The following topics were covered in this blog: Intrusion Prevention System (IPS) types, advantages of intrusion prevention system, and How an IPS Works. We also discussed core functionality and how an IPS Differs from IDS.
Intrusion prevention system (IPS)
A network security instrument called an intrusion prevention system (IPS) keeps an eye out for malicious activities in network traffic and automatically stops attacks by blocking or discarding unwanted traffic, notifying administrators, or cutting off connections. An IPS makes security teams more proactive and allows them to enforce security policies by acting to block threats, in contrast to intrusion detection systems (IDS), which just identify and report threats.
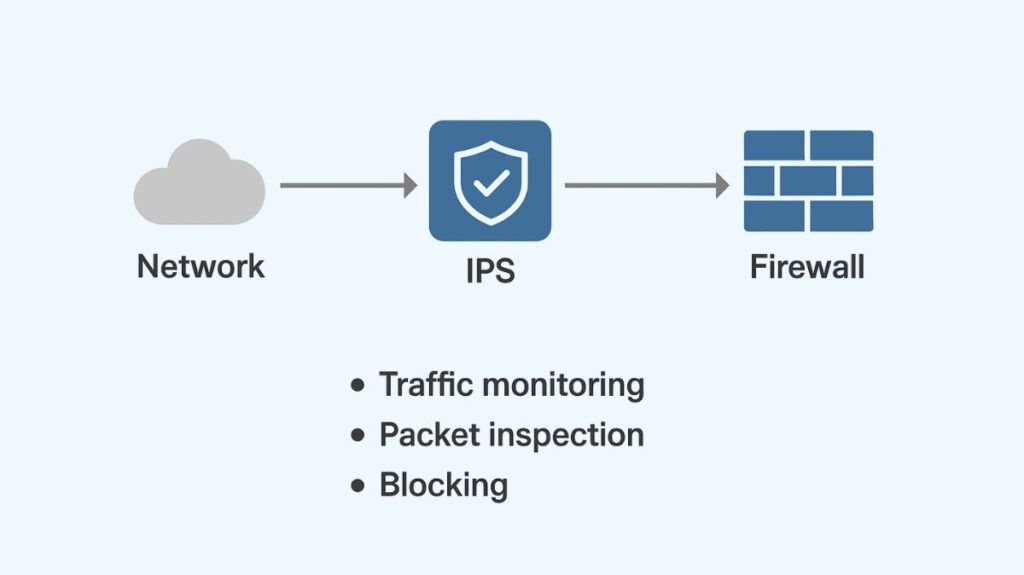
Core Functionality and Differentiation from IDS
Since both systems monitor network traffic for malicious activity, an intrusion prevention system (IPS) is frequently seen as an extension or enhancement of an intrusion detection system (IDS). But they have quite different responsibilities and capacities:
Active preventive versus Passive Detection: IPS’s proactive preventive capabilities is indicated by the “P” in the acronym. An IPS is an active security tool that also performs automated measures to stop or lessen attacks in real-time, in contrast to an IDS, which is a passive system that merely detects threats, monitors traffic, and sends administrators alerts.
Inline Deployment: Network location is a crucial factor. Inline deployment places an intrusion prevention system (IPS) directly in the path of network traffic, usually directly behind a firewall. The IPS may examine each packet that passes through in this place and stop any suspicious activity before it has a chance to do any damage. An IDS, on the other hand, is usually set up “off-line” or out-of-band.
Also Read About What Is Reflection Attack? How To Prevent Reflection Attack
How an IPS Works?
In order to function, an intrusion prevention system continuously examines network traffic in real-time, comparing it to both known and undiscovered attack patterns. There are multiple levels of analysis involved in the process:
Traffic Preprocessing and Deep Inspection
The IPS arranges the raw data prior to packet inspection:
- To stop attackers from hiding risks with encoding methods, it normalizes traffic formats.
- To make sure no information is overlooked during inspection, it puts broken packets back together.
- The system carries out Deep Packet Inspection (DPI), which examines the technical structure and intent of the traffic in addition to headers. The Network, Transport, and Application layers are examined in detail in this examination.
Detection Mechanisms
After unpacking, the IPS employs a number of methods to identify malicious traffic:
Signature-Based Detection: This technique compares traffic to an ever-growing database of recognized attack patterns, or signatures. Signatures specify particular values for header fields or code segments that are utilized by known attacks. Either vulnerability-facing signatures, which target the underlying weakness, or exploit-facing signatures, which identify the specific exploit attempt, can be used in this technique. The fact that it can only identify known attacks is a disadvantage.
Anomaly-Based Detection (Statistical Anomaly-Based Detection): The IPS creates a baseline of “normal” network traffic and then flags any activity that deviates noticeably from it. This technique is known as Anomaly-Based Detection (Statistical Anomaly-Based Detection). Although this technique frequently detects zero-day assaults (new, unidentified threats), it is prone to producing false positives in the event that legal but atypical traffic is misidentified.
Policy-Based Detection: This makes use of administrator-defined security policies. Any action that goes beyond these pre-established guidelines for example, preventing access by illegal users or banning particular file types is halted.
