What is Storm Control in Networking?
Network Storm Control is a crucial Layer 2 feature implemented on switches and routers, designed to monitor and regulate incoming traffic levels to prevent network disruptions caused by traffic storms.
The switch removes the extra packets to keep the network from being overloaded with various kinds of traffic, which can lead to poor performance or total network outages, when a port gets more than a predetermined threshold. The threshold can be set in packets per second or as a percentage of bandwidth, and triggering an SNMP trap or temporarily shutting down the interface are two ways to go over it.
Storm Control’s main objective is to prevent network instability by limiting high traffic volumes.
You can also read What is DHCP Option 82? How it Works, Benefits & Components
What is a Traffic Storm?
When a network device is overloaded with broadcast, multicast, or unicast traffic, it’s known as a traffic storm. Hardware malfunctions, network loops, and setup errors can all cause this. A typical illustration is a broadcast storm, in which broadcast packets cause receiving devices to react, starting a domino effect that overwhelms the network with data.
- Causes: Traffic storms are often caused by Layer 2 network loops (where the Spanning Tree Protocol, or STP, has failed or is misconfigured), malfunctioning devices (like a faulty network interface card, or NIC), misconfigured applications, or malicious denial-of-service (DoS) attacks.
- Effects: A strong broadcast storm might overload all links, push out valid frames, dramatically raise switch CPU usage, and result in MAC address table instability, or “thrashing.”
How Storm Control Works?
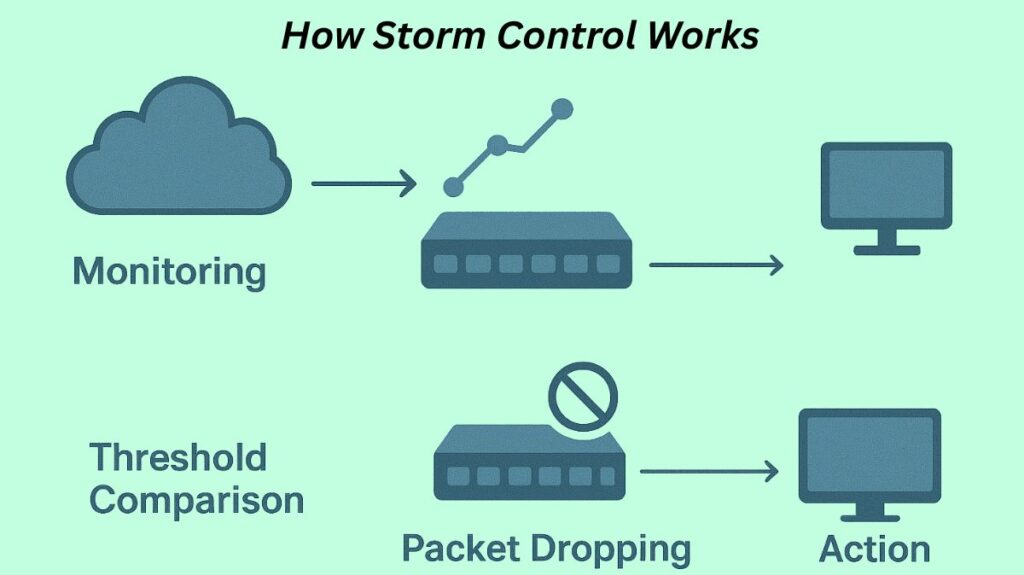
- Monitoring: Storm control keeps track of the volume of incoming traffic for particular categories (broadcast, multicast, and unknown unicast) on a switch port.
- Threshold Comparison: Comparing the monitored traffic rate to a user-specified threshold is known as threshold comparison.
- Packet Dropping: The switch begins to drop or discard extra packets of that kind if the incoming traffic rate rises above this level.
- Action: Once the traffic rate falls below a configured “falling threshold,” the switch may resume forwarding traffic, or the interface might remain shut down or issue an alarm.
