This blog post covered a number of topics, including the Address Resolution Protocol (ARP), how does address resolution protocol work, its Purpose and context, its table and cache, its variations, IPv6 and ARP, security, and contemporary alternatives.
Address Resolution Protocol (ARP)
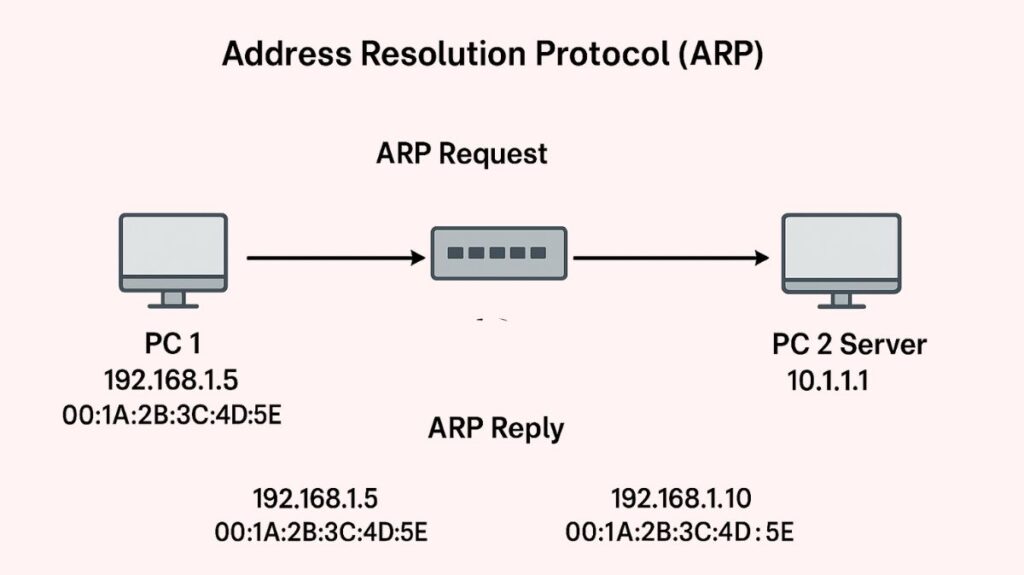
An essential Internet protocol called Address Resolution Protocol (ARP) maps a known IP address to its matching hardware address (MAC address), mostly in IPv4 networks. This procedure is necessary because data lines (Layer 2), like Ethernet, need physical addresses (MAC addresses) for local communication, whereas network layer (Layer 3) protocols, like IP, handle routing based on logical addresses. RFC 826 provides a definition of ARP.
An IP host or router linked to a local area network (LAN) can have its data-link address dynamically learnt using ARP.
Purpose and Context
Address Mapping: The primary function of ARP is to translate a dynamic Internet Protocol (IP) address to a fixed Media Access Control (MAC) address a physical machine address within a local area network (LAN).
Logical vs. Physical Addresses: While data transmission over channels such as Ethernet necessitates physical MAC addresses (Layer 2), devices on a network utilise IP addresses (Layer 3) for logical identification.
Address Lengths: Because MAC and IP addresses differ in length a MAC address is 48 bits long, whereas the commonly used IPv4 address is 32 bits long, translation becomes necessary. ARP facilitates the conversion of 32-bit addresses to 48-bit addresses and vice versa.
Layering: According to the OSI model, ARP acts as a link between the Network Layer (Layer 3, IP) and the Data Link Layer (Layer 2, MAC). It is never routed and is transmitted inside the confines of a single subnetwork.
How does address resolution protocol work?
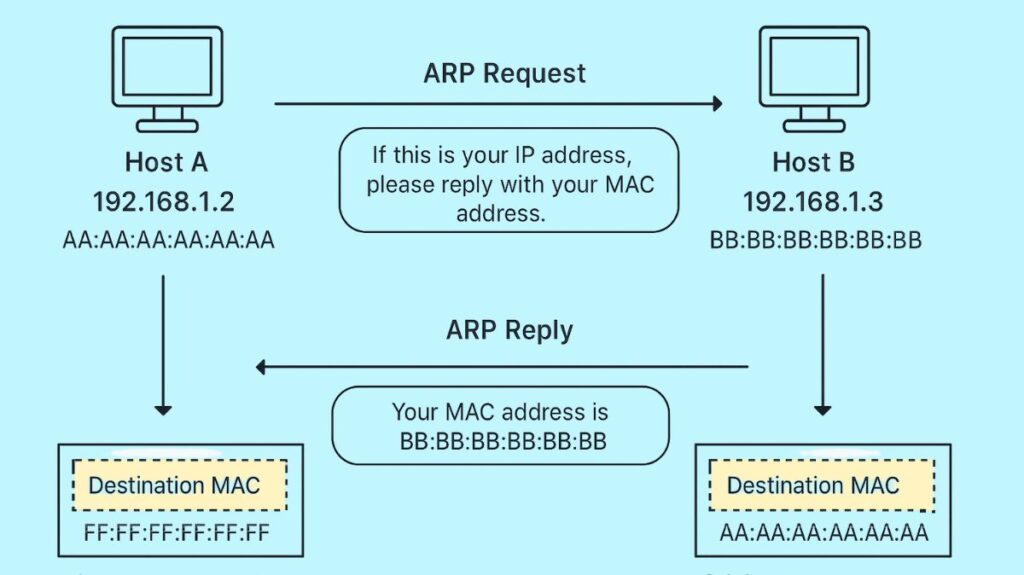
When a device (Host A) needs to determine the MAC address of a target device (Host B) but knows its IP address, it uses the standard ARP protocol, which is a request-reply method.
