In this article, we learn about what is Remote Authentication Dial-In User Service, RADIUS Components, Architecture, Key Features, Applications, advantages, and disadvantages.
What is Remote Authentication Dial-In User Service?
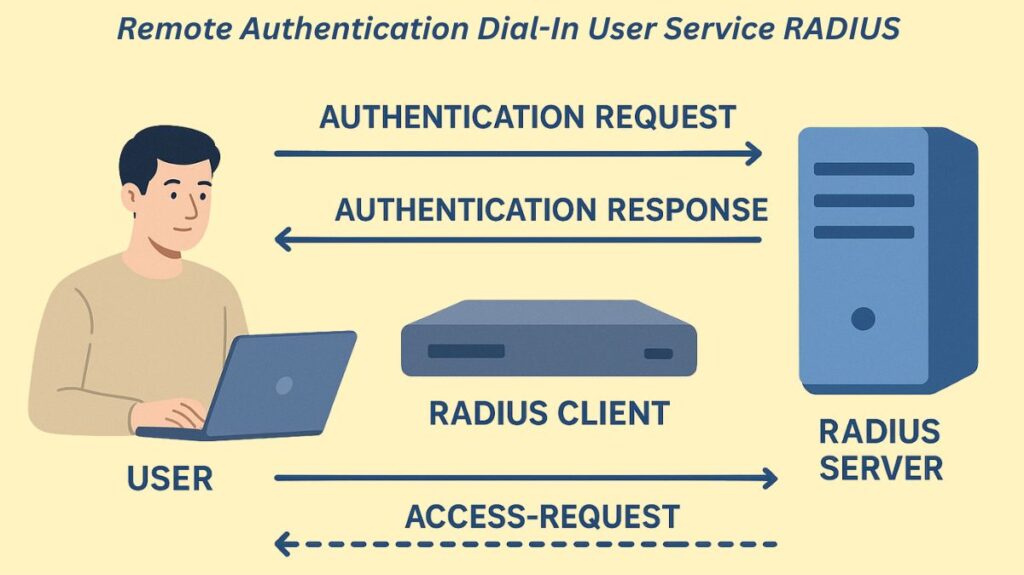
A popular networking protocol that offers centralized authentication, authorization, and accounting (AAA) administration for users gaining access to a network service is called Remote Authentication Dial-In User Service (RADIUS).
In 1991, Livingston Enterprises, Inc. created RADIUS as an authentication and accounting protocol for access servers. The Internet Engineering Task Force (IETF) established this open-standard protocol. RFC 2865 (Authentication/Authorization) and RFC 2866 (Accounting) include the majority of the definitions for the existing standards.
RADIUS Components and Architecture
Architecture and Components
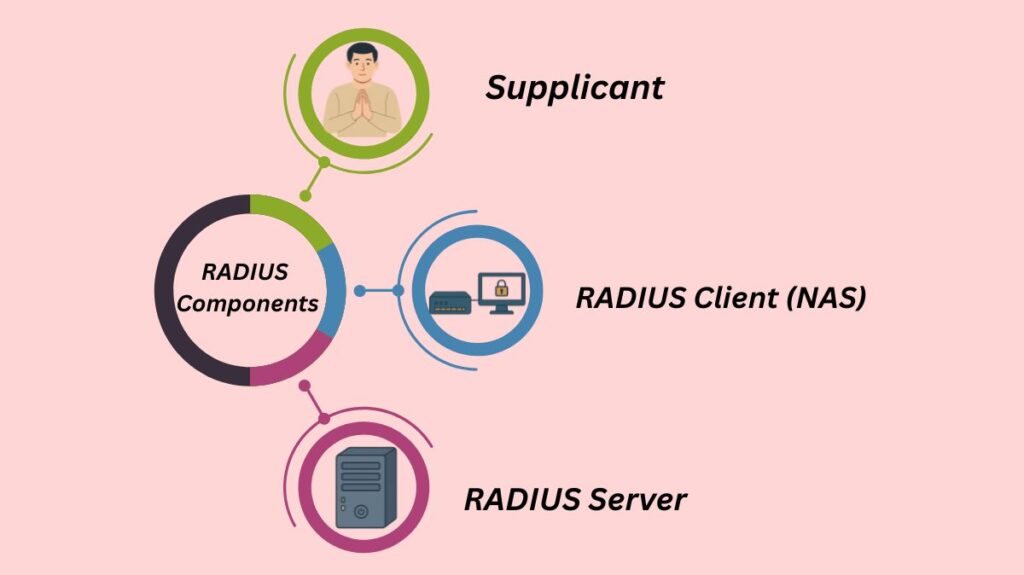
RADIUS operates using a client/server model.
