What is Port Security?
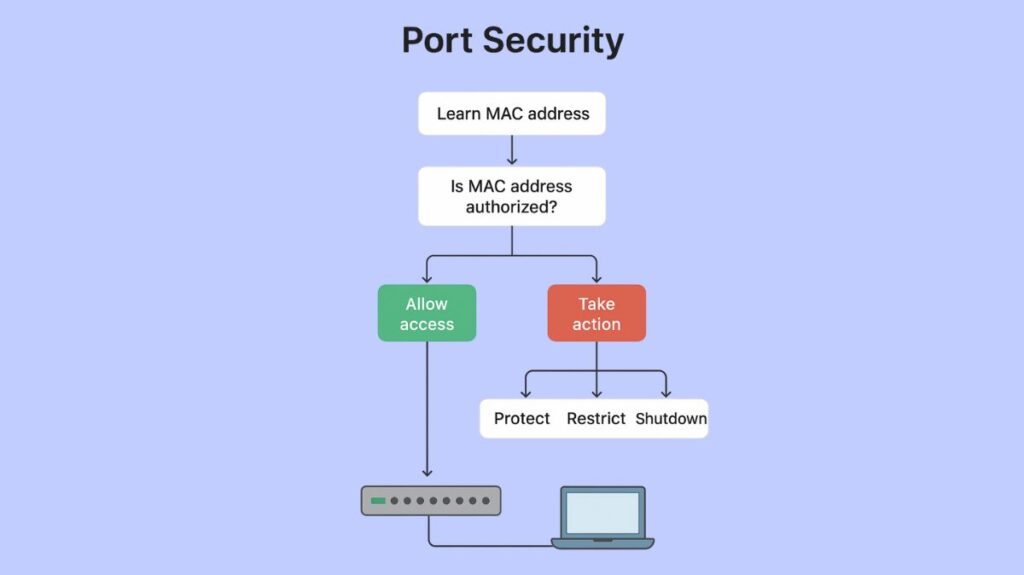
By restricting access to a switch’s physical ports and enabling only authorized devices to send data, port security is a networking feature that improves network safety. This is accomplished by binding certain MAC addresses to ports, which improves network integrity and privacy overall and stops MAC flooding attacks and unwanted access.
A crucial Layer 2 security feature, port security is mostly utilized on network switches (like Cisco switches) to restrict access to physical ports and lessen access layer vulnerabilities.
Limiting which devices can utilize particular interfaces is the main purpose of port security, which ensures that only devices with permission can send data. By doing this, the likelihood of an attacker connecting an unauthorized device (such as a laptop, hub, or access point) to a switch port to obtain network access is greatly decreased.
You can also read What Is Network Security & Why Network Security is Important
Key Concepts
- MAC address: A network interface controller’s (NIC) MAC address is a distinct hardware identification.
- Managed Switch: A managed switch is a network switch that enables port security and other feature configuration.
- Layer 2 Feature: Port security deals with MAC addresses rather than IP addresses and functions at Layer 2 (the data link layer) of the OSI model.
How it Works?
The source MAC address of Ethernet frames entering the switch interface is used by port security to identify devices. Important ideas include:
- MAC Address Filtering and Limiting: Port security works by either assigning a maximum number of distinct source MAC addresses that can be used on a port or by binding particular MAC addresses to ports.
- The maximum number of permitted MAC addresses is one by default when port security is enabled on an interface.
- The maximum MAC address count for voice ports that connect a PC and an IP phone should normally be set to two or more.
- Per-Port Configuration: Every port needs to have its security turned on and set up separately.
- Port Modes: The interface needs to be set up as either a trunk port or a static access port in order to configure port security. There is no support for dynamic modes.