Trigger: A host or router examines its internal cache when it wants to deliver an IP packet but is unsure of the destination MAC address for the subsequent hop, which might be the default router or another host. ARP is started if the MAC address is unknown.
ARP Request: The message “If this is your IP address, please reply with your MAC address” is created by the sender.
- The message is transmitted as a Layer 2 broadcast, which means that the broadcast address all Fs in hexadecimal: FF-FF-FF-FF-FF is the destination MAC address of the Ethernet frame.
- The ARP request lists an all-zero target hardware address but includes the known target IP address. This broadcast is received and processed by every device on the local area network.
ARP Reply: An ARP Reply message is returned by the host that matches the target IP address.
- The MAC address of the host is revealed in the response.
- Usually, the requester receives this response directly as a unicast frame.
- ARP packets contain fields for both the destination IP and hardware addresses and the origin IP and hardware (MAC) addresses. The receiver can obtain the sender device’s addresses by looking at the origin fields.
ARP Table and Cache
In order to save the outcomes of address resolution, both hosts and routers keep an ARP table (also known as an ARP cache) in memory. This table lists the IP addresses of neighbours on the same VLAN together with their matching MAC addresses.
- When a device needs to wrap an IP packet in an Ethernet frame, it first checks the ARP cache.
- It is possible to configure ARP entries statically or dynamically (via the ARP process).
- Frequent users may still occasionally get ARP queries even if cache entries are intended to time out regularly to clear the table.
- On the majority of operating systems, users can use the arp -a command to inspect the ARP cache.
ARP Variations
Proxy ARP
Even if hosts on one subnet don’t have a defined default gateway or particular routing information, they can nevertheless connect with hosts on other subnets thanks to proxy ARP.
- When the target IP address is not on the subnet that is linked to the receiving interface, an ARP request is received by a router that has Proxy ARP enabled.
- The router responds with an ARP Reply including its own interface MAC address if it has a route to the distant destination.
- Believing the destination to be local, the originating host subsequently forwards future packets for the distant destination to the router’s MAC address.
- Cisco routers frequently have Proxy ARP set up by default.
Also Read About What is Dynamic ARP Inspection, How it Works & Configuration
Gratuitous ARP (GARP)
An unsolicited ARP reply sent without a prior ARP request is known as a gratuitous ARP message.
Purpose: The goal is to ensure that every host on the local subnet receives GARP and updates their ARP caches by sending it to the Ethernet destination broadcast address. When a host modifies its MAC address, this is occasionally used in a valid way. It is also utilised during the DHCP process when a client broadcasts an ARP message for its freshly assigned address in an effort to prevent a duplicate IP address.
Security Risk: Man-in-the-middle attacks can be made possible by attackers sending a gratuitous ARP with a spoof MAC address, which causes hosts or switches to update their tables incorrectly.
Mitigation: To stop these attacks, a Layer 2 security feature called Dynamic ARP Inspection (DAI) verifies ARP packets (requests and answers) against a DHCP Snooping binding table.
Reverse ARP (RARP)
An previous Internet protocol called RARP was created to map a known hardware address (MAC) to its associated IP address, doing the opposite of what ARP does. Usually, diskless computers that needed to find their IP address from a RARP server but knew their MAC address used it. DHCP has mainly taken the position of RARP.
Inverse ARP (IARP)
A known Data Link Connection Identifier (DLCI), which is a Layer 2 address, can be mapped to a Layer 3 protocol address (like IP) on Frame Relay networks using the Inverse ARP technique.
IPv6 and ARP
In IPv6, the Neighbour Discovery Protocol (NDP) takes the position of the IPv4 Address Resolution Protocol (ARP) function. NDP is included in ICMPv6.
Among the many essential tasks carried out by NDP is Neighbour MAC Discovery, which substitutes ARP with a pair of matching messages:
- A host uses neighbour solicitation (NS) to ask for the MAC address of a neighbour. The solicited-node multicast address receives the NS message.
- The target device’s MAC address is included in the Neighbour Advertisement (NA), which is sent in response to an NS message.
Also Read About What is Dynamic Trunking Protocol DTP Spoofing Overview
Security and Modern Alternatives
ARP has many disadvantages even if it is essential for communication:
- Security Vulnerabilities: ARP is intrinsically vulnerable due to its lack of authentication or verification procedures.
- ARP Spoofing/Poisoning: This type of cyberattack involves sending forged ARP messages to other hosts’ ARP caches in order to associate their own MAC address with the IP address of a legitimate device (such as the default gateway). Man-in-the-Middle (MITM) attacks are made possible by this, which reroutes traffic and gives the attacker the ability to intercept and steal private information.
- Network Congestion: Because ARP depends on broadcast messages, there may be an increase in broadcast traffic on big networks, which can create congestion and poor performance.
By using static ARP entries (fixed IP-to-MAC address mappings) and turning on Dynamic ARP Inspection (DAI) on switches to verify ARP packets, administrators can reduce the risks associated with key devices.
The Neighbour Discovery Protocol (NDP) takes the place of ARP in Internet Protocol Version 6 (IPv6) networks. Using Neighbour Solicitation (NS) and Neighbour Advertisement (NA) messages, NDP offers more extensive features, such as neighbour MAC finding.
