This vulnerability is exploited by an attacker (a rogue peer) who sends forged ARP packets (usually gratuitous ARP messages) that incorrectly associate the attacker’s own MAC address with the IP address of a genuine device, such as a host or default gateway.
Man-in-the-Middle (MITM) Attack: All traffic meant for the legitimate device is diverted through the attacker’s computer when devices (such as switches or end hosts) update their ARP cache with the false binding. DAI stops this redirection.
Denial-of-Service (DoS) Attack: DAI also aids in preventing DoS attacks, in which a hacker sends out a lot of ARP packets in an attempt to overload the CPU of the switch.
How it Works
An ARP request is sent out to the network by a device (Host 1) wishing to find the MAC address of another device (Host 2), and Host B responds with the MAC and IP address. The DHCP server keeps a table that maps IP and MAC addresses and logs the ARP requests and answers. The valid mapping between the network’s MAC address and IP address is maintained by this DHCP server. DAI checks the information in an ARP packet, such as the source IP address, source MAC address, destination IP address, and destination MAC address, against the DHCP server record when it intercepts an ARP packet (either a request or a response).
The ARP packet is permitted to flood towards its destination if the data it contains matches the entry in the DHCP server’s binding table. DIA will take many steps, including creating a DROP log and rate limiting, to stop the possible ARP spoofing attack if it finds that the data in the ARP packets does not match the record on the DHCP server.
Trusted Database Sources
DAI relies on trusted data to determine validity. The primary data sources are:
- DHCP Snooping Binding Table: The most popular dynamically generated database is the DHCP Snooping Binding Table. DAI uses this table to verify that incoming ARP messages are correct since DHCP snooping captures valid IP-to-MAC-to-port mappings discovered during the DHCP procedure.
- ARP Access Control Lists (ACLs): ARP ACLs are required for manually configuring bindings on hosts with statically defined IP addresses (non-DHCP environments). Packets can be filtered by DAI using these ACLs.
- Priority: ARP ACLs take precedence over entries in the DHCP snooping binding database when both techniques are in use.
DAI implementation
DAI relies on the concept of trust states assigned to switch ports.
| Trust State | Connection Type | Inspection Status | Default Status |
|---|---|---|---|
| Untrusted Ports | Typically connected to end-user devices (hosts, PCs). | All inbound ARP packets are subject to DAI validation checks. | All ports are usually untrusted by default when DAI is enabled. |
| Trusted Ports | Connected to trusted network devices (other switches, routers, DHCP servers). | ARP packets bypass DAI validation checks entirely. | Trusted interfaces must be explicitly configured. |
Configuration Requirements and Advanced Features
Prerequisites
DAI is configured globally on a per-VLAN basis. Since DAI relies heavily on the binding table, DHCP snooping must generally be enabled on the relevant Virtual Local Area Networks before DAI is activated.
Optional Validation Checks
Beyond the basic check against the binding table, DAI can be configured to perform additional validation checks, although these often consume more switch CPU resources:
- Source MAC Validation (
src-mac): Checks if the source MAC address in the Ethernet header matches the sender MAC address in the ARP body. - Destination MAC Validation (
dst-mac): Checks if the destination MAC address in the Ethernet header matches the target MAC address in the ARP body (for ARP responses). - IP Address Validation (
ip): Checks for invalid IP addresses, such as0.0.0.0or255.255.255.255.
Rate Limiting
DAI itself is vulnerable to Denial-of-Service (DoS) attacks, in which an attacker creates a high number of ARP packets in an attempt to overload the switch’s CPU, since DAI processing takes place in the CPU of the switch rather than the ASIC.
Rate limiting the quantity of ARP messages permitted on a port over time is supported by DAI in order to lessen this. The port is put in an err-disabled state if the rate limit is exceeded.
Key details about DAI rate limiting:
- DAI defaults to using rate limits for all interfaces (trusted and untrusted), unlike DHCP Snooping.
- DAI allows the configuration of a burst interval (in seconds), enabling rate logic like “x ARP messages over y seconds,” a feature DHCP Snooping lacks.
- Commands can be used to enable automatic recovery from the err-disabled state caused by exceeding DAI rate limits (
errdisable recovery cause arp-inspection).
The command ip arp inspection limit rate number [burst interval seconds] is used to configure t
Verification Commands
Key commands for verifying DAI status and operation include:
show ip arp inspection: Lists configuration settings, status variables, and counters for processed and filtered ARP messages.show ip arp inspection statistics: Lists counters related to DAI, including the number of forwarded, dropped, and permitted DHCP/ACL ARP messages.show ip arp inspection interfaces: Confirms configured rate limits and trust states for interfaces.
You can also read PAT Port Address Translation: How It Works And Limitations