| Component | Role | Examples |
|---|---|---|
| Supplicant | The end-user device or software that requests access. | Laptop, smartphone, tablet. |
| RADIUS Client (NAS) | The Network Access Server (NAS) acts as the gateway or access control point that forwards the user’s request to the RADIUS server. The NAS acts on the response returned by the server. | Wireless Access Point (WAP), VPN Concentrator, 802.1X Switch, routers. |
| RADIUS Server | The central system (often a daemon process running on UNIX or Windows NT/Microsoft NPS) that maintains user authentication/network access information and processes the requests. | Dedicated server application running FreeRADIUS or Windows NPS. |
You can also read Intrusion Detection System IDS Importance & IDS vs Firewall
The AAA Process
The three main components of AAA authentication, authorization, and accounting are implemented by RADIUS.
Authentication and Authorization Flow
Authorization and authentication are combined in RADIUS.
- Request Initiation: The user gives the RADIUS Client (NAS) their login credentials.
- Access-Request: The RADIUS server receives an Access-Request packet from the NAS. The encrypted password, NAS IP address, and username are all contained in this message.
- Verification: The user credentials are compared by the RADIUS server to either a local database or external sources such as Active Directory, SQL, Kerberos, or LDAP.
- Server Response: One of three messages could be sent by the server in response to the NAS:
- Access-Accept (Code 2): The user is given access after successful authentication. The settings for the session, including the particular IP address, Virtual Local Area Network assignments, access list to be used, or service type, are defined by the authorization attributes (attribute-value pairs) included in this message.
- Access-Reject (Code 3): Access is refused due to unsuccessful authentication.
- Access-Challenge (Code 11): Asks the user for more details; frequently used for secure tunnel creation or multi-step authentication.
PAP (Password Authentication Protocol), CHAP (Challenge-Handshake Authentication Protocol), and the more secure EAP (Extensible Authentication Protocol) are among the authentication protocols that RADIUS supports. Because it enables encryption protocols like TLS and sophisticated techniques like smart cards or digital certificates, EAP is typically regarded as the most secure.
Accounting (Session Tracking)
RADIUS’s accounting functionalities are used without authorization or authentication. This procedure keeps track of how much time, packets, bytes, and other resources are used during a session.
- Accounting Start: The NAS signals the beginning of the session by sending an Accounting-Request (Start) packet to the RADIUS server after access has been authorized.
- Interim Updates: To indicate the current session duration and data usage, the NAS may periodically provide Accounting-Request (Interim Update) records.
- Accounting Stop: The NAS transmits a final Accounting Stop record, describing the last usage for billing and auditing purposes, as soon as the user disconnects.
Technical Details and Security
Transport Protocol and Ports
User Datagram Protocol (UDP) is the transport protocol used by RADIUS. Because UDP is quicker and connectionless, RADIUS-enabled devices, not the transmission protocol, are in charge of handling problems like server availability, retransmission, and timeouts.
The standard UDP ports used are:
- Authentication/Authorization: UDP Port 1812 (historically 1645).
- Accounting: UDP Port 1813 (historically 1646).
Security Mechanisms
RADIUS employs particular techniques to protect communication between the server and the client (NAS):
- Shared Secret: A key that is only known to the client and server and is never transmitted over the network is used to authenticate transactions between them.
