EAP-TLS
Extensible Authentication Protocol–Transport Layer Security, or EAP-TLS, is a sophisticated and reliable authentication system that is frequently used in settings where security is crucial, like VPNs and secure business Wi-Fi networks (using 802.1X).
It is widely regarded as the EAP framework’s strongest authentication method.
EAP-TLS Meaning
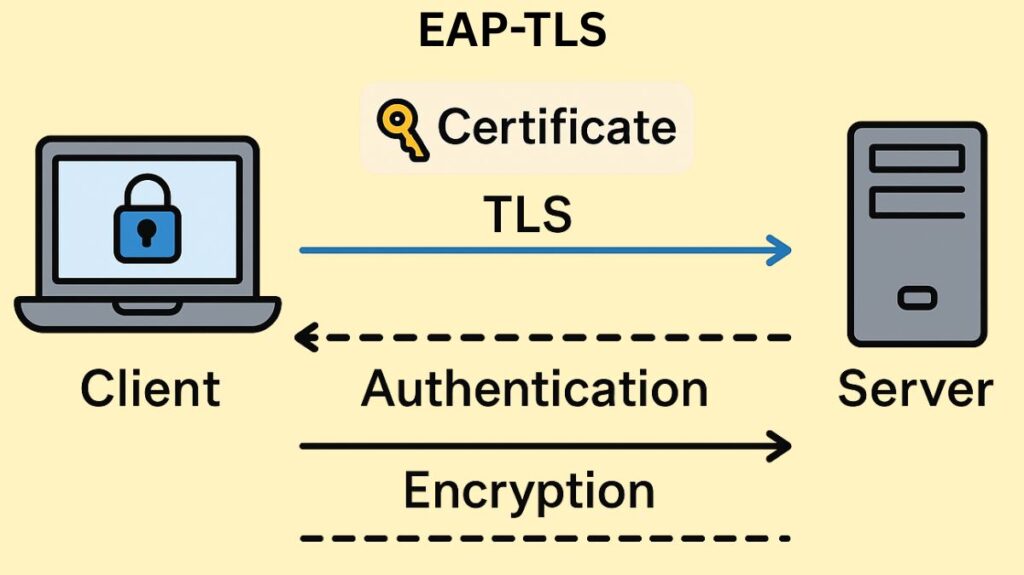
EAP-TLS is an authentication framework that uses digital certificates to verify the identity of both the client and the server.
- Basis in TLS: EAP-TLS takes advantage of the Transport Layer Security (TLS) protocol, which is the same technology that secures financial transactions and communications across HTTPS websites.
- Mutual Authentication: EAP-TLS’s primary characteristic is that it requires dual, mutual authentication using digital certificates. Identity verification is required for both the client and the server. This stops common dangers, including connections to unauthorized access points and man-in-the-middle (MITM) attacks.
- Passwordless: By relying solely on certificates securely kept digital files instead of user-entered passwords, authentication removes the possibility of credential theft or selecting weak passwords.
How EAP TLS Works (Key Steps)
The authentication process centers around the exchange and verification of certificates:
- Identification: The connection request is started by the client device.
- Server Authentication: The client is shown the TLS certificate of the authentication server, which is usually a RADIUS server. The client attests to the validity of the certificate and its issuance by a reliable Certificate Authority (CA). Users are kept from connecting to a harmful rogue access point by taking this step.
- Client Authentication: Client authentication involves the client device presenting the server with its own digital certificate, usually an X.509 certificate. The server confirms that the client’s certificate is legitimate and hasn’t been revoked.
- Secure Tunnel: A secure encrypted TLS tunnel is created if both certificates are correctly validated. A symmetric, secret session key is negotiated by the server and client using asymmetric key exchange. All ensuing session data exchanged within the secure tunnel is thereafter encrypted using this session key.
You can also read EAP and How Does Extensible Authentication Protocol Work?
Requirements and Implementation Complexity
Implementing EAP-TLS might be challenging, despite its high level of security. An organization needs to set up and maintain a Public Key Infrastructure (PKI) to use this protocol.
To issue, maintain, and revoke digital certificates for the server and each client device, an enterprise-wide system known as a PKI is necessary.
The necessary components include:
- An access point.
- A RADIUS server (e.g., FreeRADIUS or Cisco ISE).
- A functioning PKI infrastructure (Certificate Authority).
- A valid Server certificate issued to the authentication server.
- Client certificates installed on every device that needs access to the network.
Managing the issuance, distribution, and renewal of certificates for each client device can be costly if external CA services are used, and it can be administratively taxing, especially in large organizations.
You can also read What is MSCHAPv2, How it Works & MSCHAPv2 Key Features
Advantages
EAP-TLS offers several distinct advantages, primarily centered on security and user experience (post-setup):
| Advantage | Description |
|---|---|
| Maximum Security | Uses mature, well-tested cryptography (TLS) and is resistant to attacks like password guessing, phishing, and replay attacks. It is widely accepted as the most secure authentication technique. |
| Mutual Authentication | Both client and server authenticate each other via certificates, making over-the-air attacks virtually impossible. |
| Passwordless | Authentication relies on certificates, which enhances the end-user experience by allowing automatic connection without repeated password entry. |
| Device Visibility | Certificates are tied to specific devices, which boosts network visibility and allows issues to be traced back to the exact device. |
EAP-TLS is the gold standard for secure environments, including:
- Secure Enterprise Networks (802.1X): Used for Wi-Fi (WPA2/WPA3-Enterprise) and wired access in corporations, universities, and government agencies.
- VPN Authentication: Used for authenticating VPN clients in a client-to-site configuration.
- Zero-Trust Environments.
- IoT Device Authentication.
Disadvantages
- Deployment Complexity: To issue, manage, and revoke certificates for both the client and server sides, a strong Public Key Infrastructure (PKI) is necessary.
- Certificate Management: It can be administratively taxing to issue, distribute, and renew certificates for each client device, particularly in large organizations.
- Possible Cost: It might be necessary to maintain a sophisticated internal PKI or buy services from a Certificate Authority (CA).
Consider attending a highly secure corporate meeting to get a sense of the intricacy of EAP-TLS. Before being permitted to whisper private information (the encryption keys) over a secure phone line (the TLS tunnel), each participant, host server, and client device must present a distinct, validated government ID (the digital certificate) to establish their identity. It is quite safe because of this strict dual-verification procedure, but issuing and managing all those IDs takes a lot of organizational work (the PKI).
You can also read What is Password Authentication Protocol PAP & How it Works
