In this article, we learn about what DHCP snooping is, how DHCP Snooping works, attacks mitigated by DHCP Snooping, and Configuration and Management Commands.
What is DHCP snooping?
A network switch security feature called DHCP snooping inhibits rogue DHCP servers from assigning IP addresses and launching denial-of-service (DoS) attacks by filtering DHCP signals on untrusted ports. In order to monitor valid IP-MAC address bindings and improve network security generally, it creates a “DHCP snooping database” or binding table that verifies DHCP traffic from clients connected to untrusted access ports.
One essential Layer 2 security feature that switches use to defend the network infrastructure against different Dynamic Host Configuration Protocol (DHCP) assaults is DHCP Snooping.
When DHCP communications pass within the same broadcast domain (VLAN), Layer 2 and multilayer switches are subject to DHCP snooping. It works similarly to an Access Control List (ACL) or firewall, evaluating incoming DHCP packets and using logic to determine whether to allow or reject them.
DHCP Snooping = DHCP traffic police.
It only allows real DHCP servers to reply, and blocks fake ones.
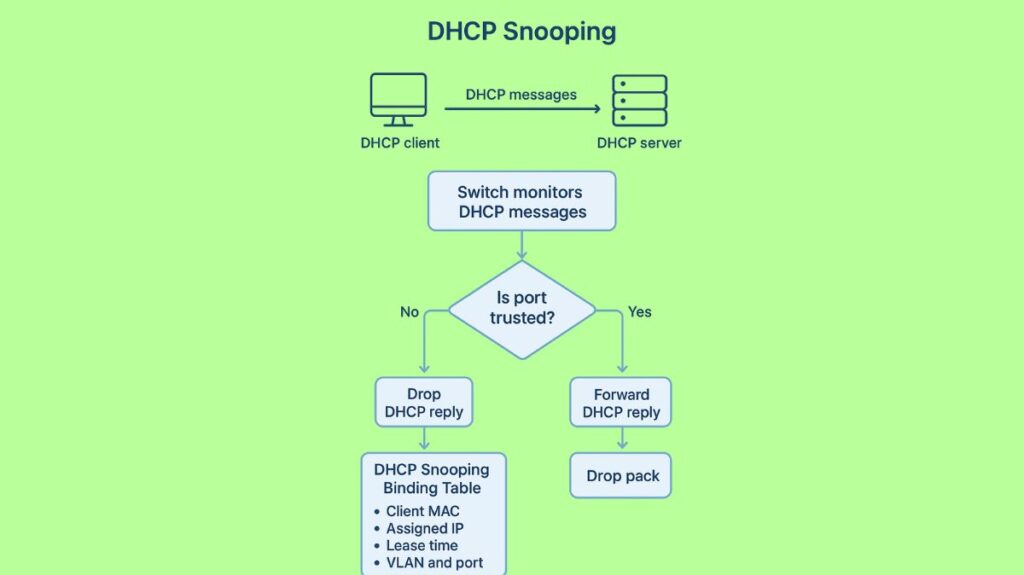
How DHCP Snooping Works
Classifying switch ports and keeping track of valid leases are the two main ideas that underpin DHCP Snooping’s operation.
Trusted and Untrusted Ports
DHCP Snooping divides switch ports into two simple categories: Trusted Ports and Untrusted Ports.
Trusted Ports:
- The authentic DHCP server or an uplink (an additional switch or router) leading to it is connected to these ports.
- They are permitted to transmit and receive all DHCP messages, including DHCPACK and DHCPOFFER, which are server response messages.
Untrusted Ports:
- Usually, these ports are linked to clients, or end-user devices.
- The only messages they can send are client request messages (such as DHCPDISCOVER and DHCPREQUEST).
- The switch instantly stops a rogue server by dropping any DHCP server response messages (DHCPOFFER, DHCPACK, and DHCPNACK) received on an untrusted port.
DHCP Message Filtering
Certain DHCP communication is monitored and filtered by the switch, especially on untrusted ports:
- Blocking Rogue Servers (Spoofing Mitigation): DHCP Snooping always drops DHCP server communications from DHCPOFFER, DHCPACK, and DHCPNAK that arrive on an untrusted port. This stops unauthorized (rogue) DHCP servers from distributing IP addresses.
- Stopping Starvation Attacks: DHCP Snooping drops DHCP messages where the Source MAC address of the Ethernet frame and the Client MAC address (
chaddr) in the DHCP message are not identical. This prevents attackers using spoofed source MAC addresses in DHCP DISCOVER/REQUEST messages from rapidly depleting the DHCP pool.
- Relay Agent/Option 82 Filtering: DHCP packets transmitted to an untrusted port by a DHCP relay agent will be dropped by the switch if they contain Option 82 information. This is known as relay agent/option 82 filtering.