Controlled Traffic Types
Storm Control can be configured to limit three specific types of traffic, often referred to as BUM traffic:
| Traffic Type | Description |
| Broadcast | Frames sent to all devices in the VLAN (e.g., ARP requests, DHCP requests). This is the most common target. |
| Multicast | Frames sent to a specific group of devices (e.g., streaming video, routing protocol updates). |
| Unknown Unicast | Unicast frames for which the switch does not have a destination MAC address entry in its MAC address table. The switch must flood these out of all ports in the VLAN (like a broadcast). |
Thresholds and Measurement
The traffic limit that initiates the control action when it is exceeded is known as the threshold. One of three methods is commonly used to define this limit:
- Percentage of Interface Bandwidth: (e.g., 5% of the port’s speed).
- Bits Per Second (bps): (e.g., 10 Mbps).
- Packets Per Second (pps): (e.g., 500 pps).
Actions
When the incoming traffic for a monitored type exceeds the threshold, Storm Control performs a configured action:
- Drop (or Suppress): As soon as a packet of the designated traffic type surpasses the threshold, the switch starts dropping it. On many switches, this is the default action. When the rate falls below the threshold, traffic immediately resumes.
- Shutdown (or Err-Disable): To isolate the storm’s origin, the switch turns off the interface and places it in an err-disabled state. Re-enabling the port requires manual action (or an automated recovery timer).
You can also read What Is Root Guard In Networking? Root Guard Vs BPDU Guard
Mitigation Actions
The switch performs a specified action when the monitored traffic over the configured threshold:
- Drop/Suppress (Default Action): When packets surpass the threshold, the switch starts dropping or suppressing them right away. When no additional action is given, this is frequently the default. After the rate falls below the threshold, traffic forwarding starts up again.
- Shutdown: The switch shuts down the interface, placing it into an err-disabled state, effectively isolating the source of the storm. This typically requires manual intervention or an automatic recovery timer (such as the
recovery-timeoutstatement in Junos) to re-enable the port.
- SNMP Trap: The switch sends a Simple Network Management Protocol (SNMP) trap to notify administrators of the event. If the action is configured as
trap, the exceeding traffic will still be dropped; the trap is an “extra” action performed alongside the packet drop.
Vendor Specifics and Configuration
Storm control configuration is specific to the Layer 2 physical interfaces and port-channels, and generally applies only to ingress traffic.
| Vendor/Platform | Default Status | Default Threshold | Notes |
|---|---|---|---|
| Cisco | Disabled by default on some platforms (e.g., ASR 903 router). | N/A (requires configuration) | Configuration example uses storm-control broadcast level 30 (30% of bandwidth). The default action is to drop traffic. |
| Juniper (Junos ELS) | Enabled by default. | 80% of available bandwidth. | Configuration can be set using bandwidth-level (in Kbps) or percentage. |
| Juniper (Junos non-ELS) | Disabled by default. | 80% of available bandwidth (if enabled). | Storm control is applied in aggregate per port (broadcast, unknown unicast, and multicast streams are summed) on most switches. |
Example Cisco Configuration
One per-interface functionality is Storm Control. In the setup below, the multicast traffic limit is set to 5000 kbps (5 Mbps) and the broadcast traffic limit is set to 10% of the interface bandwidth. If the broadcast limit is exceeded, the port will be closed.
Switch# configure terminal
Switch(config)# interface GigabitEthernet 0/1
! 1. Set Broadcast threshold to 10% of port bandwidth
Switch(config-if)# storm-control broadcast level 10.00
! 2. Set Multicast threshold to 5000 kbps (5 Mbps)
Switch(config-if)# storm-control multicast level bps 5000k
! 3. Configure the action to shut down the port if the threshold is exceeded
Switch(config-if)# storm-control action shutdown
Switch(config-if)# endYou can also read What is DHCP Snooping and How DHCP Snooping Works