Behavior-Based Detection: This keeps an eye out over time for strange or suspicious activity, like repeatedly unsuccessful login attempts.
Advanced features like deep learning models can be used by contemporary systems, such Next-Generation IPS (NGIPS), to improve detections, precisely identify malicious traffic that has never been seen before, and block unknown Command-and-Control (C2) connections.
Also Read About Common Network Security Vulnerabilities And Exploitation
Prevention Actions
When the IPS detects a threat, it automatically and instantly takes action to stop the attack:
Blocking communication: This can entail stopping the malicious session or connection, deleting malicious packets, or blocking all further communication from the problematic source IP address.
Mitigation: By changing the content, for as by eliminating a malicious attachment while permitting the remaining traffic to pass through, the IPS can clean up the assault. For defense against known and undiscovered network-exploitable vulnerabilities, it can also apply a virtual patch.
System Correction: An IPS can alleviate TCP sequencing problems, defragment packet streams, and fix cyclic redundancy check (CRC) mistakes.
Logging and Alerting: The IPS logs the event or initiates an alert, frequently informing security administrators or a Security Information and Event Management (SIEM) tool of the incident.
Policy Enforcement: It can cause other security devices to take action or change firewall rules to stop future attacks.
Types of Intrusion Prevention Systems
The deployment location and monitoring focus of IPS technologies determine their classification:
- By examining protocol activity, the Network-based Intrusion Prevention System (NIPS) keeps an eye on the entire network for questionable activities. Usually, NIPS sensors are positioned at strategic network points, like the company perimeter.
- A software program called a host-based intrusion prevention system (HIPS) is installed on a single host, such as a server or PC, and it solely keeps an eye on the activities and traffic that take place on that particular computer. As a last line of protection against threats that have gotten past the network layer, HIPS functions best when used in conjunction with NIPS.
- The Wireless Intrusion Prevention System (WIPS) may automatically eliminate unwanted devices and suspicious traffic from wireless networks.
- Examining network traffic flows to find risks that produce odd patterns, including Distributed Denial of Service (DDoS) attacks or policy infractions, is the main goal of Network Behavior Analysis (NBA).
Advantages of intrusion prevention system
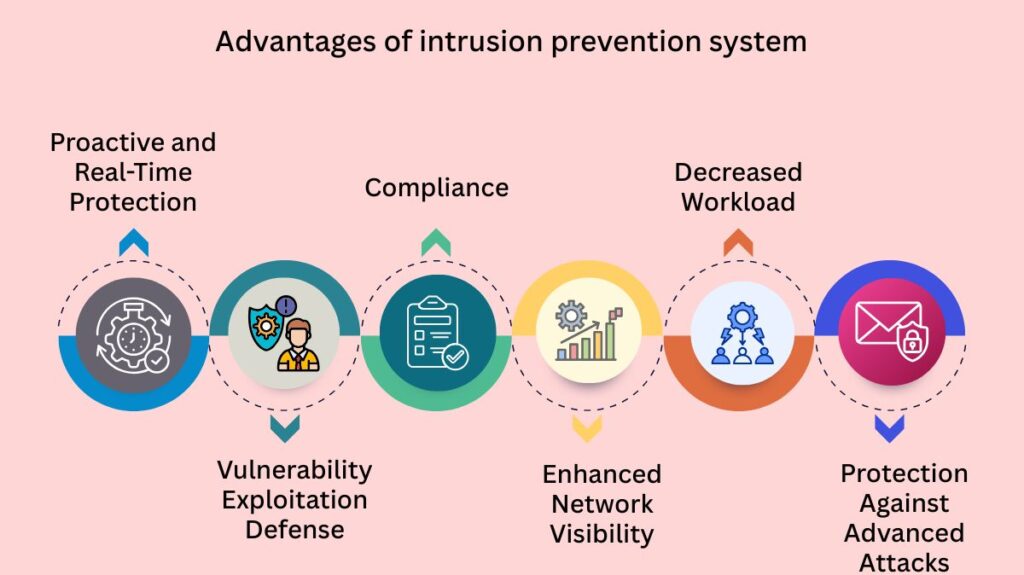
For strong network security, an intrusion prevention system is regarded as a necessary tool. Advantages consist of:
Proactive and Real-Time Protection: Intrusion Prevention Systems (IPS) proactively guard against known and new threats by identifying and blocking malicious traffic in real-time.
Vulnerability Exploitation Defense: In the time between a vulnerability’s discovery and the deployment of a security patch, intrusion prevention systems (IPS) are very good at identifying and stopping vulnerability exploits.
Compliance: By enforcing security standards and offering essential intrusion detection techniques, IPS assists enterprises in meeting security compliance requirements, such as those imposed by PCI-DSS.
Enhanced Network Visibility: IPS helps detect possible security threats by offering comprehensive insights into network activity.
Decreased Workload: By automating threat blocking, intrusion prevention systems (IPS) free up security personnel’ time to concentrate on more intricate problems.
Protection Against Advanced Attacks: IPS protects against a number of targeted attacks, such as OS fingerprinting, DDoS, buffer overflow, Address Resolution Protocol (ARP) spoofing, and SYN floods.