Methods for Defining Secure MAC Addresses
Port security supports different ways to define the allowed MAC addresses, known as “secure MAC addresses”:
| Method | Description | Configuration Command |
|---|---|---|
| Static Secure | MAC addresses are manually predefined by the administrator. They are stored in the MAC address table and the switch configuration. | switchport port-security mac-address *mac-address* |
| Dynamic Secure | MAC addresses are learned dynamically. If port security is enabled, the port will dynamically learn and secure one MAC address by default. | This relies on the default configuration and does not require explicit MAC definition commands. |
| Sticky Secure | A compromise approach where the switch dynamically learns the MAC addresses and then automatically adds them to the running configuration file as secure MAC addresses (switchport port-security mac-address *address*). This reduces administrative effort but ensures the learned addresses are retained if the switch reboots (if the running config is saved to startup config). | switchport port-security mac-address sticky |
By default, when port security is enabled on an interface, the maximum number of allowed MAC addresses is one.
You can also read Extended Access Control List And Standard Vs Extended ACL
Security Violation
There are two primary situations in which port security is violated:
- When the total number of permitted MAC addresses surpasses the specified maximum due to a frame arriving with a new source MAC address.
- A MAC move violation occurs when a MAC address that has been learnt or configured on one secure interface is found on another secure interface that is part of the same Virtual Local Area Network.
The switch performs a predetermined action in response to a violation. The offending traffic is discarded by all three primary violation mechanisms.
Let’s discuss these violation modes:
- protect: Until you eliminate enough secure MAC addresses to bring the value down below the maximum, this mode discards packets with unknown source MAC addresses.
- Restrict: This mode does the same thing as protecting, which is to drop packets until enough secure MAC addresses are eliminated for the value to fall below the upper limit. Additionally, it will issue an SNMP trap, increase the counter value, and generate a log message.
- shut down: This mode is generally chosen above others since it instantly closes the port in the event that unauthorized access is made. In addition, it will issue an SNMP trap, increase the counter value, and create a log. Until the administrator executes the “no shutdown” command, this port will stay in a shutdown state.
- Sticky: This mode isn’t a violation. The user can provide static MAC address security without entering the absolute MAC address by using the sticky command. For instance, the first two MAC addresses discovered on that port will be added to the running configuration if the user specifies a maximum limit of two. If the third user wishes to access the MAC address after the second has been learnt, the proper action will be taken based on the violation method that was used.
- Err-Disabled Recovery: When a port enters the err-disabled state due to a security violation, it remains disabled until manually restored. Alternatively, the switch can be configured for automatic recovery using the global commands
errdisable recovery cause psecure-violationanderrdisable recovery interval seconds.
Note: Only access ports will be affected by port security; therefore, in order to activate port security, the user must first make the port an access port.
Configuration Steps
To configure port security on a switch interface, several steps are generally followed:
- Set the Port Mode: The port must be configured as a static access port or a trunk port. Dynamic modes are not supported.
- Command:
switchport mode accessorswitchport mode trunk.
- Command:
- Enable Port Security:
- Command:
switchport port-security.
- Command:
- (Optional) Set Maximum Addresses: Override the default (1) if needed.
- Command:
switchport port-security maximum *number*.
- Command:
- (Optional) Set Violation Action: Override the default action (
shutdown).- Command:
switchport port-security violation {protect | restrict | shutdown}.
- Command:
- (Optional) Define MAC Addresses: Use
switchport port-security mac-address *mac-address*for static definition orswitchport port-security mac-address stickyfor sticky learning.
Note on Voice Ports: For voice ports connected to an IP phone and a PC, the maximum MAC address count should be set to at least two (one for the phone, one for the PC).
MAC Address Aging
Port security supports secure MAC address aging, which manages how long learned addresses remain secured. This applies mainly to dynamically learned addresses:
- Absolute: Regardless of activity, secure addresses are erased after a predetermined amount of time.
- Inactivity: Only after being inactive for the designated amount of time are secure addresses removed.
The default aging time is 0 minutes, and the default aging type is absolute. Static secure addresses and sticky secure addresses do not age out by default.
Benefits of Port Security
- Prevents Unauthorized Access: It prevents rogue or unfamiliar devices from establishing a connection and transmitting information.
- Mitigates Attacks: It aids in preventing MAC flooding attacks, in which a hacker sends a large number of phoney MAC addresses to overload a switch.
- Enhances Network Integrity: Port security contributes to the preservation of network privacy and integrity by limiting access.
- Controls Device Access: It makes sure that only particular, authorized devices can communicate via a particular port.
You can also read How Organization Based Access Control OrBAC Works?