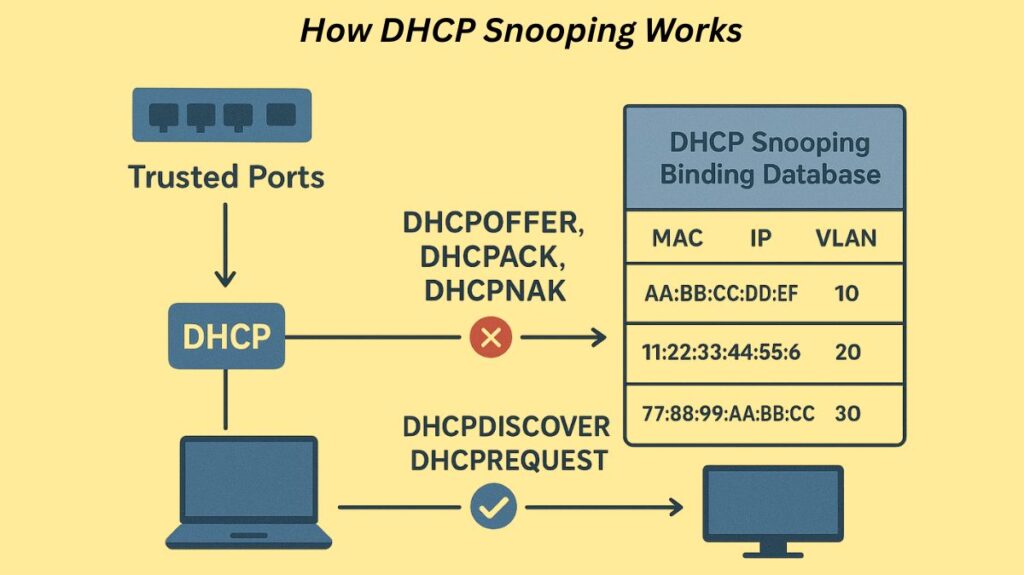
The DHCP Snooping Binding Database
DHCP Snooping creates a DHCP Snooping Binding Database (or binding table) dynamically when it is activated. This database tracks genuine IP addresses leased to hosts connected to untrusted ports.
When the switch receives a DHCPACK message from the trusted DHCP server acknowledging an IP assignment to an untrusted host, it automatically generates an entry. Each entry documents the following important data:
- MAC address of the untrusted host.
- Leased IP address of the untrusted host.
- VLAN number and the associated interface (switch port).
- Lease time.
Because it is used by other Layer 2/3 security features, such as IP Source Guard and Dynamic ARP Inspection (DAI), to protect against ARP Poisoning and ARP Spoofing attacks and to maintain IP integrity, this binding table is crucial.
Attacks Mitigated by DHCP Snooping
DHCP Snooping is designed to mitigate several major network threats:
| Attack | Description | Mitigation by DHCP Snooping |
| Rogue DHCP Server (DHCP Spoofing) | An attacker sets up an unauthorized DHCP server to distribute incorrect IP information (like a malicious default gateway or DNS server) to clients. | Blocks DHCPOFFER/DHCPACK messages from untrusted ports, ensuring clients only receive valid responses from the trusted server. |
| Man-in-the-Middle (MITM) Attack | By acting as a rogue DHCP server, the attacker can set their own device as the client’s default gateway, allowing them to intercept and manipulate all the client’s traffic. | By blocking rogue DHCP servers, it prevents the attacker from gaining a crucial position to launch a subsequent MITM attack (often combined with Dynamic ARP Inspection for full protection). |
| DHCP Starvation Attack | An attacker floods the network with DHCPDISCOVER messages using spoofed MAC addresses, quickly exhausting the DHCP server’s pool of available IP addresses. | Can be combined with rate limiting to restrict the number of DHCP messages allowed per untrusted port, preventing a single device from overwhelming the DHCP server. |
| IP Address Spoofing | A malicious client attempts to use an IP address that was not legitimately assigned to it. | The DHCP Binding Table allows the switch (when integrated with IP Source Guard) to verify that a device’s traffic is only sent with the IP address it was actually assigned. |
Configuration and Management Commands
To enable and configure DHCP Snooping on a switch, several commands are typically used.
Required Global Configuration:
- To enable DHCP Snooping globally:
ip dhcp snooping. - To list the Virtual Local Area Networks on which to enable DHCP Snooping:
ip dhcp snooping vlan vlan-list. Both commands are required for the feature to operate.
Interface Configuration (Trusted Ports):
- To configure a port as trusted (overriding the default untrusted state):
ip dhcp snooping trust.
Optional Configuration/Mitigation:
- Option 82: If a Layer 2 switch using DHCP Snooping is not also acting as a DHCP relay agent, you should disable the insertion of DHCP Option 82 header fields using the global command
no ip dhcp snooping information option. If this is not done, the default setting (which assumes the switch is a relay agent) can cause DHCP to fail for end users because the message changes cause DHCP servers to ignore the request.
- Rate Limiting: To prevent DoS attacks that flood the switch CPU with DHCP messages, rate limiting can be applied on interfaces.
- To set a limit (in messages per second):
ip dhcp snooping limit rate number(interface subcommand). - If the rate limit is exceeded, the port enters an err-disabled state. Automatic recovery can be configured using
errdisable recovery cause dhcp-rate-limit.
- To set a limit (in messages per second):
Verification Commands:
show ip dhcp snooping statistics: Lists counters regarding DHCP Snooping behavior on the switch.
show ip dhcp snooping: Displays a variety of configuration settings, status, and interface trust/rate details.
show ip dhcp snooping binding: Displays the contents of the dynamically created DHCP Snooping binding table.
You can also read What is uRPF Unicast Reverse Path Forwarding & How it Works
