What is Generic Routing Encapsulation?
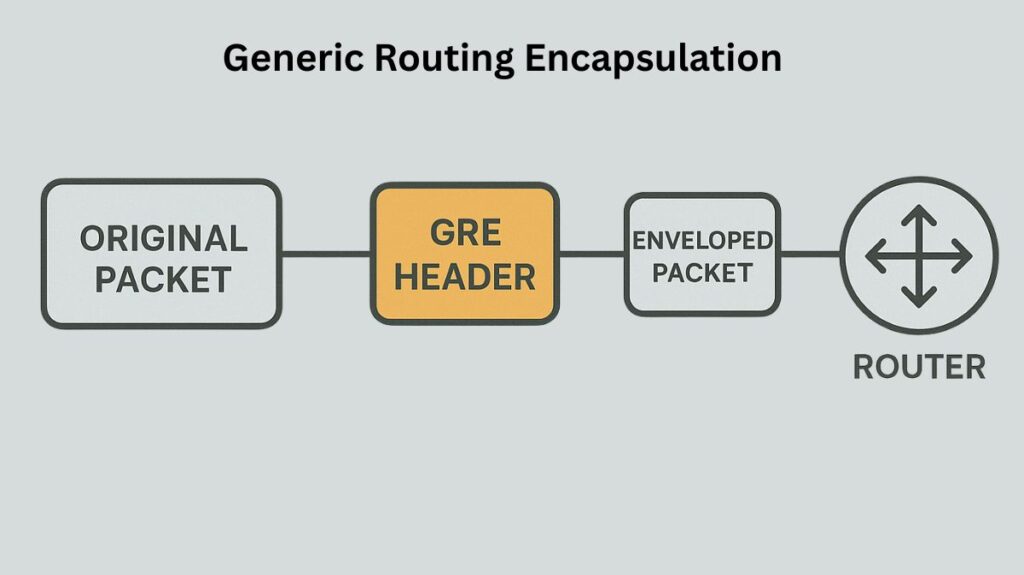
Cisco Systems created the essential and popular tunneling technique known as Generic Routing Encapsulation (GRE). Its main function is to encapsulate one network protocol into another protocol’s packets. GRE enables various network segments or protocols to communicate as though they were directly connected by establishing a virtual point-to-point connection between network endpoints, usually routers.
GRE employs IP Layer 3 protocol number 47 and is described in RFC 2784.
You can also read What is MPLS Layer 2 VPN? Architecture, Types and Benefits
How does GRE Encapsulation Work?
GRE works by adding two further headers to the original data packet, also referred to as the payload packet or inner packet:
- GRE Header (Carrier Protocol): A GRE header encapsulates the initial payload packet. Although this header is normally 4 bytes long, optional data like the checksum, key, and sequence number can make it up to 16 bytes long. It contains crucial metadata, most significantly the Protocol Type field, which indicates the network layer protocol of the enclosed payload (e.g., IPv4, IPv6).
- Delivery Header (Outer IP Header/Transport Protocol): The GRE packet (GRE header with original payload) is then enclosed within a new outer IP header. Both the local tunnel endpoint’s source IP address and the remote tunnel endpoint’s destination IP address are contained in this outer IP header. The following header is a GRE header since the protocol field of the outer IP header is set to 47.
The Encapsulation Process: The Encapsulation Process The original packet is first encapsulated with the GRE header and then the Delivery Header by a GRE-enabled router. After that, the packet travels across the network in this encapsulated state. The path’s intermediate routers merely parse the outer IP packet and forward it in accordance with the remote tunnel endpoint’s destination IP address.
The Decapsulation Process: The decapsulation process restores the original payload packet by removing the outer IP header and the GRE header when the encapsulated packet reaches the tunnel remote router, which is the destination tunnel endpoint. Then, using the information in its inner header, this original packet is routed to its destination.
Key Characteristics and Trade-offs
Security and Statelessness
- No Inherent Security: GRE is a straightforward encapsulation technique that, by default, offers no security; it lacks authentication and encryption. The contents of packets sent via a GRE tunnel are in plain text if they are intercepted on a public network.
- GRE over IPsec: GRE tunnels are commonly encapsulated within IPsec (Internet Protocol Security), which offers authentication and encryption and is extensively utilized in site-to-site Virtual Private Networks (VPNs) to secure communications.
- Stateless Protocol: GRE has no flow control methods and is stateless. There is no information regarding the availability or status of the remote endpoint in the tunnel endpoints.
Overhead and MTU
- Overhead: GRE adds a minimum of 24 bytes of overhead (20 bytes for the outside IP header + 4 bytes for the GRE header) to every tunneled packet.
- MTU Impact: Performance may be impacted by the larger packet size caused by this extra overhead. Usually, it lowers the tunnel’s effective Maximum Transmission Unit (MTU). Fragmentation happens if the packet size after encapsulation is larger than the MTU, which slows down delivery times and uses more resources. In order to prevent fragmentation, it is frequently required to modify the Maximum Segment Size (MSS).
You can also read MLPS Managed Network Providers Improve Network Security
Benefits and Applications
GRE is prized for its adaptability and capacity to handle different kinds of traffic:
- Protocol Independence (Multiprotocol Traffic): The capacity of GRE to tunnel nearly any Layer 3 protocol (the passenger protocol), such as IPv4, IPv6, or even non-IP protocols like IPX, over an IP network is its greatest strength. This is known as Protocol Independence (Multiprotocol Traffic).
- Routing Protocol Support: It makes it possible for dynamic routing protocols, which are essential for automatic route discovery and include OSPF, EIGRP, and RIP, to function across the tunnel.
- Multicast and Broadcast Support: GRE may encapsulate multicast and broadcast traffic, allowing them to traverse networks that generally only support unicast forwarding.
- Connecting Discontiguous Networks: To create a VPN across a wide area network (WAN), GRE builds a transparent communication tunnel. This allows geographically disparate networks to appear as a single private network.
- IPv6 Transition: Encapsulating IPv6 packets and sending them over an existing IPv4-only infrastructure is known as IPv6 transition.
- DDoS Mitigation: Service providers, such as Cloudflare Magic Transit, can use GRE tunnels to reroute client traffic to security scrubbing centers for processing before sending clean traffic back.
Configuration and Verification
Configuring a GRE tunnel requires several steps: utilizing IP addressing, creating the logical tunnel interface (e.g., interface tunnel number), specifying the GRE tunnel mode (which is optional since it is the default), and setting the tunnel source and destination IP addresses. On Cisco IOS, the default tunnel mode is GRE over IP.
A tunnel interface is configured in the routing table as a directly connected interface.
Troubleshooting and verification commands include:
• show ip interface brief.
• show interface tunnel 0.
• Using the ping command to test connectivity across the tunnel.
A common configuration error is the “GRE flapping” message (%TUN-5-RECURDOWN: Tunnel0 temporarily disabled due to recursive routing), which indicates the router is incorrectly configured to try routing to the tunnel destination address using the tunnel interface itself.
Furthermore, Access Control Lists (ACLs) must be configured to specifically permit GRE traffic when implementing tunnels, as GRE is a Layer 3 protocol (not TCP/UDP).
You can also read What is Extranet VPN, Intranet VPN, Purpose & How They Work