- Password Encryption: Usually, a technique based on the MD5 hashing algorithm in conjunction with the shared secret is used to transmit encrypted user passwords between the client and RADIUS server.
- Security Limitation: One of the protocol’s biggest drawbacks is that it only encrypts the password in the Access-Request packet; the username and other information are frequently left unprotected. Moreover, legacy RADIUS’s MD5 hashing technique is seen as unsafe. To reduce vulnerabilities like the Blast-RADIUS attack, it is advised to employ protocols like RadSec (RADIUS wrapped in TLS).
You can also read Components of Digital Certificate, How it Works and Benefits
Key Features and Applications
RADIUS is extensively used as the authentication server for modern access control mechanisms:
- 802.1X: A security protocol called RADIUS is utilized in IEEE 802.1X messages that are sent between an AAA server and an 802.1X authenticator, such as a Local area network switch.
- The authentication server in the 802.1X architecture is usually a RADIUS server.
- User credentials are set up on the RADIUS authentication server.
- Wireless LAN Controllers (WLCs): When using 802.1X security, WLCs frequently use RADIUS servers to secure wireless connections.
- RADIUS server configuration is supported by a WLC.
- Network Users (wireless clients) or Management Users (administrators gaining access to the controller) can be authenticated by a RADIUS server when it is configured on a WLC.
- An individual WLAN can specify up to six RADIUS servers, while a WLC can support up to 32 RADIUS servers.
- EAP Methods: EAP-based authentication techniques such as EAP-FAST and EAP-TLS require a RADIUS server.
- WPA2-Enterprise: In order to authenticate users or machines connecting to the wireless network, WPA2-Enterprise mode requires setting up a RADIUS server.
Advantages and Disadvantages
| Feature | Advantages (Pros) | Disadvantages (Cons) |
|---|---|---|
| Management & Scale | Provides centralized authentication and authorization, simplifying administration. Highly scalable for large networks with many users and devices. Reduces manual IT labor. | Complexity to set up and configure, requiring networking expertise. |
| Security | Enhanced network security and access control. Supports a variety of authentication methods (PAP, CHAP, EAP). | Potential single point of failure if the central server goes down, requiring redundant configuration. Security limitations because it encrypts only the password, leaving other sensitive data (like username) vulnerable. Vulnerable to attacks like spoofing and replay attacks. |
| Functionality | Open standard protocol, allowing integration between devices from different vendors. Provides greater extensive accounting support compared to TACACS+. | Does not provide explicit command authorization. |
Configuration and Management
IOS Configuration Snippet
To implement RADIUS on an IOS device with local database fallback:
- Enable AAA:
Router(config)# aaa new-model. - Configure the RADIUS server host and shared secret key:
Router(config)# radius server SecureLoginfollowed byRouter(config-radius-server)# address ipv4 10.10.10.254andRouter(config-radius-server)# key MyRadiusPassword. - Apply the AAA login method, referencing the RADIUS group and specifying
localas the backup method:Router(config)# aaa authentication login default group MyRadiusGroup local. This fallback ensures that if the RADIUS server cannot be reached, local authentication can still be used.
WLC Configuration Details
When configuring RADIUS on a WLC (Wireless LAN Controller), the necessary fields include the server’s IP address, a shared secret key, and the port number (which defaults to 1812). WLC configurations also include:
Server Index: The RADIUS server prioritizes this. It regulates the server’s placement in the selection list. After I select 1 as the value, the next server must be 2 because the Server Index needs to be unique.
Server Address: This is simply the RADUS server’s IP address, which may be either IPv4 or IPv6. Although it’s a little excessive for the CCNA, WLC does support DNS names.
Support for CoA: Configuring Change of Authorization (CoA) functionality enables an 802.1X server, such as Cisco Identity Service Engine (ISE), to modify the authorization outcome of a RADIUS connection.
You can also read What is Dynamic Trunking Protocol DTP Spoofing Overview
